 "Crypt" means "encrypt" and "graphy" means "writing". Cryptography is the study of writing the code in an encrypted form.
"Crypt" means "encrypt" and "graphy" means "writing". Cryptography is the study of writing the code in an encrypted form. Security in Computer Networking
Consider the today's scenario of Internet where , there are more than 2 billion Internet users throughout the Globe.
People interacting with each other, exchanging mails, purchasing items
online and many other activities are being done over Internet online.
Thus there is a great need of securing the data of the users from the
bad commodity or person, or we can say this bad person as an Intruder.
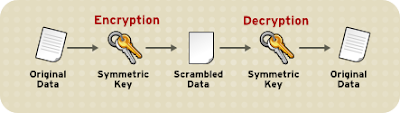

Suppose there are 2 persons , James and Steve. They want to communicate over Internet. Lets consider a scenario, what can be there basic needs when they communicate.
First of all, they both surely wanted that the data they are
exchanging, must not be read by any third person, it should be between
them only.
Secondly, while transmitting the data, the message should not be
deleted, or modified. It should reach the destination in its original
form.
Thirdly, they both wants to verify that the person they are
communicating , is the legal person, with whom they wants to
communicate. Steve wants to make sure that the person on other side is
James only, and James wants to make sure, that he is communicating with
Steve only.
Taking these 3 scenarios, we can say that there are some basic needs of the communicating parties. These are :
1. Confidentiality :
The term confidentiality means that the meaning of the data must be
understood by the sender and the intended receiver only. As an Intruder
can steal the data during its transmission. Thus the message must be
encrypted, so the Intruder is unable to understand the message.
2. Integrity :
James and Steve wants to ensure that the data is not altered during
its transmission neither by an Intruder, nor accidentally. In Transport
Layer and Network Layer, we have checksum for error in the message. But
prior to that, Data Integrity is used for this purpose.
3. Authentication :
In real world, when you meet a person and talks to him, you both just
tell your name to each other, in order to verify each other identity.
But when you are communicating over Internet, and you cannot see the
other party, its very difficult to authenticate the identity of that
person. Thus Authentication includes verifying the identity of the
person to each other over Communication Medium.
4. Organisation Security :
As you must be aware, that now a days ,
almost every organisation's network is connected to the outer world
Internet. Thus an Intruder can get access of the Organisation Network,
he can deposit harmful malwares or worms in the end systems of the
organisation network, can access secret information of the organisation.
To secure organisation from such attacks, we have Firewalls and
Intrusion detection System in Computer Networks which we will cover in
our later posts.
Now lets have a look at what an Intruder can do and how it can harm the
network. Suppose James and Steve are communicating and they want to
ensure confidentiality, Data Integrity and Authentication. Now what
different things an Intruder can do.
i) Record the messages on the channel.
ii) Delete or Modify the original message during its transmission.
iii) Impersonating himself as someone else.
If proper measures are not taken, then an Intruder can attack in a
numerous number of ways. For example, if not properly encrypted, an
Intruder can steal your username and Password. He can do Denial of
Service ( DoS ) attack by overloading the network resources and
disabling other Network users to communicate. There are various other
attacks also. We will discuss each and there measure in detail , later
in this post and in the coming post.
Till now you must have understsood that there is a great need of
securing our data while transferring it over Communication medium. There
are various techniques to safeguard our data, these are known as Cryptography Techniques.
Cryptographic techniques are so much much developed in past 30-40 years,
that they themselves include Confidentiality, Integrity and
Authentication. So there is no need of applying for different security
algorithms to provide all these services individually.
Cryptography allows a sender to be-fool an Intruder by encrypting the
message in some other format using certain technique or algorithm. The
Intruder can be disguised, that he cannot get any information from the
data, if he is able to intercept it. Yes , the authenticated receiver
will be able to receive the original data from the disguised data.
Let us suppose , James and Steve wants to communicate. James wants to
send a message to Steve. For example: James wants to ask "How are you
Steve". Thus James message in original form is known as Plain text. James will use an encryption algorithm to encrypt his original message, to save it from the intruder attack. The encrypted message is known as Cipher Text. Cipher Text is not understandable by the intruder.
But as you know, in today's global world, almost all the encryption and
decryption algorithms are open to every person on the Internet. Even
intruder knows these algorithms.So if intruder knows the encryption
method, he could have easily decrypt the message. But still something is
there, that is preventing the intruder to decrypt and extract the
transmitted message, that is known as key.
A key can be anything like a string of characters or numbers etc. Say in this case, the encryption algorithm takes key A, message m as input and produces the cipher text as output. The cipher text here will be denoted as A(m).
Cipher Text ( C ) = A(m)
This means that the plain text, m is encrypted using a key A.
On the receiving side, Steve will provide a key B and the cipher text
to the decryption algorithm, that will generate the plain text.
Plain Text (m) = B (C)
or
we can also write it as , Plain Text (m) = B(A(m))
There are two types of encryption Algorithms.
i) Symmetric Key Algorithm :
In these algorithms, both sender and receiver have the identical keys. They share it with each other secretly.
ii) Public Key Algorithm :
In these types of algorithms, sender and receiver make use of a pair of
keys. One of the keys is known to both sender and receiver and infact to
the rest of the world, and the other key is known only to one , either
sender or receiver, but not to both.
Let us start with our discussion over different encryption Algorithm.
First we will be going through Symmetric Key Algorithms and then moving
on to various public key encryption techniques.
Symmetric Key Algorithm in Cryptography
Till now what have you understand about Cryptography. It must be that
Cryptography is just putting one thing in place of the other using
certain techniques so that it should not be understood by any wrong
person. So we shall now look at various symmetric algorithms that are
almost 500 years old or more. For Symmetric Key cryptography algorithms ,
we will use key as K.
1. Caesar Cipher :
For example : James wants to send a message to Steve,
"James, Meet me at University, Steve".
Caesar Cipher will replace the every alphabet by its K letter
later in the alphabet. Say if key K=5. Then every alphabet in the plain
message will be replaced by its 5 letter later alphabet. Therefore in
this case, the cipher text will be as follows.
m= James, Meet me at University, Steve
K=5
Cipher Text ( C) = K(m) = K(5)
'J' will be replaced by 'O', 'a' will be replaced by 'f' and similarly
all the letters will be replaced. So our generated cipher text would be,
Cipher Text = Ofrjx, Rjjy rj fy Zsnajwxnyd, Xyjaj
Disadvantage of Caesar Cipher
Might be , the above Cipher text looks very difficult to read or
unintelligible. But as you know there are only 26 alphabets in English.
Thus if the intruder came to know that Caesar Cipher is used, then its
very easy for him to break the code, as there are only 25 key value
possible. So he can use hit and try method for 25 times and will surely
obtain the original message in one of its try.
2. Mono-Alphabetic Cipher :
Mono-alphabetic Cipher is an improvement over Caesar cipher. In Caesar
Cipher, we were only able to replace the letters according to a pattern (
substituting according to K ) . But in Mono-alphabetic Cipher, we can
replace the letters randomly. This means any letter can be substituted
for any letter, as long as for a single letter throughout the message,
same susbstitute must be used.
Lets take an Example of a mono-alphabetic Cipher.

The plain message, "James, Meet me at University, Steve" will be encrypted as ,
Cipher Text = pqdtl, Dttz dt qz Xfoctklozn, Lztct
Mono-alphabetic cipher can be extended to 26! ways to encrypt your text.
It is almost equal 10^26. Thus, even if the intruder knows , that you
have used Mono-alphabetic cipher algorithm, then using a Brute Force
Approach ( Hit and Trial Approach ) also, it will be very brainstorming
task for him to crack the code.
3. Poly-alphabetic Cipher :
One more improvement of Caesar Cipher was Poly-alphabetic Cipher. In
poly-alphabetic , we use 2 Caesar ciphers together. There are 2 keys
such as ( with K=3 and K=5). Now we can chose that how these 2 keys
should be used in a pattern. For Example: C1 , C1 , C2 , C2 , C1. The
1st letter will be encrypted using 1st encryption key, the second will
also be using 1st encryption key, 3rd will be using 2nd encryption key,
4th will use 2nd key also and the 5th letter will be encrypted using 1st
encryption key. And this pattern will be followed for the coming
letters also. Lets take our Example :
Plain Text (m) = "James, Meet me at the University, Steve".
Keys, K=3, K=5
Cipher Text (C) = Mdrjv, Phjy ph dy ykh Xsnyhuxnwb, Vyjyh
In Poly-alphabetic Cipher, the Encryption and the Decryption key is the
knowledge of the two ciphers i.e.(K=3 and K=5) and the pattern C1 , C1 , C2 , C2 , C1.
- Since now a days , technology and the communication over Internet has grown to that extent, that these Symmetric Key Cryptographic Techniques also don't work very effectively. As the 2 commodities communicating needs to share the key. Which is not feasible. Thus these techniques are hardly in use in today's world. The techniques which are currently in use are PGP or Public Key Encryption.

No comments:
Post a Comment