//RSA ALGORITHM
#include <stdio.h>
int modulo(int e, int n, int pt)
{
int h;
if(e==0)
return 1;
else if(e==1)
return pt%n;
else
{
h = modulo(e/2, n, pt);
if(e%2==0)
return ((h*h)%n)%n;
else
return ((h*h)*(pt%n))%n;
}
}
int main()
{
int p, q, n, z, e, d, pt,ct;
printf("Enter p & q values <prime numbers>: ");
scanf("%d%d", &p, &q);
n = p*q;
z = (p-1)*(q-1);
printf("\nEnter a relative prime number to %d i.e., e value: ",z);
scanf("%d", &e);
d = 1;
while((d*e)%z!=1)
d++;
printf("d value is: %d\n", d);
printf("Keys are: <e, n>:(%d, %d)\t<d, n>:(%d, %d)",e,n,d,n);
printf("\n\nEnter message<pt> such that pt < %d : ",n);
scanf("%d", &pt);
ct = modulo(e,n,pt);
printf("\nCipher Text: %d\n",ct);
pt = modulo(d,n,ct);
printf("Decrypted Text: %d",pt);
return 0;
}
/* SAMPLE OUTPUT
Enter p & q values <prime numbers>: 11 7
Enter a relative prime number to 60 i.e., e value: 13
d value is: 37
Keys are: <e, n>:(13, 77) <d, n>:(37, 77)
Enter message<pt> such that pt < 77 : 5
Cipher Text: 26
Decrypted Text: 5
*/
Showing posts with label CN. Show all posts
Showing posts with label CN. Show all posts
Thursday, 7 April 2016
RSA Algorithm
Dijkstra's Algorithm
/PROGRAM FOR DIJKSTRA'S ALGORITHM #include <stdio.h> #include <conio.h> #define GRAPHSIZE 2048 #define INFINITY GRAPHSIZE*GRAPHSIZE #define MAX(a, b) ((a > b) ? (a) : (b)) int e; /* The number of nonzero edges in the graph */ int n; /* The number of nodes in the graph */ long dist[GRAPHSIZE][GRAPHSIZE]; /* dist[i][j] is the distance between node i and j; or 0 if there is no direct connection */ long d[GRAPHSIZE]; /* d[i] is the length of the shortest path between the source (s) and node i */ int prev[GRAPHSIZE]; /* prev[i] is the node that comes right before i in the shortest path from the source to i*/ void printD() { int i; printf("Distances:\n"); for (i = 1; i <= n; ++i) printf("%d\t", i); printf("\n"); for (i = 1; i <= n; ++i) { printf("%ld\t", d[i]); } printf("\n"); } /* Prints the shortest path from the source to dest. * dijkstra(int) MUST be run at least once BEFORE this is called */ void printPath(int dest) { if (prev[dest] != -1) printPath(prev[dest]); printf("%d ", dest); } void dijkstra(int s) { int i, k, mini; int visited[GRAPHSIZE]; for (i = 1; i <= n; ++i) { d[i] = INFINITY; prev[i] = -1; /* no path has yet been found to i */ visited[i] = 0; /* the i-th element has not yet been visited */ } d[s] = 0; for (k = 1; k <= n; ++k) { mini = -1; for (i = 1; i <= n; ++i) if (!visited[i] && ((mini == -1) || (d[i] < d[mini]))) mini = i; visited[mini] = 1; for (i = 1; i <= n; ++i) if (dist[mini][i]) if (d[mini] + dist[mini][i] < d[i]) { d[i] = d[mini] + dist[mini][i]; prev[i] = mini; } } } void main() { int i, j; int u, v, w; //clrscr(); FILE *fin = fopen("dist.txt", "r"); fscanf(fin, "%d", &e); for (i = 0; i < e; ++i) for (j = 0; j < e; ++j) dist[i][j] = 0; n = -1; for (i = 0; i < e; ++i) { fscanf(fin, "%d%d%d", &u, &v, &w); dist[u][v] = w; n = MAX(u, MAX(v, n)); } fclose(fin); dijkstra(1); printD(); printf("\n"); for (i = 1; i <= n; ++i) { printf("Path to %d: ", i); printPath(i); printf("\n"); } getch(); } /*SAMPLE OUTPUT ____________________ inputfile: dist.txt 10 1 2 10 1 4 5 2 3 1 2 4 3 3 5 6 4 2 2 4 3 9 4 5 2 5 1 7 5 3 4 _____________________

OUTPUT
Distances:
1 2 3 4 5
0 7 8 5 7
Path to 1: 1
Path to 2: 1 4 2
Path to 3: 1 4 2 3
Path to 4: 1 4
Path to 5: 1 4 5
*/ Distance Vector Routing Algorithm
//PROGRAM FOR DISTANCE VECTOR ROUTING ALGORITHM
#include<stdio.h>
#include<conio.h>
struct node
{
unsigned dist[20];
unsigned from[20];
}rt[10];
int main()
{
int dmat[20][20];
int n,i,j,k,count=0;
printf("\nEnter number of nodes : ");
scanf("%d",&n);
printf("\nEnter the cost matrix :\n");
for(i=0;i<n;i++)
for(j=0;j<n;j++)
{
scanf("%d",&dmat[i][j]);
dmat[i][i]=0;
rt[i].dist[j]=dmat[i][j];
rt[i].from[j]=j;
}
do
{
count=0;
for(i=0;i<n;i++)
for(j=0;j<n;j++)
for(k=0;k<n;k++)
if(rt[i].dist[j]>dmat[i][k]+rt[k].dist[j])
{
rt[i].dist[j]=rt[i].dist[k]+rt[k].dist[j];
rt[i].from[j]=k;
count++;
}
}while(count!=0);
for(i=0;i<n;i++)
{
printf("\n\nNODE %d ROUTING TABLE",i+1);
printf("\nNode\tDistance\tViaNode\n");
for(j=0;j<n;j++)
{
printf("\t\n %d\t %d\t\t %d",j+1,rt[i].dist[j],rt[i].from[j]+1);
}
}
printf("\n\n");
return 0;
getch();
}
/*SAMPLE OUTPUT
**********INPUT*********
Enter number of nodes : 5
Enter the cost matrix :
0 4 2 6 99
4 0 99 99 99
2 99 0 3 99
6 99 3 0 2
99 99 99 2 0

::::::OUTPUT ::::: NODE 1 ROUTING TABLE
Node Distance ViaNode
1 0 1
2 4 2
3 2 3
4 5 3
5 7 4
NODE 2 ROUTING TABLE
Node Distance ViaNode
1 4 1
2 0 2
3 6 1
4 9 1
5 11 1
NODE 3 ROUTING TABLE
Node Distance ViaNode
1 2 1
2 6 1
3 0 3
4 3 4
5 5 4
NODE 4 ROUTING TABLE
Node Distance ViaNode
1 5 3
2 9 1
3 3 3
4 0 4
5 2 5
NODE 5 ROUTING TABLE
Node Distance ViaNode
1 7 4
2 11 4
3 5 4
4 2 4
5 0 5
Cyclic Redundancy Check
=> A Generator is shared between the Sender and the Receiver.
=> Sender will convert Dataword into Codeword using the Generator and send it
to the Receiver.
=> Receiver upon receiving the Codeword, will check for errors in the received
Codeword with the help of the Generator.
=> If no error is found, receiver can extract Dataword from the Codeword.
Sender Side:
Generator/Divisor: 1100000001011 (Total 13-bits)
Dataword: 10101 (5-bits)
Extended Dataword: 10101000000000000 (17-bits: Dataword + 12 0's)
1100000001011 ) 10101000000000000 ( 11001
1100000001011
_____________
x1101000010110
1100000001011
_____________
x0010000111010
0000000000000
_____________
x0100001110100
0000000000000
_____________
x1000011101000
1100000001011
_____________
x100011100011
=> So, CRC Bits are: 100011100011
=> Now Codeword is 10101100001110100 (17-bits: Dataword + CRC bits)
=> Sender will send this Codeword to the Receiver.
Receiver Side:
Codeword: 10101100011100011
Generator/Divisor: 1100000001011
1100000001011) 10101100011100011 ( 11001
1100000001011
_____________
x1101100001010
1100000001011
_____________
x0011000000010
0000000000000
_____________
x0110000000101
0000000000000
_____________
x1100000001011
1100000001011
_____________
0000000000000
=> Reached Codeword contain no errors and now extract Dataword from Codeword
=> Dataword is 10101 [[by removing (Generator_Size - 1) bits from Codeword from Right]]
// PROGRAM FOR CYCLIC REDUNDANCY CHECK
#include<stdio.h>
int main()
{
int ds, dws, i, j, k, c=0; // ds-DivisorSize: dws-DataWordSize:
int div[100], dw[100], ta[100]; // div-Divisor: dw-DataWord: ta-TemporaryArray
//TAKING INPUT - DIVISOR
printf("Enter the size of divisor: ");
scanf("%d", &ds);
printf("Enter the divisor in bit pattern: ");
for(i=0; i<ds ; i++)
scanf("%d", &div[i]);
//TAKING INPUT - DATAWORD
printf("Enter the size of the DataWord: ");
scanf("%d",&dws);
printf("Enter the DATAWORD in bit pattern: ");
for(i=0; i<dws; i++)
scanf("%d",&dw[i]);
//ADDING ZEROS TO THE DATAWORD i.e., WE GOT EXTENDED DATAWORD HERE
for(i=dws; i<(dws+ds-1); i++)
dw[i] = 0;
//PRINTING THE EXTENDED DATAWORD
printf("Data after inserting zeros or <EXTENDED DATAWORD> : ");
for(i=0; i<(dws+ds-1); i++)
printf("%d", dw[i]);
//COPYING DATAWORD INTO TEMPORARY ARRAY
for(i=0; i<(dws+ds-1); i++)
ta[i] = dw[i];
//GENERATING THE REDUNDANT BITS
for(i=0; i!= dws; i++)
{
if(ta[i]==1)
for(j=0, k=i; j<ds; j++, k++)
ta[k] = ta[k]^div[j];
}
//ADDING REDUNDANT BITS TO THE DATAWORD
for(i=dws; i<(dws+ds-1); i++)
dw[i] = ta[i];
//PRINTING THE CODEWORD
printf("\n\nThe Generated CODEWORD is: ");
for(i=0; i<(dws+ds-1); i++)
printf("%d", dw[i]);
//COPYING CODEWORD INTO TEMPORARY ARRAY
for(i=0; i<(dws+ds-1); i++)
ta[i] = dw[i];
//DIVIDING CODEWORD WITH DIVISOR AT RECEIVERS END
for(i=0; i!= dws; i++)
{
if(ta[i]==1)
for(j=0, k=i; j<ds; j++, k++)
ta[k] = ta[k]^div[j];
}
printf("\nThe Remainder @ receiver's End is: ");
for(i=dws; i<(dws+ds-1); i++)
printf("%d",ta[i]);
//CHECKING IF THERE ARE ANY 1s IN THE REMAINDER
for(i=dws; i<(dws+ds-1); i++)
{
if(ta[i]!=0)
c++;
}
if(c==0)
printf("\nThe Codeword hasn't been altered::Message sent SUCCESSFULLY :)");
else
printf("\nThe Codeword has been altered :(");
return 0;
}
/* EXAMPLE OUTPUT
Enter the size of divisor: 4
Enter the divisor in bit pattern: 1 0 1 1
Enter the size of the DataWord: 5
Enter the DataWord in bit pattern: 1 0 1 1 1
Data after inserting zeros or <EXTENDED DATAWORD> : 10111000
The Generated CODEWORD is: 10111011
The Remainder @ receiver's End is: 000
The Codeword hasn't been altered::Message sent SUCCESSFULLY :)
*/
Character Stuffing
// PROGRAM FOR CHARACTER STUFFING
#include<stdio.h>
#include<conio.h>
#include<string.h>
void main()
{
int i,j=1;
char str1[100], str2[100], str3[100];
//clrscr();
printf("Enter a string: ");
scanf("%s",&str1);
//GENERATING ENCODED MESSAGE
str2[0] = '@';
for(i=0; i< strlen(str1); i++)
{
if( str1[i]=='@' || str1[i] == '#')
{
str2[j] = '#'; j++;
}
str2[j] = str1[i]; j++;
}
str2[j] = '@'; j++;
str2[j] = '\0';
printf("Encoded message is: %s", str2);
// DECODED MESSAGE or ACTUAL MESSAGE
j=0;
for(i=1; i<(strlen(str2)-1);i++)
{
if(str2[i]=='#')
i++;
str3[j]=str2[i];
j++;
}
str3[j] ='\0';
printf("\nDecoded or actual message is: %s", str3);
getch();
} Bit Stuffing
//PROGRAM FOR BIT-STUFFING #include<stdio.h> #include <string.h> int main() { char ed[100]; //ed - Entered Data char ta[100]; //ta - Temporary Array char dd[100]; //dd - Decoded Data char ecd[100]={'0','1','1','1','1','1','1','0'}; //ecd - EnCoded Data int n, i, j=0, count=0; printf("Enter the string:"); scanf("%s",&ed); printf("\nEntered bit pattern: %s",ed); //ENCODING for(i=0; i<strlen(ed); i++) { if(ed[i]=='1') count++; else count = 0; ta[j]=ed[i]; j++; if(count==5) { ta[j] = '0'; j++; count = 0; } } ta[j] = '\0'; strcat(ta,ecd); strcat(ecd,ta); printf("\nEncoded Data: %s",ecd); //DECODING j=0; count =0; for(i=8; i<strlen(ecd)-8; i++) { if(ecd[i]=='1') count ++; else count = 0; dd[j] = ecd[i]; j++; if(count==5) { i++; count=0; } } dd[j] ='\0'; printf("\nDecoded Data: %s", dd); return 0; }
Tuesday, 13 October 2015
Transport Layer 4
Introduction to Transport Layer
Before starting with our discussion on Transport Layer, I want to give you a live scenario, that will make you clear with the working of Transport Layer and the other layers of the Internet stack.
Let us suppose that there are two bungalows. One is in India and Other
is in America. In the bungalow in India, lives a person James along with
his 5 children. And in the bungalow in America, lives a person Steve
along with his 4 children. Now all 5 children of James write a letter to every children of Steve on every Sunday. Therefore total number of letters will be 20.
Thus, all the children writes the letter , put them in envelopes and
hand over it to James. Then James write source house address and the
destination house address on the envelope and give it to the postal
service of India. Now the postal service of India puts some other
addresses corresponding to the country and delivers it to the America
postal Service. The American Postal sees the destination address on the
envelopes and will deliver those 20 letters to the Steve House. Steve
collects the letter from the postman and after considering the name of
his respective children on the envelopes, he gives the letter to each of
them.
In this example we have processes and the layers. Let me explain.
Processes = children
Application Layer messages = envelopes
Hosts = The two Bungalows
Transport Layer Protocol = James and Steve
Network Layer protocol = Postal Service
- Here you can see, that according to children, James and Steve are the mail services, but in real they are just a part of the delivery process.
Suppose James and Steve went on a holiday for 10 days. Then as their
susbstitute, Angelina comes at place of James and Ashley comes at place
of Steve. But now for the two bungalows, unfortunately Angelina and
Ashley are not able of providing services as James and Steve. Angelina
and Ashley often drops letters, lose them, which are often eaten by the
dogs. Thus in the same way , services provided by the Transport Layer depends on type of protocol you use in your network.
- In this scenario, for example if the postal service cannot guarantee the maximum time taken in the delivery of the envelopes, thus there is no way that James and Steve can guarantee the maximum delays in the delivery of mails between the children. In the same way, the services provided by the Transport Layer are often subjected to the services provide by the underlying network layer. If the network layer cannot guarantee the delay in delivery of messages, then surely transport layer can never.
But still, a Transport Layer protocol guarantees certain services that are not guaranteed by the underlying Network Layer.
Thus, in our coming posts on transport layer and the other layers, you
must always remember this example, making it easier for you to
understand the layers concept.
Overview of Transport Layer Protocol:
Transport Layer acts as a medium
between the Application Layer and the the Network Layer. Transport Layer
provides a logical communication medium between the processes running
on different end systems. What does logical communication means?
Logical communication means that,
from an Application perspective, it is like the hosts are directly
connected to each other, but in reality , the hosts may be on two
opposite sides of the earth, connected by routers and links. As the
physical infrastructure of the two hosts and the intermediate can be
different, so for this reason , the Application processes use the
logical communication of the Transport Layer to send message from one
host to other and be free from the worry of the physical infrastructure
used.
Different Protocols of Transport Layer:
There are basically two types of protocols that Transport provides to give services to Application Layer. These are:
1. Transmission Control Protocol (TCP)
2. User Datagram Protocol (UDP)
TCP provides a reliable and
connection-oriented service to the Application. On the other hand, UDP
provides a unreliable and connection-less service to the Application.
Thus, it is upto the Application Developer, which transport Layer
protocol has to be used. For example: In case of HTTP, it is built over
TCP.
Transmission Control Protocol (TCP):
1. TCP provides a reliable delivery
of data. Irrespective of the fact, Network layer doesn't provides
reliable data transfer, TCP guarantees that. But TCP doesn't guarantee
anything about the time taken to deliver the packet.
2. TCP delivers the packet in their
respective order. This means, from the source, in the order in which you
will send the packet, they will reach in the same order at the
destination.
3. As TCP provides reliable data transfer and connection oriented services, it is a bit heavy and complex protocol.
4. TCP provides congestion control or the flow control within a network.
User Datagram Protocol (UDP):
1. UDP provides non-reliable data delivery. It is a connection-less service provider.
2. UDP doesn't guarantee the delivery of packets in the order they are sent.
3. Its a light protocol.
4. TCP provides congestion control or the flow control within a network.
User Datagram Protocol (UDP):
1. UDP provides non-reliable data delivery. It is a connection-less service provider.
2. UDP doesn't guarantee the delivery of packets in the order they are sent.
3. Its a light protocol.
On one hand , the Transport Layer provides communication between processes, whereas on the other hand, the Network Layer provides communication between hosts. Recall the above example of two bungalows and compare it with that. I am sure, you will understand it
TCP
Transmission Control Protocol (TCP)
Coming to the 2nd Transport Layer Protocol i.e. Transmission Control Protocol (TCP). The Transmission Control Protocol is such an important protocol in the Internet protocol model, that the whole Internet stack is called as the TCP/IP stack. TCP was 1st introduced in 1974.A number of applications use TCP for their execution such as HTTP, FTP, SMTP. Web Browser uses TCP to connect to the World Wide Web (www). TCP is used to deliver mails and transfer files from one host to another.
TCP is called as Connection-Oriented Protocol. Because in TCP, there is a 3-way handshake between the communicating hosts before exchanging the data or the message. There are lots of services provided by TCP that were not available by UDP. TCP provides Reliable Delivery of data, checks for error in the data and tries for its correction, delivers the packet in their respective order as they were sent by the sender. TCP also provides congestion control and flow control.
TCP provides a full-duplex mode of transmission i.e. if there is a connection between a Process Y on one host and a Process Z on another host. Then the Application message can be sent from Process Y to Process Z and from Process Z to Process Y within the same TCP connection.
A TCP connection is between a single sender and a single receiver. That means, TCP is a point-to-point connection control protocol. Multi-casting is not possible with TCP. Multi-catsing is a procedure of sending of data from a single sender to different receiver in a single send operation.
Problems with TCP:
Due to large traffic and congestion in the network, packets might get lost or they can get corrupt. TCP being the reliable data delivery protocol, detects all these problems, try to resolve them, asks for the re-transmission of the lost or corrupt packets, arranges the packet in order and send them to the receiver. The TCP receiver arranges all these packets in order and send them to the Application.
Thus in all this, re-transmissions , in order packet delivery, sometimes TCP results in long delays.
How TCP provides Reliable Delivery of Data:
TCP does it by a process of positive Acknowledgement. The receiver has to acknowledge the sender by sending a message to the sender, if it has receive the data correctly. The sender keeps the record of every packet it sends and maintains a clock with every packet. If the acknowledgment doesn't comes before the clock expires, the sender will re-transmit that packet, assuming that the packet is either lost or corrupted.
TCP Packet Structure:
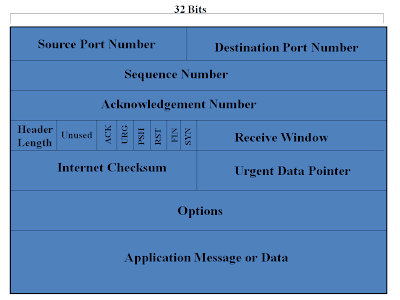
1. Source Port Number: It is used to identify the sending port number.
2. Destination Port Number: It is used to identify the receiving port Number.
3. Sequence Number and Acknowledgement Number : These are used for the reliable Delivery of data. Each Sequence and Acknowledgement Number is of 32 bits.
4. Header Length : This field is of 4 bytes. It tells the length of the TCP Header. The TCP header can be of variable lengths due to the presence of Option Fields. (In most cases, option field is empty, then the TCP header length is 20 bytes).
5. Unused or Reserved : This is reserved for future use. It is of 3 bit.
6. Pointers:
- ACK: This bit is used to indicate that whether the value in Acknowledgement field is valid or not. That means, whether it contains an acknowledgment number for a packet that has been successfully received.
- RST, SYN and FIN : These 3 bits are used for establishing a connection between and to stop a connection.
- PSH : This bit indicates whether the data should be pass to the upper layer or not. If PSH=1, it indicates the receiver should pass the data immediately to the upper layer.
- URG: This bit is used to indicate , if there is any data , that the host has marked as urgent. If URG=1, then it shows that some data has been marked as urgent. To know the address of that Urgent data, the 16-bit Urgent Data Pointer field is used which gives that information.
7. Checksum: It is of 16 bits. It is used to check that whether the data has arrived correctly or not. It is also used to detect any error in the data.
8. Application Message: It is of 32 bits. It contains the actual Application that the user wants to transmit.
9. Options : This field is of 32 bits. If the user need to send a data that is larger that the Application Message field size, then option field is used by the TCP header.
- It is recommended that you must send small packets, because if the packet size is larger, than the packet fragmentation will take place at the network layer, resulting in more number of lost packets.
TCP Implementation:
TCP is implemented in different ways. These are:
i) TCP TAHOE
ii) TCP RENO
iii) TCP VEGAS
iv) TCP SACK
We will discuss all these in details in our coming posts.
Concept of Sequence Number and Acknowledgement Number
These two numbers are of great importance in TCP. As they enable TCP for reliable Data Delivery and in order Delivery of Packets. Lets take a look and try to understand, what are these two fields .First of all, I would like to tell you that, TCP Sequence and Acknowledgement Number doesn't hold the size or number of transmitted packet , instead they contain the byte stream of those packets. That means , Sequence and Acknowledgement number contains the 1st byte of the transmitted packet.
The sender and the receiver decides on , what should be the starting sequence number of the 1st packet.
Sequence Numbers:
For Example : If you have a 50,000 bytes of data to send and the Maximum Segment Size (MSS) is 1000 bytes, you have to send 50 packets. Suppose you and the receiver decide the starting sequence number of 1st packet as 0. The second packet will have sequence number as 1000, 3rd will have 2000 and so on till 50000.
- MSS refers to the maximum size of a TCP packet that can be sent.
Acknowledgement Number:
As we have already discussed that TCP is full Duplex, so at the same
time both sender and receiver can send packets to each other
simultaneously. Let us Suppose that James is the sender and Steve is the receiver.
All the packets arriving from James, has a sequence number for the data
flowing from James to Steve. Now the Acknowledgment number that Steve
puts in its packet is the sequence number of the next packet, that Steve
is expecting from James.
For Example: If Steve has received all bytes numbered from 0 to 499 from
James. Then Steve will put the acknowledgement number as 500 in the
packet , it will send to James.
Cumulative Acknowledgement:
For Example: If Steve has received bytes numbered from 0 to 499 and
bytes from 1000 to 1099. Due to some failure or packet loss, Steve has
not received packet from 500 to 999 and Still he is waiting for 500
segment, to build the whole message from James in a proper order. Thus
Steve's next packet will contain acknowledgment number as 500. Since TCP
only acknowledges the 1st byte missing, this is known as Cumulative Acknowledgement.
This also brings one more concern, that when Steve receives packet from 0
to 499 and then from 1000 to 1099, but packet from 500 to 999 is still
missing. Thus the 3rd packet arrives out of order. Now a question
arises: What should the receiver do when it receives a packet out of order?
Thus , I would like to bring the fact to you that, Computer networking
doesn't impose any restriction on this. It totally depends on the people
programming the TCP implementation. They can choose either of these:
1. The receiver can discard the out-of-order packet as soon as he receives it.
or
2. The receiver can save the out of order packet in its buffer and waits for the missing packet to arrive.
- Hopefully maximum people will choose the 2nd option , in order to use the network bandwidth to the maximum, and to shorten the delay process. In Internet, the 2nd choice is used .
*****There are various interesting cases,
where you sometimes have to re-transmit and sometimes you need not
re-transmit a packet due to acknowledgment. Lets have a look at these
scenarios.
Scene 1: Re-transmission due to lost Acknowledgment :

Scene 2: Cumulative Acknowledgment avoids re-transmission of the 1st packet.
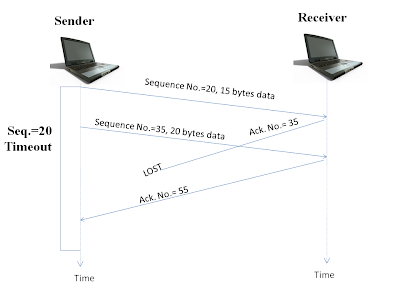
Suppose, sender sends a
packet of 15 bytes and a packet of 20 bytes back to back and they are
received at the receivers side and the receiver sends an acknowledgement
for the same. But the acknowledgment for the 1st packet is lost in the
network. But before the timeout occurs, the sender receives an
acknowledgment for the 2nd packet. Thus, the sender will understand,
that the sender has received all the packets till Sequence number 54.
Hence it will not resend the 1st packet.
UDP
User Datagram Protocol (UDP)
UDP is one of the most important protocol in the Transport Layer
providing services to the Internet. The UDP was first ever developed by
David P. Reed in 1980. UDP is used by transport Layer to pass the messages from Application Layer to the underlying Network Layer.
UDP is said to be a Connection-Less
protocol. This means that there is no handshaking between the two hosts
before transmission of packets. UDP provides no guarantee for
the delivery of packets. As transport layer works over Network Layer.
Thus, UDP working over IP , that is also an unreliable data delivery.
Therefore in case of UDP , you cannot be sure about the delivery of
message. UDP just provides simple multiplexing and demultiplexing at
hosts and a checksum for data integrity at both the hosts.
Multiplexing/De-multiplexing is performed by the Transport Layer
Protocols in order to send the data between the Network Layer and the
correct-Application Layer process.
Checksum is a procedure or you can say that it is a mathematical
calculation, that is done at both the sending and the receiving host, in
order to check that, whether the data has arrived in its original form
or not. It checks the correctness of the received data.
**** Now a question must be arising in your mind. That, if UDP doesn't
provides any guarantee of transfer of packets, it doesn't provide any
flow control, then why should a developer use UDP for his Application??
Let me tell you some uses of UDP and why should a Application Developer uses UDP for his Application.
There are various uses of UDP. These are as follows:
1. Stateless Protocol :
It doesn't maintain any state of the clients. Thus is very useful in
Application where there are millions of clients and maintaining
information of all the clients would be difficult task such as Streaming Media, etc.
2. No Re-transmission Delay :
As UDP doesn't provide any reliable delivery of data, so there are no
re-transmission for the lost packets. Therefore, this is good for real
Time Application such as Voice over IP etc.
3. Suitable for DNS:
It is a Transaction Oriented protocol, thus plays a vital role in query-response protocols, such as Domain Name Systems (DNS).
4. Small Header :
The header that UDP encapsulate with Application Layer message, is only
of 8 bytes whereas TCP header is of 20 bytes. We will discuss about
headers later in the post.
Working of UDP:
As we have discussed above that UDP do multiplexing/demultiplexing and
some error checking. It just adds a UDP header containing the Source
port Number and a Destination port Number and pass the data to the
underlying Network Layer. Then the network Layer adds it own header to
Transport Layer packet and sends it to the destination.
Port Numbers:
Ports are identified by a port number. A Port Number is a 16 bit number i.e a port number can be assigned from 0 to 65535 to an Application. Port Number from 0 to 1023 are registered for the IANA registered services such as HTTP, FTP, TCP etc. and port Numbers from 1024 to 65535 are dynamic, that means, a newly developed application can be assigned port number among these.
UDP Packet Structure:

The UDP Header has 4 fields . Each field is of 16 bit or 2 bytes. Thus UDP header length is 8 bytes or 32 bits.
******** 1 byte= 8 bits *********
Source and Destination Port Number:
The source and destination port number allows the application to pass
the message to the correct process running on the end systems or the
hosts. They are of length 16 bit each.
Length:
It tells you the complete length of the UDP Packet i.e Length = UDP header + Application Message length. Thus for different UDP segments, length will be different, depending upon the size of the Application Message.
Minimum Length will be 8 bytes i.e. the size of the header.
Checksum:
Checksum is used on the receiving side in order to check, whether the
data has arrived in its original form or not. Or to check any error in
the data, during transmission.
Checksum Calculation:
Checksum is used for Error Detection.
Let us suppose that we have
Source Port Number (S) = 0001101110010101
Destination Port Number (P) = 1010100101110011
Length (L) = 0011011110010001
We will add all these and put it in the Checksum field.
S+P=T
0001101110010101
1010100101110011
+ 1100010100001000 = T
T+L= A
1100010100001000
0011011110010001
+ 1111110010011001 = A
Now we will take the 1's complement of A, i.e converting all 1's to 0 and all 0's to 1.
Thus 1's complement of 1111110010011001 is 0000001101100110. And this is our checksum.
We will put this checksum in the
header and send the packet. On the receiving side, the receiver will add
all the 4 fields of the header i.e. Source+Destination+Length+Checksum.
If the data has arrived him
correctly, then the sum will be equal to 1111111111111111. That is , he
will get all 1's after adding the 4 fields. And if he gets 0 at some bit
, that will show him the error.
- You can see that UDP provides error checking, but it doesn't provide anything to recover from that error. Some UDP applications will discard the packet with an error, and some will pass the packet to the Application with a given warning.
Datagram Network Layer
Network Layer Datagram and its format
There are basically 3 components or 3 main parts of Network Layer. The 1st component is the Routing Protocols and Routing algorithms . The 2nd component is the IP protocol that covers the Network Layer datagram format and addressing convention. The 3rd component is the Internet Control Message Protocol (ICMP) protocol that undertakes Error reporting and Router Signaling.
IP Datagram Format
There are 2 versions of IP. IPv4 and IPv6. IPv4 is widely used in internet. As the number of users is increasing every day , thus an alternative of IPv4 was developed (IPv6) in order to provide more number of IP addresses to the hosts.
IPv4 Datagram format :

It tells the router about the version of IP whether it is version 4 or version 6. Because different version are processed differently. This field is of 4 bits.
2. Header Length :
This field tells you the size of IP header. There are variable field in the IPv4 header. Like option can be there or not. So Header Length is usually used to tell, from where the actual Data is starting in an IP datagram. This field is of 4 bits.
3. Type of Service :
This field is used in IP header in order to allow router to distinguish about the type of application. For example, whether an Application is a Real-Time Datagrams such as for Video Calling or a Non Real-Time Datagrams such as for SMTP or FTP. This field is of 8 bits.
4. Datagram Length :
This field indicated the total size of the IP datagram i.e. IP header + Data. This field is of 16 bits.
5. Header Checksum :
This is used in order to detect the error in the IP datagram. Typically in most cases, if a router detects an error in a datagram, it discards that datagram. This field is of 16 bits.
6. Upper Layer Protocol :
This field indicates the name of the protocol that is being used in the above layer. Whether it is TCP or UDP. This field is used when the datagram reaches its destination. Then a number 6 in this field indicates , that TCP is used and a number 17 indicates that UDP is used at the Transport Layer. This field is of 8 bits.
7. Time-to-Live (TTL):
This field is used in order to ensure that the datagram is not circulated into the network for an unlimited period of time. For Example, in an infinite loop. Thus this field is decremented by one, every-time a datagram is processed at a router. Therefore when TTL becomes 0, the datagram is dropped. This field is of 8 bits.
8. Source and Destination IP address :
The source puts its own IP address in the source field and the address of the final destination in the destination field. The source often gets the IP address of the destination by a DNS lookup. Each of the source and destination address field is of 32 bits in IPv4 header.
9. Data :
This field contains the actual data to be transmitted to the destination. This field in an IP datagram contains the TCP segment to be transmitted. This field is of 32 bits.
- The IPv4 header is of 20 bytes. We assume that there is no options. If it is working over TCP, then the each IPv4 datagram caries a total of 40 bytes header (TCP header of 20 bytes and IP header of 20 bytes) + the Application Message.
10. Identifiers, Flags and Offset :
These 3 fields are used in order to break the datagrams into the smaller segments , when a datagram is larger than a maximum limit arrives. Identifier field is of 16-bits, flags is of 3-bits, and fragmentation offset is of 13 bits.
******You can clearly see that the source IP address field is of 32 bits. That means there can exist 2^32 different IP addresses in Internet. This is almost equal to 4 billion IP addresses.*****
IPv6 Datagram Format

Same as IPv4. It tells you about the version of the IP. Surely in this case, the value will be 6. This field is of 4 bits.
2. Traffic Class :
This field is of 8 bits. This is similar to Type of Service field in IPv4. This tells the router about the Real Time or non-real time Applications .
3. Payload Length :
It is a 16 bit field, describing the size of data in IP datagram. It gives you the size of the Data field.
4. Next header :
It tells you the type of the upper layer protocol being used. This field is of 8 bits.
5. Hop Limit :
This Hop count is decreased by one at every router. When Hop Count reaches, the datagram is discarded. This field is of 8 bits.
6. Source and Destination IP address :
Each of the source and destination address fields are of 128 bits. That means, now Internet can have 2^128 different IP addresses. This unit is in trillions. Thus the internet now can be expanded much bigger than in IPv4.
7. Data :
It contains the Transport Layer header along with the original Application message.
- Now as the the size of Source and destination IP address increases, the header size of IPv6 datagram is 40 bytes.
Advantages of IPv6 :
1.In IPv6 , the size of IP addresses is increased from 32 bits to 128
bits. Therefore , now if you give an IP address to every seed on the
Earth, the IP addresses will not end. That means, now the Internet world
would not go out of IP addresses.
2. A lot of fields are removed in IPv6. Such as Options field, making it
a fixed length header, resulting in the faster processing of IP
datagram.3. There is no fragmentation of IPv6 datagram. If the datagram is large, the router simply drops it and sends a "Datagram too Large" ICMP error message.
4. The checksum is removed in IPv6 header. The developers thought that the checksum at the Transport layer is suitable. At network layer, it is getting redundant, so developers decided to remove checksum from network layer.
As IPv4 header contains a TTL field, thus checksum has to be processed at every router. Along with fragmentation, this is a very costly process.
Transformation from IPv4 to IPv6 :
As you must know, that most of the routers around the globe are working on IPv4. And the present routers are not compatible of handling IPv6 datagrams. So what should be done to make them IPv6 compatible. One solution that some scientists give is that, a flag day should be declared and all the networks of the world should be closed on that day for this transformation, and in that time the routers must be converted to IPv6. But do you really think that is it a possible solution with millions of systems in the Internet? Surely , I don't think so.
Other solution can be that the new IPv6 routers can be made compatible of handling both the IPv4 and IPv6 datagrams. This is known as Dual Stack Approach. Such nodes or routers that are capable of implementing both are known as IPv4/IPv6 nodes. But a still a problem is there in this approach also. Let me explain you with an example :
Suppose Router A wants to send a IPv6 datagram to Router F. But for
transmitting a datagram to F, the datagram has to traverse through the
intermediate routers B,C & D. But the router C & D are only
IPv4 compatible routers. Now Router A will send an IPv6 datagram to B,
but C is only IPv4 compatible. Thus , B has to send an IPv4 datagram to
C. So router B will copy the fields of IPv6 to IPv4 datagram router, and
the appropriate mappings can be done. But you can see that, there are
certainly some fields in IPv6 that doesn't have a counterpart in IPv4.
In such case, some fields will be lost. Since router E & F are
capable of exchanging IPv6 datagram. But certainly , datagram arriving
from D to E, doesn't contain all the fields originally sent by router
A.
To overcome this dual Approach problem, we have a technique known as Tunneling. Tunneling
will enable router E to receive the original datagram sent by router A.
Let us take an Example given below. Suppose IPv6 compatible Router U
and Router Z wants to inter-operate , but are connected by intermediate
router W & X, that are IPv4 compatible only. Thus the intermediate IPv4 routers are referred to a Tunnel.

Now a IPv6 router on the sending side of the tunnel , say router V, puts
a complete IPv6 datagram into the data field of IPv4 datagram. This
IPv4 datagram is addressed to Router Y. Then this datagram is sent into
the tunnel. The IPv4 router routes this datagram inside the tunnel among
themselves , without knowing that the IPv4 datagram itself contains a
complete IPv6 datagram inside it. And finally the datagram reach router
Y, where the IPv6 datagram is extracted from IPv4 and pass it on to Z.
In this way, the IPv6 datagram reaches its destination without losing
any fields.
Network Layer 5
The Network Layer
Characteristics of Network Layer:
1. Host Addressing:
Every end system or a host must have a specific address, so that its
address could be known to the outer world. This address is known as IP
address. IP addresses are of 32 bits. Such as, 192.145.59.28. For
Example : You can be "Steve Bond" for the people of your house, "Steve
Bond", 54-Church Street for the people in USA, "Steve Bond", 54-Church
Street, USA, for the people of the whole world. In the same way, this IP
address hierarchy works.
2. Connection-less Service:
Since IP is the only protocol, working at Network Layer. Thus when a
datagram is travelling from sender to receiver, the recipient doesn't
need to send any acknowledgement as, IP is connection-less.
- The Network Layer is responsible for Packet Forwarding and Routing .
Forwarding : This is the
phenomenon that includes when a packet arrives at a router, then to
which next appropriate outgoing link , it should be sent. For Example
in the given figure, a packet from Host A arriving at router R1 must be
forwarded to the next router on the way to Host B.

Routing : On
one hand , where forwarding includes the functioning between two
routers, the Routing includes the functioning of the whole network.
Routing determines the whole path and the number of routers that the
packet should go through during its flow from sender to receiver. The
algorithms that calculates these paths are known as Routing Algorithms.
There is a forwarding table in every router. Every router
examines the header field in the arriving packet and based on the
corresponding index to the header field, router forwards packet to the
the outgoing link. For Example, in the given figure, the header field
value of the incoming packet is 0101 and its corresponding outgoing link
is 3. Thus the router examines its forwarding table and transfers that
packet to the corresponding output link i.e 3.

Figure: Values in Forwarding Table at Different Routers
Centralized Algorithm :
The Algorithm may be operating in a single router or the centralized router and updating the records of each of the other routers also.
The disadvantage of this technique is that, on a single router a lot of burden is there. And the other disadvantage is, if the centralized router goes down, then the whole network will crash.
De-Centralized Algorithm :
The Routing algorithm is running on every router.
In both the cases, the router receives a routing protocol message, and updates or configures its forwarding table.
- You can assume that , this all forwarding and routing configuration is done by humans. That is, persons are physically present at every router. Thus every human operator have to interact with each other in order to update the forwarding table records, so that the travelling packets reach the correct desired destination. But as you know, human configuration are more prone to errors and will be very slow, in comparison to a routing protocol. Therefore we have softwares and routing protocols in our networks to automate our work, in order to provide a much more efficient and fast delivery of packets to the end users.
- There are numerous numbers of algorithms that run in the routers to provide fast and correct delivery of packets . For Example : Link State (LS) Routing Algorithm, Distance Vector (DV) Routing Algorithms etc. We will discuss each of these algorithms in detail in the coming posts.
IP Address :
As we all know, that humans understand the words and the letters very well. Thus domains name are very easy to remember by us. Like www.google.com, www.com2networks.blogspot.com etc. But what about routers and intermediate switches. These domains are of variable length. Thus they are very difficult to be understood by the routers. Therefore, there are fixed length IP addresses corresponding to every domain name, that are understand by routers. These IP addresses are of 32 bits. For Example : www.google.com corresponds to 192.174.43.128. Every section separated by the decimal is of 8 bits. Thus every section can contain number from 0 to 255 (2^8) .
The mapping of these domain names with the corresponding IP address is done by a protocol known as Domain Name System (DNS).
Services Provided by the Network Layer :
1. Guarantee of Delivery of Packets :
This means the packet will definitely reach its destination.
2. Guaranteed Delivery with Bounded Delay :
This means not only delivery of packet to its destination, but also within the given period of time. For Example : Delivery of packet in 50 msec.
3. Delivery of Packet in-order :
The packets will reach the destination in the same order as they were sent.
4. Minimal Jitter :
Jitter is the difference in the delays of the two packets of the same message arriving at a destination. Thus network must provide Minimal Jitter.
- Now you must always remember that, the Network Layer doesn't provide any of these services. The Network Layer just provide a single service that is "Best Effort Service". The Network Layer tries to provides the best of its effort to provide these above services to the communicating hosts. But it doesn't guarantees anything.
Thus you can say , Best Effort Service can be Alternatively be used for
No Service at all also. A network providing no delivery of packets can
also come under Best Effort Service.
Router Architecture:
Now lets have a brief look at the parts of the Router or what is all there inside a router.

Figure : Architecture of a Router
1. Input Ports :
The input port performs various functions inside a router. The incoming
link is terminated at the left most box of the input port. At the right
most box of the input port, it is the place where the forwarding table
is consulted and the corresponding output link is determined.
2. Switching fabric :
The Switching fabric connects the input ports of router to its output ports and incorporates the the processor.
3. Output Ports :
The output port transmits the packet to the correct outgoing link towards its destination.
4. Routing Processor :
The Routing processor controls all the functions of consulting ,
updating and configuring the router and forwarding table. It executes
the routing protocol. It also performs network management functions.
DDNS
Distributed Domain Name System (DNS)
To deal with millions of Internet users throughout the globe, a single DNS server is not capable of mapping each and every hostname to every IP address in a Computer Network. Thus, a network of DNS known as Distributed DNS is formed. This Domain Name Systems are structured in a hierarchical format. There are basically 3 types of DNS servers- Root Servers, Top-level Domain Servers and Authoritative Servers. Lets have a look at this diagram.
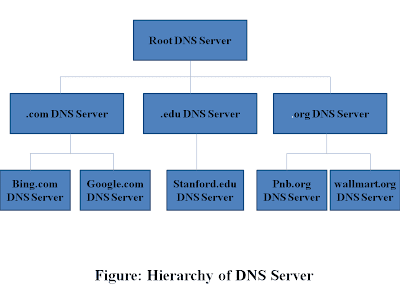
There are 13 root servers throughout the globe. They are named from A to M. Most of these are located in North America. This doesn't mean that there are only 13 root DNS servers. This indicates that there are 13 authoritative companies that look after these root DNS servers and most of these companies are in North America. Because root DNS servers are replicated at various places to distribute the load and provide better services. The number of root DNS servers is around 247 that are spread throughout the world.
2. Top Level Domain (TLD )Servers:
These servers are responsible for the Top level Domain Names such as .com, .org, .edu, .gov etc. and the Top level Domains of a country such as .in, .us, .fr etc. The Two companies, 1st is Verisign Global Registry Services maintains the TLD servers for com top level domain and 2nd one is the Educause, that maintains the edu top level domains.
I refer you to read IANA TLD 2012 to get more knowledge on Top Level Domain Servers.
3. Authoritative Servers:
A company or a university can maintain their own authoritative DNS servers. The organisation having its host accessible publicly to the Internet can provide an authoritative DNS servers.
- Here is a Map showing all the DNS servers throughout the Globe.

There is also one more type of DNS servers. These are known as Local DNS servers. Every Internet Service Provider (ISP) has a local DNS. Whenever a host connects to a ISP, the ISP provides it with the IP address of its local DNS server. When a host makes a DNS query , the query is 1st send to the local DNS, which forwards it to the upper DNS server hierarchy.
Let us discuss an example that will make you clear with the working of the DNS servers in a hierarchy.
Let us suppose that a host ec.school.edu wants the IP address of the cs.stanford.edu. The local DNS server of ec.school.edu is dns.school.edu and the authoritative DNS server of cs.stanford.edu is dns.stanford.edu. The host ec.school.edu will 1st send the DNS query to its local DNS server. The query is to translate the hostname cs.stanford.edu into its IP address. The local DNS server forwards the query to the root DNS server. The root DNS notes that the query contains the .edu suffix, and returns the local DNS server a list of IP addresses for TLD servers responsible for .edu. The local DNS server then re-sends the query to a TLD server. The TLD server notes that query is with .stanford.edu suffix. Thus it responds with the IP address of authoritative DNS server for the Stanford University, named dns.stanford.edu. The local server now sends the final query to the dns.stanford.edu, which responds with the IP address of the cs.stanford.edu. You can see that, to obtain the IP address for 1 hostname, 8 DNS queries are being sent. Thus to reduce these queries DNS caching is used, that I will tell you later in this post.
Lets clear it with the help of a figure :

A figure for this scenario:

There are particularly 2 types of queries.
i) Recursive Query
ii) Iterative Query
The query sent from ec.school.edu to dns.school.edu is recursive , as it is send on its own behalf. But the other subsequent queries are iterative, since the replies are directly returned to dns.school.edu. In Figure 1 and Figure 2, only the query send from ec.school.edu to dns.school.edu is recursive, rest all other queries are iterative.
Diagram for Recursive Queries:

- In an Internet world, the queries follows the Figure 1 and Figure 2 pattern.
DNS caching is an important aspect of DNS. It is highly used in the real Internet world to reduce the delays and to reduce the number of DNS queries running around the Internet.
Let me take the above Stanford example and you will understand DNS Caching very well.
Here ec.school.edu queries to Local DNS server to get the IP address of cs.stanford.edu. Now after completing this request, the Local DNS server will save this mapping in its own memory. Therefore, if any other host from the school , queries for the cs.stanford.edu again, then the local server can reply from its own memory at much faster pace. This phenomenon is known as DNS Caching. The Local DNS servers can cache the mappings of TLD servers also, in order to bypass the root servers.
But this caching will be removed after some period of time , as mapping between the hosts and IP address is not permanent.
DNS
DOMAIN NAME SYSTEM (DNS)
After Covering HTTP, FTP and SMTP, now we will discuss about another Application layer protocol, DNS. DNS stands for Domain Name System.
Before starting I would like to ask you , how do you identify human beings.
I am sure , your answer will be , by their names. But I want to tell
you that , there are also other ways of identifying a human being. Such
as from their Driving License, from their passport Number etc. For
example, If you work in a industry, where 1000's of employees work. And
there is a database, that store the information of every employee
according to the Serial Number id of that employee. So for the database,
your serial id is an appropriate option to remember you. But your
friend will not use that serial id, he will call you by your name only.
Therefore, we humans can be identified in different ways, those
different ways can be used for different preferences where appropriate.
Similarly the Internet hosts are identified in many ways. One way is to
identify them by their host names. For Example : Hostname can be
www.google.com, yahoo.in , network.edu etc. But these host-names are
appreciated by humans only because hostnames are easily readable by
them. Hostnames provide some information about the host. Say, if a
hostname is www.school.edu.fr. Thus the .fr at the last refers that the host might be located in France. Except that it tells nothing.
But hostnames can be of variable lengths. What about the routers. it
will be difficult for them to process these variable length hostnames.
Therefore, for these reasons, hosts are also identified by IP-addresses.
IP address are the fixed length numbers. These are of 32 bits or 4 bytes such as 198.168.32.45.
Each of the 1 byte or 8 bits separated by a decimal, can contain number
for 0 to 255. These 4 bytes follow a hierarchical structure. For
example, if you read a postal address on a letter, you will keep getting
a more idea as you go down reading it, that where the address is
located. In the same way, as we keep scanning the IP address from left
to right, we will keep getting more and more information about the host,
where it is located.
Importance of Domain Name System (DNS) :
Above we have discussed two ways of identifying a host. Either by their
hostname or IP address. Human prefers hostname while the routers prefer
IP addresses. Therefore to fulfill these preferences, it is a need that
there should be directory that transforms the hostnames into routers
understandable IP addresses. This work is done by Domain name System. It transforms the hostnames into their respective IP addresses.
Therefore we can say that, DNS is a database or a distributed database that is implemented in a hierarchy of DNS servers.
Also DNS is an application layer-protocol that apply queries to that
database. DNS is used or implemented by the other Application Layer
Protocols like HTTP to translate the human provided hostnames to IP
addresses.
Lets discuss this with an example. Say, you type a URL in your Browser (
a HTTP client), www.com2networks.com/ images.png. Thus, for the client
host to send the HTTP request to the Web Server www.com2networks.com,
the user host must obtain the IP address of www.com2networks.com. These
are the steps that took place when you type the URL in the Browser and
press Enter.
1. The user or the client machine executes the client side of the DNS.
2. The Browser extracts the hostname from the URL i.e. www.com2networks.com, and delivers it to the client DNS.
3.The DNS client sends a message containing the hostname to a DNS server.
4. The DNS server replies back with the IP address of the requested hostname to the DNS client.
5. Now the browser receives the IP address from client DNS, it can setup
a TCP connection to the HTTP server at that IP address. ( Connection
with HTTP process at port 80).
- You must have noticed that except a HTTP request-response, now there is a added DNS request-response also, resulting in the additional delay.
The DNS servers are often UNIX machines running on the Berkeley Internet Name Domain (BIND) Software. And the DNS protocol runs over UDP at port 53.
There is certain other services also that are provided by the DNS. I am
telling you one of those which is the most important of all..
HOST ALIASING:
A hostname can be very complicated to remember . For example: east-country.education.girls.school.com . Thus, 1 or more alias name can be made for it, such as school.com or www.school.com. Hence , in this scenario, the east-country.education.girls.school.com is said to be the canonical hostname. DNS can obtain the canonical hostname as well as the IP address of a host.
Other service of DNS is Load Distribution.
Working of DNS and Issues Related With It :
Now you know how DNS works. When the browser wants to transforms a
hostname into IP address, it invokes the DNS client . The DNS in the
host sends a query into the network. After some Delay, the DNS in the user host gets a reply message within UDP datagram at port 53
that provides the correct IP address for the requested hostname. You
can see that , DNS provides a simple translation service behind the
scene i.e. you can also say that it acts as a black box. But in reality,
this is very complicated phenomenon, that consists of thousands of DNS
servers that are distributed among the globe. And also an Application
Layer Protocol that regulates how the DNS servers and the requesting
hosts communicate.
Now its possible that here is a single DNS server that contains all the
IP addresses and the related mappings. The hosts just query the single
DNS and the DNS responds directly to the requesting host. But in Today's
Internet, where millions of hosts are requesting at a time. Thus, for a
single DNS to process all queries is impossible. There are certain
problems associated with this centralized DNS design. These are:
i) DNS failure: If at some point of time, this single DNS server crashes or stops, then the whole Internet is dead.
ii) Far Away DNS: For
example, if the single DNS is put in Australia, then all the requests
from USA have to travel the whole globe to process their requests,
resulting in large delays.
iii) Traffic : There are millions of users around the globe, thus making it almost impossible for the single DNS to process all the requests.
iv) Maintenance: Every day , large number of new hosts are
getting added to the internet. Thus, the single DNS have to updated with
these records. Hence making it very difficult to maintain.
You can now illustrate that a centralized DNS is not possible in today's
Internet. Thus, distributed DNS are implemented all over the globe to
provide a better and a fast service. We will discuss the Distributed DNS
in the next Post. Now coming to DNS Records and Message Format.
DNS Records:
The DNS servers that together implements the DNS distributed database ,
store Resource Records(RR's). including RR's that provide transformation
from hostname to IP address. Each DNS reply message contains one or
more resource records.
A Resource Record(RR) has four fields:
(Name, Value, Type, TTL)
TTL= Time to Live
TTL determines, when the record should be removed from the cache.
The DNS servers have record in 4 types that have different fields for RR's. These records are as follows:
a) If Type=A, the "Name" is a "hostname" and "Value is the IP
address "of the hostname. For example:(shop.kung.com, 127.134.87.197,A).
This a Type A example.
b) If Type=NS, then "Name" is "Domain(as kung.com)" and the
"Value" is the "hostname of an authoritative server" that will know ,
how to obtain the IP address of the host. For Example: (kung.com,
dns.kung.com, NS). This is a NS Type Records.
c) If Type=CNAME, then "Value" is a canonical hostname for the
alias hostname and "Name" will provide the "Domain name" for the
hostname. For Example:(kung.com, shop.cloth.metre.kung.com, CNAME). This
is CNAME Type Record.
d) If Type=MX, the "Value" is the "canonical Name" of a mail server that has a Alias Name. For Example:(kung.com, mail.shop.kung.com, MX).
- MX records enables the hostnames of mail servers to have easy alias names.
- MX also enable an organisation to have same alias name for its mail server and one of its other server.
- To get the canonical name for the mail server, a DNS client would query for a MX record and to obtain the canonical name of the other server, the DNS client would query the CNAME record.
DNS Message Format :
There are two types of DNS messages. DNS query and DNS reply. The format
of both these messages is same. Lets have a look at the message format
of DNS.

1. The first 12 bytes or 96 bits, are called as the header
section, which has 6 fields. The Identifier filed is of 16 bits, that is
a number which identifies the query. A Flag contains 1 bit number,
either 0 or 1. If the Message is a query, the flag is set as 0, and if
the message is a reply, flag is set to 1.
2.The Next 4 fields i.e. No. of Questions, No. of Answers, No. of Authority RR's and No. of additional Information RR's. contains information about the Number of Occurrences of the Below Given Fields.
3. The Question Section Contains the information about the query. This Section includes two things. 1. A Name field that contains the name of the query. 2. A Type Field that contains the type of question being queried. For Example: A host Address associated with a Name of Type A.
4. In the Reply from the DNS server, the Answer Section contains the Resource Records for the name, that was queried.
5. The information about the Authoritative Servers is contained in the Authority Section.
This was all I had in Introduction, Basics and Message Formats of Domain
Name System. In the next Post, Continuing with DNS, I will discuss
about Distributed Structure of DNS and DNS caching.
Subscribe to:
Comments (Atom)
