Monday, 16 November 2015
Notes
Please click on that boxes
Database Access Notes
Distributed Databases Notes-All 8 units
1.Introduction: syllabus, administration and organisation of the course, general introduction in distributed DBMS
2. DDBMS Architecture: definition of DDBMS architecture, ANSI/SPARC standard, global, local, external, and internal schemas, DDBMS architectures, components of DDBMS
3.Distributed Database Design: conceptual design (what can be distributed, design patterns), top-down, bottom-up patterns, technical design (fragmentation, allocation and replication of fragments, optimality, heuristics)
4.Semantic Integrity Control: view management, security control, integrity control
5.Distributed Query Processing: overview of query processing and query optimization, query decomposition and data localization
6.Query decomposition and data localization: normalization, analysis, elimination of redundancy, rewriting, reduction for HF, reduction for VF
7.Optimization of Distributed Queries: basic concepts, distributed cost model, database statistics
8.Optimization of Distributed Queries: ordering of joins and semijoins, query optimization algorithms, INGRES, System R, hill climbing
9.Transactions: introduction to transactions, definition and examples, properties, classification, processing issues, execution
10.Concurrency Control: definition, execution schedules, examples, locking based algorithms, timestamp ordering algorithms, deadlock management
11.Reliability: definitions, basic concepts, local recovery management, distributed reliability protocols
12.Reliability: distributed reliability protocols, 2PC protocol
Please click on that boxes
| MTECH CALENDER | ||
| . | . | |
| MFCS NOTES | WEB TECHNOLOGIES | |
| . | . | |
| MTECH SYLLABUS | ||
| ADS LAB | ||
| JWT LAB | validation program | |
| Servlet program | ||
Database Access Notes
Distributed Databases Notes-All 8 units
1.Introduction: syllabus, administration and organisation of the course, general introduction in distributed DBMS
2. DDBMS Architecture: definition of DDBMS architecture, ANSI/SPARC standard, global, local, external, and internal schemas, DDBMS architectures, components of DDBMS
3.Distributed Database Design: conceptual design (what can be distributed, design patterns), top-down, bottom-up patterns, technical design (fragmentation, allocation and replication of fragments, optimality, heuristics)
4.Semantic Integrity Control: view management, security control, integrity control
5.Distributed Query Processing: overview of query processing and query optimization, query decomposition and data localization
6.Query decomposition and data localization: normalization, analysis, elimination of redundancy, rewriting, reduction for HF, reduction for VF
7.Optimization of Distributed Queries: basic concepts, distributed cost model, database statistics
8.Optimization of Distributed Queries: ordering of joins and semijoins, query optimization algorithms, INGRES, System R, hill climbing
9.Transactions: introduction to transactions, definition and examples, properties, classification, processing issues, execution
10.Concurrency Control: definition, execution schedules, examples, locking based algorithms, timestamp ordering algorithms, deadlock management
11.Reliability: definitions, basic concepts, local recovery management, distributed reliability protocols
12.Reliability: distributed reliability protocols, 2PC protocol
NPTEL
| Course Name | Type | Coordinators | Institute | Available |
|---|---|---|---|---|
| Artificial Intelligence(Prof.P.Dasgupta) | Video | Prof. P. Dasgupta | IIT Kharagpur | Course contents |
| CAD for VLSI Design II | Web | Prof. V. Kamakoti Prof. Shankar Balachandran | IIT Madras | Course contents |
| Computational Geometry | Video | Prof. Sandeep Sen | IIT Delhi | Course contents |
| Computer Architecture | Video | Prof. Anshul Kumar | IIT Delhi | Course contents |
| Computer Networks | Web | Prof. Hema A Murthy | IIT Madras | Course contents |
| Computer Organization | Video | Prof. S. Raman | IIT Madras | Course contents |
| Design and Analysis of Algorithms | Video | Prof. Sundar Viswanathan Prof. Ajit A Diwan Prof. Abhiram G Ranade | IIT Bombay | Course contents |
| Electronic Design Automation | Video | Prof. Indranil Sengupta | IIT Kharagpur | Course contents |
| Logic for CS | Video | Prof. S. Arun Kumar | IIT Delhi | Course contents |
| Principles of Communication | Web | Prof. Hema A Murthy | IIT Madras | Course contents |
| Programming and Data Structure | Video | Dr. P.P.Chakraborty | IIT Kharagpur | Course contents |
| Artificial Intelligence | Video | Prof. S. Sarkar Prof. Anupam Basu | IIT Kharagpur | Syllabus Course contents |
| Artificial Intelligence | Web | Prof. P. Mitra Prof. S. Sarkar | IIT Kharagpur | Syllabus Course contents |
| CAD for VLSI Design I | Web | Prof. V. Kamakoti Prof. Shankar Balachandran | IIT Madras | Syllabus Course contents |
| Compiler Design | Web | Prof. Sanjeev K Aggarwal | IIT Kanpur | Syllabus Course contents |
| Compiler Design | Video | Prof. Y.N. Srikanth | IISc Bangalore | Syllabus Course contents |
| Computational Number Theory & Cryptography | Web | Dr. Pinaki Mitra | IIT Guwahati | Syllabus Course contents |
| Computer Graphics | Web | Prof. Prem K Kalra | IIT Delhi | Syllabus Course contents |
| Computer Graphics | Video | Prof. Sukhendu Das | IIT Madras | Syllabus Course contents |
| Computer Networks | Web | Prof. Ajit Pal | IIT Kharagpur | Syllabus Course contents |
| Computer Networks | Video | Prof. Sujoy Ghosh | IIT Kharagpur | Syllabus Course contents |
| Computer Organisation and Architecture | Web | Prof. Bhaskaran Raman | IIT Bombay | Syllabus Course contents |
| Computer Organization and Architecture | Web | Prof. Jatindra Kumar Deka | IIT Guwahati | Syllabus Course contents |
| Cryptography and Network Security | Video | Dr. Debdeep Mukhopadhyay | IIT Kharagpur | Syllabus Course contents |
| Data Communication | Video | Prof. Ajit Pal | IIT Kharagpur | Syllabus Course contents |
| Data Communications | Web | Prof. H.S. Jamadagni | IISc Bangalore | Syllabus Course contents |
| Data Structures And Algorithms | Video | Prof. Naveen Garg | IIT Delhi | Syllabus Course contents |
| Data Structures and Program Methodology | Web | Dr. Pradip K Das Dr. S.V. Rao | IIT Guwahati | Syllabus Course contents |
| Database Design | Video | Dr. S. Srinath Prof. D. Janaki Ram | IIIT Bangalore IIT Madras | Syllabus Course contents |
| Design and Analysis of Algorithms | Web | Prof. Sundar Viswanathan Prof. Ajit A Diwan Prof. Abhiram G Ranade | IIT Bombay | Syllabus Course contents |
| Digital Image Processing | Web | Dr. G. Harit | IIT Kharagpur | Syllabus Course contents |
| Digital Systems | Web | Prof. N.J. Rao | IISc Bangalore | Syllabus Course contents |
| Discrete Mathematical Structures | Video | Prof. Kamala Krithivasan | IIT Madras | Syllabus Course contents |
| Graph Theory | Video | Dr. L. Sunil Chandran | IISc Bangalore | Syllabus Course contents |
| High Performance Computer Architecture | Video | Prof. Ajit Pal | IIT Kharagpur | Syllabus Course contents |
| High Performance Computing | Video | Prof. Mathew Jacob | IISc Bangalore | Syllabus Course contents |
| Indexing and Searching Techniques in Databases | Web | Dr. Arnab Bhattacharya | IIT Kanpur | Syllabus Course contents |
| Internet Technology | Video | Prof. Indranil Sengupta | IIT Kharagpur | Syllabus Course contents |
| Introduction to Computer Graphics | Video | Prof. Prem K Kalra | IIT Delhi | Syllabus Course contents |
| Introduction to Database Systems and Design | Web | Prof. P.Sreenivasa Kumar | IIT Madras | Syllabus Course contents |
| Introduction to Problem Solving and Programming | Web | Prof. S. Arun Kumar | IIT Delhi | Syllabus Course contents |
| Introduction to Problem Solving and Programming | Video | Prof. D. Gupta | IIT Kanpur | Syllabus Course contents |
| Low Power VLSI Circuits & Systems | Video | Prof. Ajit Pal | IIT Kharagpur | Syllabus Course contents |
| Microprocessors and Microcontrollers | Web | Prof. Krishna Kumar | IISc Bangalore | Syllabus Course contents |
| Natural Language Processing | Video | Prof. Pushpak Bhattacharyya | IIT Bombay | Syllabus Course contents |
| Numerical Optimization | Video | Dr. Shirish K. Shevade | IISc Bangalore | Syllabus Course contents |
| Operating Systems | Web | Prof. P.C.P. Bhatt | IISc Bangalore | Syllabus Course contents |
| Parallel Computer Architecture | Web | Dr. Mainak Chaudhuri | IIT Kanpur | Syllabus Course contents |
| Pattern Recognition | Web | Prof. V. Susheela Devi Prof. M. Narasimha Murty | IISc Bangalore | Syllabus Course contents |
| Performance Evaluation of Computer Systems | Video | Prof. Krishna Moorthy Sivalingam | IIT Madras | Syllabus Course contents |
| Principles of Programming Languages | Video | Prof. S. Arun Kumar | IIT Delhi | Syllabus Course contents |
| Program Optimization for Multi-core Architectures | Web | Prof. Rajat Moona Dr. Mainak Chaudhuri Prof. Sanjeev K Aggarwal | IIT Kanpur | Syllabus Course contents |
| Real Time Systems | Video | Prof. Rajib Mall | IIT Kharagpur | Syllabus Course contents |
| Real Time Systems | Web | Prof. Rajib Mall | IIT Kharagpur | Syllabus Course contents |
| Software Engineering | Video | Prof. N.L. Sarda Prof. Umesh Bellur Prof. Rushikesh K Joshi | IIT Bombay | Syllabus Course contents |
| Software Engineering | Web | Prof. Rajib Mall | IIT Kharagpur | Syllabus Course contents |
| System Analysis and Design | Video | Prof. V. Rajaraman | IISc Bangalore | Syllabus Course contents |
| System Analysis and Design | Web | Prof. V. Rajaraman | IISc Bangalore | Syllabus Course contents |
| Theory of Automata and Formal Languages | Web | Dr. Diganta Goswami | IIT Guwahati | Syllabus Course contents |
| Theory of Automata, Formal Languages and Computation | Video | Prof. Kamala Krithivasan | IIT Madras | Syllabus Course contents |
| Theory of Computation | Video | Prof. Somenath Biswas | IIT Kanpur | Syllabus Course contents |
| VLSI Design Verification and Test | Web | Dr. Santosh Biswas Prof. Jatindra Kumar Deka | IIT Guwahati | |
| Advanced Computer Graphics | Video | Prof. C. Sharat | IIT Bombay | Syllabus only |
| Bioinformatics | Web | Prof. Harish Karnick Dr. Arnab Bhattacharya Prof. Somenath Biswas | IIT Kanpur | Syllabus only |
| Combinatorics | Video | Dr. L. Sunil Chandran | IISc Bangalore | Syllabus only |
| Computer Security and Cryptography - I | Video | Prof. Bernard Menezes | IIT Bombay | Syllabus only |
| Design Verification and Test of Digital VLSI Circuits | Video | Dr. Santosh Biswas Prof. Jatindra Kumar Deka | IIT Guwahati | Syllabus only |
| Distributed Computing Systems | Web | Prof. Ananthanarayana V.S | NITK | Syllabus only |
| Game Theory | Video | Prof. Y. Narahari | IISc Bangalore | Syllabus only |
| Grid Computing | Web | Prof. D. Janaki Ram | IIT Madras | Syllabus only |
| Human-Computer Interaction | Web | Pradeep P Yammiyavar Dr.Samit Bhattacharya | IIT Guwahati | Syllabus only |
| Introduction to Cognitive Science | Video | Prof. Amitabha Mukerjee | IIT Kanpur | Syllabus only |
| Introduction To Optimization | Web | Prof. Keshava Prasad Halemane | NITK | Syllabus only |
| Introduction to Programming | Video | Prof. C. Sharat | IIT Bombay | Syllabus only |
| Mobile Computing | Web | Prof. R.K. Ghosh | IIT Kanpur | Syllabus only |
| Object Computing | Web | Dr. R. Nadarajan | PSG College of Technology | Syllabus only |
| Object Computing | Video | Dr. R. Nadarajan | PSG College of Technology | Syllabus only |
| Operating System | Video | Prof. Kumkum Garg | IIT Roorkee | Syllabus only |
| Parallel Algorithms | Video | Prof. R. Seethalakshmi Dr. N. Sairam | SASTRA University | Syllabus only |
| Pattern Recognition | Video | Prof. Sukhendu Das Prof. C.A. Murthy | IIT Madras Indian Statistical Institute | Syllabus only |
| Pattern Recognition | Web | Dr. C. Chandra Sekhar | IIT Madras | Syllabus only |
| Principles of Compiler Design | Video | Prof. Y.N. Srikanth | IISc Bangalore | Syllabus only |
| Riemann Hypothesis and its Applications | Video | Prof. Manindra Agrawal | IIT Kanpur | Syllabus only |
| Self-Stabilizing Distributed Algorithms | Web | Dr. Sushanta Karmakar | IIT Guwahati | Syllabus only |
| Software Architecture and Design | Web | Prof. T.V. Prabhakar | IIT Kanpur | Syllabus only |
| Storage Systems | Video | Dr. K. Gopinath | IISc Bangalore | Syllabus only |
| Biometrics | Video | Prof. Phalguni Gupta | IIT Kanpur | Under development |
| Parallel Computing | Video | Dr. Subodh Kumar | IIT Delhi | Under development |
Wednesday, 14 October 2015
Tuesday, 13 October 2015
Crypt Key
 "Crypt" means "encrypt" and "graphy" means "writing". Cryptography is the study of writing the code in an encrypted form.
"Crypt" means "encrypt" and "graphy" means "writing". Cryptography is the study of writing the code in an encrypted form. Security in Computer Networking
Consider the today's scenario of Internet where , there are more than 2 billion Internet users throughout the Globe.
People interacting with each other, exchanging mails, purchasing items
online and many other activities are being done over Internet online.
Thus there is a great need of securing the data of the users from the
bad commodity or person, or we can say this bad person as an Intruder.

Suppose there are 2 persons , James and Steve. They want to communicate over Internet. Lets consider a scenario, what can be there basic needs when they communicate.
First of all, they both surely wanted that the data they are
exchanging, must not be read by any third person, it should be between
them only.
Secondly, while transmitting the data, the message should not be
deleted, or modified. It should reach the destination in its original
form.
Thirdly, they both wants to verify that the person they are
communicating , is the legal person, with whom they wants to
communicate. Steve wants to make sure that the person on other side is
James only, and James wants to make sure, that he is communicating with
Steve only.
Taking these 3 scenarios, we can say that there are some basic needs of the communicating parties. These are :
1. Confidentiality :
The term confidentiality means that the meaning of the data must be
understood by the sender and the intended receiver only. As an Intruder
can steal the data during its transmission. Thus the message must be
encrypted, so the Intruder is unable to understand the message.
2. Integrity :
James and Steve wants to ensure that the data is not altered during
its transmission neither by an Intruder, nor accidentally. In Transport
Layer and Network Layer, we have checksum for error in the message. But
prior to that, Data Integrity is used for this purpose.
3. Authentication :
In real world, when you meet a person and talks to him, you both just
tell your name to each other, in order to verify each other identity.
But when you are communicating over Internet, and you cannot see the
other party, its very difficult to authenticate the identity of that
person. Thus Authentication includes verifying the identity of the
person to each other over Communication Medium.
4. Organisation Security :
As you must be aware, that now a days ,
almost every organisation's network is connected to the outer world
Internet. Thus an Intruder can get access of the Organisation Network,
he can deposit harmful malwares or worms in the end systems of the
organisation network, can access secret information of the organisation.
To secure organisation from such attacks, we have Firewalls and
Intrusion detection System in Computer Networks which we will cover in
our later posts.
Now lets have a look at what an Intruder can do and how it can harm the
network. Suppose James and Steve are communicating and they want to
ensure confidentiality, Data Integrity and Authentication. Now what
different things an Intruder can do.
i) Record the messages on the channel.
ii) Delete or Modify the original message during its transmission.
iii) Impersonating himself as someone else.
If proper measures are not taken, then an Intruder can attack in a
numerous number of ways. For example, if not properly encrypted, an
Intruder can steal your username and Password. He can do Denial of
Service ( DoS ) attack by overloading the network resources and
disabling other Network users to communicate. There are various other
attacks also. We will discuss each and there measure in detail , later
in this post and in the coming post.
Till now you must have understsood that there is a great need of
securing our data while transferring it over Communication medium. There
are various techniques to safeguard our data, these are known as Cryptography Techniques.
Cryptographic techniques are so much much developed in past 30-40 years,
that they themselves include Confidentiality, Integrity and
Authentication. So there is no need of applying for different security
algorithms to provide all these services individually.
Cryptography allows a sender to be-fool an Intruder by encrypting the
message in some other format using certain technique or algorithm. The
Intruder can be disguised, that he cannot get any information from the
data, if he is able to intercept it. Yes , the authenticated receiver
will be able to receive the original data from the disguised data.
Let us suppose , James and Steve wants to communicate. James wants to
send a message to Steve. For example: James wants to ask "How are you
Steve". Thus James message in original form is known as Plain text. James will use an encryption algorithm to encrypt his original message, to save it from the intruder attack. The encrypted message is known as Cipher Text. Cipher Text is not understandable by the intruder.
But as you know, in today's global world, almost all the encryption and
decryption algorithms are open to every person on the Internet. Even
intruder knows these algorithms.So if intruder knows the encryption
method, he could have easily decrypt the message. But still something is
there, that is preventing the intruder to decrypt and extract the
transmitted message, that is known as key.
A key can be anything like a string of characters or numbers etc. Say in this case, the encryption algorithm takes key A, message m as input and produces the cipher text as output. The cipher text here will be denoted as A(m).
Cipher Text ( C ) = A(m)
This means that the plain text, m is encrypted using a key A.
On the receiving side, Steve will provide a key B and the cipher text
to the decryption algorithm, that will generate the plain text.
Plain Text (m) = B (C)
or
we can also write it as , Plain Text (m) = B(A(m))
There are two types of encryption Algorithms.
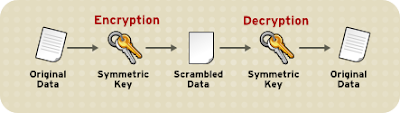
i) Symmetric Key Algorithm :
In these algorithms, both sender and receiver have the identical keys. They share it with each other secretly.
ii) Public Key Algorithm :
In these types of algorithms, sender and receiver make use of a pair of
keys. One of the keys is known to both sender and receiver and infact to
the rest of the world, and the other key is known only to one , either
sender or receiver, but not to both.
Let us start with our discussion over different encryption Algorithm.
First we will be going through Symmetric Key Algorithms and then moving
on to various public key encryption techniques.
Symmetric Key Algorithm in Cryptography
Till now what have you understand about Cryptography. It must be that
Cryptography is just putting one thing in place of the other using
certain techniques so that it should not be understood by any wrong
person. So we shall now look at various symmetric algorithms that are
almost 500 years old or more. For Symmetric Key cryptography algorithms ,
we will use key as K.
1. Caesar Cipher :
For example : James wants to send a message to Steve,
"James, Meet me at University, Steve".
Caesar Cipher will replace the every alphabet by its K letter
later in the alphabet. Say if key K=5. Then every alphabet in the plain
message will be replaced by its 5 letter later alphabet. Therefore in
this case, the cipher text will be as follows.
m= James, Meet me at University, Steve
K=5
Cipher Text ( C) = K(m) = K(5)
'J' will be replaced by 'O', 'a' will be replaced by 'f' and similarly
all the letters will be replaced. So our generated cipher text would be,
Cipher Text = Ofrjx, Rjjy rj fy Zsnajwxnyd, Xyjaj
Disadvantage of Caesar Cipher
Might be , the above Cipher text looks very difficult to read or
unintelligible. But as you know there are only 26 alphabets in English.
Thus if the intruder came to know that Caesar Cipher is used, then its
very easy for him to break the code, as there are only 25 key value
possible. So he can use hit and try method for 25 times and will surely
obtain the original message in one of its try.
2. Mono-Alphabetic Cipher :
Mono-alphabetic Cipher is an improvement over Caesar cipher. In Caesar
Cipher, we were only able to replace the letters according to a pattern (
substituting according to K ) . But in Mono-alphabetic Cipher, we can
replace the letters randomly. This means any letter can be substituted
for any letter, as long as for a single letter throughout the message,
same susbstitute must be used.
Lets take an Example of a mono-alphabetic Cipher.

The plain message, "James, Meet me at University, Steve" will be encrypted as ,
Cipher Text = pqdtl, Dttz dt qz Xfoctklozn, Lztct
Mono-alphabetic cipher can be extended to 26! ways to encrypt your text.
It is almost equal 10^26. Thus, even if the intruder knows , that you
have used Mono-alphabetic cipher algorithm, then using a Brute Force
Approach ( Hit and Trial Approach ) also, it will be very brainstorming
task for him to crack the code.
3. Poly-alphabetic Cipher :
One more improvement of Caesar Cipher was Poly-alphabetic Cipher. In
poly-alphabetic , we use 2 Caesar ciphers together. There are 2 keys
such as ( with K=3 and K=5). Now we can chose that how these 2 keys
should be used in a pattern. For Example: C1 , C1 , C2 , C2 , C1. The
1st letter will be encrypted using 1st encryption key, the second will
also be using 1st encryption key, 3rd will be using 2nd encryption key,
4th will use 2nd key also and the 5th letter will be encrypted using 1st
encryption key. And this pattern will be followed for the coming
letters also. Lets take our Example :
Plain Text (m) = "James, Meet me at the University, Steve".
Keys, K=3, K=5
Cipher Text (C) = Mdrjv, Phjy ph dy ykh Xsnyhuxnwb, Vyjyh
In Poly-alphabetic Cipher, the Encryption and the Decryption key is the
knowledge of the two ciphers i.e.(K=3 and K=5) and the pattern C1 , C1 , C2 , C2 , C1.
- Since now a days , technology and the communication over Internet has grown to that extent, that these Symmetric Key Cryptographic Techniques also don't work very effectively. As the 2 commodities communicating needs to share the key. Which is not feasible. Thus these techniques are hardly in use in today's world. The techniques which are currently in use are PGP or Public Key Encryption.
Public Key Cryptography

Securing Computer Networks using Public Key
In Public Key Cryptography, inspite of having a shared key between sender and receiver, there are 2 keys.
Let us Suppose, James is the sender and Steve is the receiver.
Steve will have 2 keys , one is Public Key- that is available to the whole world and the second is Private
Key- that is only known to Steve. We will use Us for the public key of Steve and Ks for the private key of Steve.
James in order to to send message to Steve securely, will 1st fetch the public key of Steve (that is known to everyone). Now James will encrypt message, m , using an encryption algorithm and the public key if Steve. That means, James will perform, Us (m). On receiving the encrypted message from James, Steve will use a decryption algorithm and his private key, to get the plain text. Steve will compute Ks(Us (m)). You can clearly see that, James and Steve can securely send message to each other, without sharing or distribution of any key ( that has to be done in Symmetric Key Cryptography).
Let us now start with some Public Key Encryption Algorithms.
RSA Encryption Algorithm
RSA was named after the scientists who developed it i.e. Ron Rivest , Adi Shamir , Leonard Adleman . Lets now see the working of of RSA. But before directly coming to the implementation of RSA, lets have a look at some mathematical calculations, as RSA makes a large use of modulo-n for computing and encrypting a data. In modulo, if you compute A modulo n, then the result will be the remainder lest after dividing A by n. For example : If you compute 24 mod 5, the result will be 4. There are various operations associated with modulo. These are as follows.
- [( (a mod n) + ( b mod n )] mod n = (a + b) mod n
- [( (a mod n) - ( b mod n )] mod n = (a - b) mod n
- [( (a mod n) * ( b mod n )] mod n = (a * b) mod n
- ( ( a mod n)^d ) mod n = ( a^d) mod n
Now to generate a public key and a private key in RSA algorithm, Steve will perform the following steps :
1. Choose two large prime numbers a and b.
Now a question arises, how large the numbers must be ? The answer is, as mush the numbers are large, the more harder is to break the RSA algorithm. But also, it will takes more time to compute encryption and decryption. Thus it is recommended that you use prime numbers of the order 1024 bits.
2. Calculate n = a * b and y = ( a-1) * ( b-1 )
3. Select a number e , less than n ( e < n ) such that e and n doesn't have any common factor other than 1. Hence m and n are said to be as relatively prime.
e will be used in encrypting the message.
- 5 and 11 are relatively prime , as they have only 1 as common factor.
4. Find a number z such that ez-1 is exactly divisible by y. We can also write it as that select z such that
ez mod y =1.
z will be used decrypting the message.
5. Now the public and the private key of Steve are ready. The public key , Us that will be available to the whole world is ( n, e) and his private key , Ks is ( n, z ).
\

James is sending a message m to
Steve. Message will be represented by some integer that can be
mathematically computed. Thus James will encrypt the message in this
way.
Cipher text or Encrypted Message ( c ) = ( m^e ) mod n
The bit pattern corresponding to c, will be sent to Steve.
On the receiving side, to get the original message, Steve will decrypt it in the following way.
Plain text ( m ) = ( c^z ) mod n.
Let us take an Example that will make clear , how the RSA algorithm works.
Suppose James has a message , m=5 that he wants to send to Steve. So he start with RSA algorithm.
1. He chooses two prime numbers, say a = 17 and b = 7 .
2. Calculate n= a * b= 17 * 7 = 119 and y = ( 17-1 ) * ( 7-1 ) = 16 * 6 = 96.
3. Select e=5. Thus 5 and 119 are relatively prime.
4. To calculate in order to fulfill ez mod y=1. We will get z as 77.
5. Therefore Steve public key = ( 119, 5) and private key = ( 119, 77).
Thus while encrypting the message before sending it, James will do the following computation.
Cipher Text ( c ) = ( m^e) mod n = ( 5^5) mod 119 = 3125 mod 119 = 31
On the receiving side, while decrypting the cipher text, Steve will do the following computation.
Plain Text ( m ) = (c^z) mod n = ( 31^77) mod 119 = 5
So you must have noticed that , RSA is secure in the sense, there are numerous number of prime numbers are there for computation. Hence it will be a very brainstorming task for an Intruder to break the code and get the plain text.
Transport Layer 4
Introduction to Transport Layer
Before starting with our discussion on Transport Layer, I want to give you a live scenario, that will make you clear with the working of Transport Layer and the other layers of the Internet stack.
Let us suppose that there are two bungalows. One is in India and Other
is in America. In the bungalow in India, lives a person James along with
his 5 children. And in the bungalow in America, lives a person Steve
along with his 4 children. Now all 5 children of James write a letter to every children of Steve on every Sunday. Therefore total number of letters will be 20.
Thus, all the children writes the letter , put them in envelopes and
hand over it to James. Then James write source house address and the
destination house address on the envelope and give it to the postal
service of India. Now the postal service of India puts some other
addresses corresponding to the country and delivers it to the America
postal Service. The American Postal sees the destination address on the
envelopes and will deliver those 20 letters to the Steve House. Steve
collects the letter from the postman and after considering the name of
his respective children on the envelopes, he gives the letter to each of
them.
In this example we have processes and the layers. Let me explain.
Processes = children
Application Layer messages = envelopes
Hosts = The two Bungalows
Transport Layer Protocol = James and Steve
Network Layer protocol = Postal Service
- Here you can see, that according to children, James and Steve are the mail services, but in real they are just a part of the delivery process.
Suppose James and Steve went on a holiday for 10 days. Then as their
susbstitute, Angelina comes at place of James and Ashley comes at place
of Steve. But now for the two bungalows, unfortunately Angelina and
Ashley are not able of providing services as James and Steve. Angelina
and Ashley often drops letters, lose them, which are often eaten by the
dogs. Thus in the same way , services provided by the Transport Layer depends on type of protocol you use in your network.
- In this scenario, for example if the postal service cannot guarantee the maximum time taken in the delivery of the envelopes, thus there is no way that James and Steve can guarantee the maximum delays in the delivery of mails between the children. In the same way, the services provided by the Transport Layer are often subjected to the services provide by the underlying network layer. If the network layer cannot guarantee the delay in delivery of messages, then surely transport layer can never.
But still, a Transport Layer protocol guarantees certain services that are not guaranteed by the underlying Network Layer.
Thus, in our coming posts on transport layer and the other layers, you
must always remember this example, making it easier for you to
understand the layers concept.
Overview of Transport Layer Protocol:
Transport Layer acts as a medium
between the Application Layer and the the Network Layer. Transport Layer
provides a logical communication medium between the processes running
on different end systems. What does logical communication means?
Logical communication means that,
from an Application perspective, it is like the hosts are directly
connected to each other, but in reality , the hosts may be on two
opposite sides of the earth, connected by routers and links. As the
physical infrastructure of the two hosts and the intermediate can be
different, so for this reason , the Application processes use the
logical communication of the Transport Layer to send message from one
host to other and be free from the worry of the physical infrastructure
used.
Different Protocols of Transport Layer:
There are basically two types of protocols that Transport provides to give services to Application Layer. These are:
1. Transmission Control Protocol (TCP)
2. User Datagram Protocol (UDP)
TCP provides a reliable and
connection-oriented service to the Application. On the other hand, UDP
provides a unreliable and connection-less service to the Application.
Thus, it is upto the Application Developer, which transport Layer
protocol has to be used. For example: In case of HTTP, it is built over
TCP.
Transmission Control Protocol (TCP):
1. TCP provides a reliable delivery
of data. Irrespective of the fact, Network layer doesn't provides
reliable data transfer, TCP guarantees that. But TCP doesn't guarantee
anything about the time taken to deliver the packet.
2. TCP delivers the packet in their
respective order. This means, from the source, in the order in which you
will send the packet, they will reach in the same order at the
destination.
3. As TCP provides reliable data transfer and connection oriented services, it is a bit heavy and complex protocol.
4. TCP provides congestion control or the flow control within a network.
User Datagram Protocol (UDP):
1. UDP provides non-reliable data delivery. It is a connection-less service provider.
2. UDP doesn't guarantee the delivery of packets in the order they are sent.
3. Its a light protocol.
4. TCP provides congestion control or the flow control within a network.
User Datagram Protocol (UDP):
1. UDP provides non-reliable data delivery. It is a connection-less service provider.
2. UDP doesn't guarantee the delivery of packets in the order they are sent.
3. Its a light protocol.
On one hand , the Transport Layer provides communication between processes, whereas on the other hand, the Network Layer provides communication between hosts. Recall the above example of two bungalows and compare it with that. I am sure, you will understand it
TCP
Transmission Control Protocol (TCP)
Coming to the 2nd Transport Layer Protocol i.e. Transmission Control Protocol (TCP). The Transmission Control Protocol is such an important protocol in the Internet protocol model, that the whole Internet stack is called as the TCP/IP stack. TCP was 1st introduced in 1974.A number of applications use TCP for their execution such as HTTP, FTP, SMTP. Web Browser uses TCP to connect to the World Wide Web (www). TCP is used to deliver mails and transfer files from one host to another.
TCP is called as Connection-Oriented Protocol. Because in TCP, there is a 3-way handshake between the communicating hosts before exchanging the data or the message. There are lots of services provided by TCP that were not available by UDP. TCP provides Reliable Delivery of data, checks for error in the data and tries for its correction, delivers the packet in their respective order as they were sent by the sender. TCP also provides congestion control and flow control.
TCP provides a full-duplex mode of transmission i.e. if there is a connection between a Process Y on one host and a Process Z on another host. Then the Application message can be sent from Process Y to Process Z and from Process Z to Process Y within the same TCP connection.
A TCP connection is between a single sender and a single receiver. That means, TCP is a point-to-point connection control protocol. Multi-casting is not possible with TCP. Multi-catsing is a procedure of sending of data from a single sender to different receiver in a single send operation.
Problems with TCP:
Due to large traffic and congestion in the network, packets might get lost or they can get corrupt. TCP being the reliable data delivery protocol, detects all these problems, try to resolve them, asks for the re-transmission of the lost or corrupt packets, arranges the packet in order and send them to the receiver. The TCP receiver arranges all these packets in order and send them to the Application.
Thus in all this, re-transmissions , in order packet delivery, sometimes TCP results in long delays.
How TCP provides Reliable Delivery of Data:
TCP does it by a process of positive Acknowledgement. The receiver has to acknowledge the sender by sending a message to the sender, if it has receive the data correctly. The sender keeps the record of every packet it sends and maintains a clock with every packet. If the acknowledgment doesn't comes before the clock expires, the sender will re-transmit that packet, assuming that the packet is either lost or corrupted.
TCP Packet Structure:
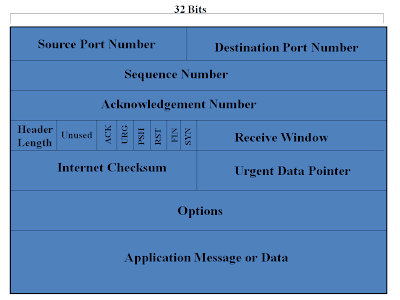
1. Source Port Number: It is used to identify the sending port number.
2. Destination Port Number: It is used to identify the receiving port Number.
3. Sequence Number and Acknowledgement Number : These are used for the reliable Delivery of data. Each Sequence and Acknowledgement Number is of 32 bits.
4. Header Length : This field is of 4 bytes. It tells the length of the TCP Header. The TCP header can be of variable lengths due to the presence of Option Fields. (In most cases, option field is empty, then the TCP header length is 20 bytes).
5. Unused or Reserved : This is reserved for future use. It is of 3 bit.
6. Pointers:
- ACK: This bit is used to indicate that whether the value in Acknowledgement field is valid or not. That means, whether it contains an acknowledgment number for a packet that has been successfully received.
- RST, SYN and FIN : These 3 bits are used for establishing a connection between and to stop a connection.
- PSH : This bit indicates whether the data should be pass to the upper layer or not. If PSH=1, it indicates the receiver should pass the data immediately to the upper layer.
- URG: This bit is used to indicate , if there is any data , that the host has marked as urgent. If URG=1, then it shows that some data has been marked as urgent. To know the address of that Urgent data, the 16-bit Urgent Data Pointer field is used which gives that information.
7. Checksum: It is of 16 bits. It is used to check that whether the data has arrived correctly or not. It is also used to detect any error in the data.
8. Application Message: It is of 32 bits. It contains the actual Application that the user wants to transmit.
9. Options : This field is of 32 bits. If the user need to send a data that is larger that the Application Message field size, then option field is used by the TCP header.
- It is recommended that you must send small packets, because if the packet size is larger, than the packet fragmentation will take place at the network layer, resulting in more number of lost packets.
TCP Implementation:
TCP is implemented in different ways. These are:
i) TCP TAHOE
ii) TCP RENO
iii) TCP VEGAS
iv) TCP SACK
We will discuss all these in details in our coming posts.
Concept of Sequence Number and Acknowledgement Number
These two numbers are of great importance in TCP. As they enable TCP for reliable Data Delivery and in order Delivery of Packets. Lets take a look and try to understand, what are these two fields .First of all, I would like to tell you that, TCP Sequence and Acknowledgement Number doesn't hold the size or number of transmitted packet , instead they contain the byte stream of those packets. That means , Sequence and Acknowledgement number contains the 1st byte of the transmitted packet.
The sender and the receiver decides on , what should be the starting sequence number of the 1st packet.
Sequence Numbers:
For Example : If you have a 50,000 bytes of data to send and the Maximum Segment Size (MSS) is 1000 bytes, you have to send 50 packets. Suppose you and the receiver decide the starting sequence number of 1st packet as 0. The second packet will have sequence number as 1000, 3rd will have 2000 and so on till 50000.
- MSS refers to the maximum size of a TCP packet that can be sent.
Acknowledgement Number:
As we have already discussed that TCP is full Duplex, so at the same
time both sender and receiver can send packets to each other
simultaneously. Let us Suppose that James is the sender and Steve is the receiver.
All the packets arriving from James, has a sequence number for the data
flowing from James to Steve. Now the Acknowledgment number that Steve
puts in its packet is the sequence number of the next packet, that Steve
is expecting from James.
For Example: If Steve has received all bytes numbered from 0 to 499 from
James. Then Steve will put the acknowledgement number as 500 in the
packet , it will send to James.
Cumulative Acknowledgement:
For Example: If Steve has received bytes numbered from 0 to 499 and
bytes from 1000 to 1099. Due to some failure or packet loss, Steve has
not received packet from 500 to 999 and Still he is waiting for 500
segment, to build the whole message from James in a proper order. Thus
Steve's next packet will contain acknowledgment number as 500. Since TCP
only acknowledges the 1st byte missing, this is known as Cumulative Acknowledgement.
This also brings one more concern, that when Steve receives packet from 0
to 499 and then from 1000 to 1099, but packet from 500 to 999 is still
missing. Thus the 3rd packet arrives out of order. Now a question
arises: What should the receiver do when it receives a packet out of order?
Thus , I would like to bring the fact to you that, Computer networking
doesn't impose any restriction on this. It totally depends on the people
programming the TCP implementation. They can choose either of these:
1. The receiver can discard the out-of-order packet as soon as he receives it.
or
2. The receiver can save the out of order packet in its buffer and waits for the missing packet to arrive.
- Hopefully maximum people will choose the 2nd option , in order to use the network bandwidth to the maximum, and to shorten the delay process. In Internet, the 2nd choice is used .
*****There are various interesting cases,
where you sometimes have to re-transmit and sometimes you need not
re-transmit a packet due to acknowledgment. Lets have a look at these
scenarios.
Scene 1: Re-transmission due to lost Acknowledgment :

Scene 2: Cumulative Acknowledgment avoids re-transmission of the 1st packet.
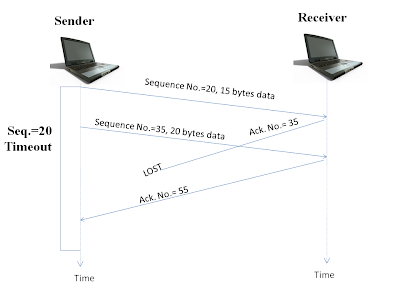
Suppose, sender sends a
packet of 15 bytes and a packet of 20 bytes back to back and they are
received at the receivers side and the receiver sends an acknowledgement
for the same. But the acknowledgment for the 1st packet is lost in the
network. But before the timeout occurs, the sender receives an
acknowledgment for the 2nd packet. Thus, the sender will understand,
that the sender has received all the packets till Sequence number 54.
Hence it will not resend the 1st packet.
Subscribe to:
Comments (Atom)
