Friday, 31 July 2015
Friday, 24 July 2015
MSDN
Diagnostic Tools debugger window in Visual Studio 2015
Diagnostic Tools debugger window in Visual Studio 2015
:(
Supported project types and configurations
The following startup project types and debugging configurations are
supported by the Diagnostic Tools window in Visual Studio 2015 CTP 5:
- Managed WPF, WinForms, Console projects running locally
- Native Win32, Console, and MFC projects running locally
- Note: the Debugger Events tool is currently not supported for Native projects
- ASP.NET 4 using IIS Express
- Managed or Native 32-bit Windows Store projects running locally
The Diagnostic Tools window currently does not support:
- ASP.NET 5 projects, or ASP.NET 4 projects using IIS
- Windows Store projects that are 64-bit, using JavaScript, or running on a remote device
- Targeting remote devices
http://blogs.msdn.com/b/visualstudioalm/archive/2014/11/13/memory-usage-tool-while-debugging-in-visual-studio-2015.aspx
http://blogs.msdn.com/b/visualstudioalm/archive/2015/01/16/diagnostic-tools-debugger-window-in-visual-studio-2015.aspx
Googlez
How Google works - Book Review
To this day the rule of thumb is that late half of Google employees should be engineers.
Jonathan has plenty of experience in the "gate based" approach to building product which in most companies entails a series of well defined phases and milestone, governed by various executive reviews that escalate slowly up the corporate food chain . This approach is designed to conserve resource san funnel information up from far-flung silos to small set of design-makers.
Google engineers are business savvy and possessed a healthy streak of creativity.
Hire the best engineers and get out of their way.
How Google was able to beat Microsoft 11 billion dollar challenge is explained.
Why product excellence is required.
Cost of experimentation and failure has dropped significantly.
http://www.wsj.com/articles/book-review-how-google-works-by-eric-schmidt-and-jonathan-rosenberg-1412371982
"company is a symbol of innovation, success and technology leadership."
Anyone managing technology-focussed team should read this book, though not all the lessons will translate outside of Google's unique culture or the era when many of the decisions were made.
If you believe that Google sees the world as zeros and ones and manages that way, this book should serve to ground you in the potential challenges faced by management trying to see decision-making programmatically. What you will find is a framework held together by talented engineers, supported by an insatiable demand for data, and acted on with a set of principles that aren’t always as binary as “smart creatives” might prefer.
http://www.economist.com/news/books-and-arts/21620056-search-giant-shares-some-its-business-methods-dont-be-modest
Though it is not discussed in the book, Google’s management philosophy doubtless springs from the careers of the founders, Sergey Brin and Larry Page. Their youth, vision and technical genius, together with Google’s vast wealth, enabled the company to take risks that others would never contemplate. This is why it vies to photograph every street in the world and scan every book ever published, to say nothing of building self-driving cars and glasses that record almost everything.
In large part Google grew because it threw out the traditional MBA playbook; its success speaks for itself. However, this underscores a shortcoming of “How Google Works”. The experience of Messrs Schmidt and Rosenberg is so coloured by Google’s accomplishments that many of their recommendations best apply to managing teams of aces in lucrative, fast-growing markets, not to overseeing a wide range of talent in low-margin businesses—the life of most managers.
Androidz
Solution for Android SDK Manager not opening in Windows 8
I have installed windows 8 in my laptop and tried to open ‘Android SDK Manager’. It was not open. By googling I found the solution as below.
Solution:- Go to android-sdk folder what you had set path under windows->preference menu for android.
Edit android.bat file.
Find java_exe=
And in front of add Java.exe path like “C:\Program Files (x86)\Java\jdk1.6.0\bin\java.exe”
HTML
How to display Progress bar while page is loading
<pre>
<code>
protected void Page_Load(object sender, EventArgs e)
{
showPageLoad();
//do somthing
{
showPageLoad();
//do somthing
}
private void showPageLoad()
{
int i=0;
Response.Write(“<div=’divTitle’>Loading(<span id=’message’>0%</span>)</div>”);
Response.Flush();
for(i=5;i<=100;i=i+5)
{
System.Threading.Thread.Sleep(200);// any codes can be typed here
outputflash(i.ToString() + “%”);
Response.Flush();
}
}
private void removePageLoad()
{
ScriptManager.RegisterStartupScript(Page, this.GetType(), “deleteLoading”, “var d = document.getElementById(‘divTitle’);d.parentNode.removeChild(d);”, true);
private void showPageLoad()
{
int i=0;
Response.Write(“<div=’divTitle’>Loading(<span id=’message’>0%</span>)</div>”);
Response.Flush();
for(i=5;i<=100;i=i+5)
{
System.Threading.Thread.Sleep(200);// any codes can be typed here
outputflash(i.ToString() + “%”);
Response.Flush();
}
}
private void removePageLoad()
{
ScriptManager.RegisterStartupScript(Page, this.GetType(), “deleteLoading”, “var d = document.getElementById(‘divTitle’);d.parentNode.removeChild(d);”, true);
}
private void outputflash(string value)
{
Response.Write(“<scriptpe=’text/javascript’>document.getElementById(‘message’).innerHTML='” + value + “‘;</script>”);
private void outputflash(string value)
{
Response.Write(“<scriptpe=’text/javascript’>document.getElementById(‘message’).innerHTML='” + value + “‘;</script>”);
}
</code></pre>
FTP
How to Download / Upload Files on FTP Server
Require following ftp details where you want to upload the files:
FTP URL: “ftp://ftp.yoursite.com/”
FTP Username: username
FTP Password: password
FTP Port: 21
Upload File
public string UploadFile(string FtpUrl, string fileName, string userName, string password, string UploadDirectory = "")
{
string PureFileName = new FileInfo(fileName).Name;
String uploadUrl = String.Format("{0}{1}/{2}", FtpUrl, UploadDirectory, PureFileName);
FtpWebRequest req = (FtpWebRequest)FtpWebRequest.Create(uploadUrl);
req.Proxy = null;
req.Method = WebRequestMethods.Ftp.UploadFile;
req.Credentials = new NetworkCredential(userName, password);
req.UseBinary = true;
req.UsePassive = true;
byte[] data = File.ReadAllBytes(fileName);
req.ContentLength = data.Length;
Stream stream = req.GetRequestStream();
stream.Write(data, 0, data.Length);
stream.Close();
FtpWebResponse res = (FtpWebResponse)req.GetResponse();
return res.StatusDescription;
}
public static string DownloadFile(string FtpUrl,string FileNameToDownload,
string userName, string password,string tempDirPath)
{
string ResponseDescription = "";
string PureFileName = new FileInfo(FileNameToDownload).Name;
string DownloadedFilePath = tempDirPath+"/"+PureFileName;
string downloadUrl = String.Format("{0}/{1}", FtpUrl, FileNameToDownload);
FtpWebRequest req = (FtpWebRequest)FtpWebRequest.Create(downloadUrl);
req.Method = WebRequestMethods.Ftp.DownloadFile;
req.Credentials = new NetworkCredential(userName, password);
req.UseBinary = true;
req.Proxy = null;
try
{
FtpWebResponse response = (FtpWebResponse)req.GetResponse();
Stream stream = response.GetResponseStream();
byte[] buffer = new byte[2048];
FileStream fs = new FileStream(DownloadedFilePath, FileMode.Create);
int ReadCount = stream.Read(buffer, 0, buffer.Length);
while (ReadCount > 0)
{
fs.Write(buffer, 0, ReadCount);
ReadCount = stream.Read(buffer, 0, buffer.Length);
}
ResponseDescription = response.StatusDescription;
fs.Close();
stream.Close();
}
catch(Exception e)
{
Console.WriteLine(e.Message);
}
return ResponseDescription;
}
SQL
Creating Transaction SQL Server
BEGIN TRANSACTION
BEGIN TRY
-- put SQL commands here INSERT/UPDATE/Delete
-- if successful - COMMIT the work
COMMIT TRANSACTION
END TRY
BEGIN CATCH
-- handle the error case (here by displaying the error)
SELECT
ERROR_NUMBER() AS ErrorNumber,
ERROR_SEVERITY() AS ErrorSeverity,
ERROR_STATE() AS ErrorState,
ERROR_PROCEDURE() AS ErrorProcedure,
ERROR_LINE() AS ErrorLine,
ERROR_MESSAGE() AS ErrorMessage
-- in case of an error, ROLLBACK the transaction
ROLLBACK TRANSACTION
-- if you want to log this error info into an error table - do it here
-- *AFTER* the ROLLBACK
END CATCH
Wednesday, 15 July 2015
STOCKS
The Indian market trend comes handy
Guruji.com the most powerful Indian search engine and India's Number one music search engine
has yet another feature that proves itself. Guruji finance offers most
interesting and a powerful market trend analysis site can be used as a
powerful market analysis tool to forecast and predict the future returns
about various equities,mutual fund and commodities. Google finance also
has a similar interface but not suitable for the Indian market as the
data fetch by it is delayed for India market.
Lets showcases some of the best usages and tools that is offered by Guruji finance.
2. Search and get performance of a particular stock
Lets showcases some of the best usages and tools that is offered by Guruji finance.
- Sensex, Nifty Chart
- Portfolio,Watchlist and Finance
- News and Research about a particular equity
- Top gainers and losers
- Sector wise performance
- Mutual funds
- Futures
- World currency
- Search for a particular stock
- Create Portfolio and track your stocks with real time data and analysis
LINUX NETWORKING COMMANDS
Linux is most powerful operating system which often needs to use commands to explore it effectively.Some of the commands are restricted to normal user groups as they are powerful and has more functionality involved in it.Here we summarized most interesting and useful networking commands which every linux user are supposed to be familiar with it.
1.Arp manipulates the kernel’s ARP cache in various ways. The primary options are clearing an address mapping entry and manually setting up one. For debugging purposes, the arp program also allows a complete dump of the ARP cache.ARP displays the IP address assigned to particular ETH card and mac address
2.Ifconfig is used to configure the network interfaces. Normally we use this command to check the IP address assigned to the system.It is used at boot time to set up interfaces as necessary. After that, it is usually only needed when debugging or when system tuning is needed.
[fasil@smashtech ~]# /sbin/ifconfig
eth0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:126341 errors:0 dropped:0 overruns:0 frame:0
TX packets:44441 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
3. Netstat prints information about the networking subsystem. The type of information which is usually printed by netstat are Print network connections, routing tables, interface statistics, masquerade connections, and multicast.
[fasil@smashtech ~]# netstat
Active Internet connections (w/o servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 .230.87:https ESTABLISHED
Active UNIX domain sockets (w/o servers)
Proto RefCnt Flags Type State I-Node Path
unix 10 [ ] DGRAM 4970 /dev/log
unix 2 [ ] DGRAM 6625 @/var/run/hal/hotplug_socket
unix 2 [ ] DGRAM 2952 @udevd
unix 2 [ ] DGRAM 100564
unix 3 [ ] STREAM CONNECTED 62438 /tmp/.X11-unix/X0
unix 3 [ ] STREAM CONNECTED 62437
unix 3 [ ] STREAM CONNECTED 10271 @/tmp/fam-root-
unix 3 [ ] STREAM CONNECTED 10270
unix 3 [ ] STREAM CONNECTED 9276
unix 3 [ ] STREAM CONNECTED 9275
4.ping command is used to check the connectivity of a system to a network.Whenever there is problem in network connectivity we use ping to ensure the system is connected to network.
[root@smashtech ~]# ping google.com
PING google.com (74.125.45.100) 56(84) bytes of data.
64 bytes from yx-in-f100.google.com (74.125.45.100): icmp_seq=0 ttl=241 time=295 ms
64 bytes from yx-in-f100.google.com (74.125.45.100): icmp_seq=1 ttl=241 time=277 ms
64 bytes from yx-in-f100.google.com (74.125.45.100): icmp_seq=2 ttl=241 time=277 ms
--- google.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 6332ms
rtt min/avg/max/mdev = 277.041/283.387/295.903/8.860 ms, pipe 2
5.Nslookup is a program to query Internet domain name servers. Nslookup has two modes: interactive and non-interactive. Interactive mode allows the user to query name servers for information about various hosts and domains or to print a list of hosts in a domain. Non-interactive mode is used to print just the name and requested information for a host or domain.
[fasil@smashtech ~]# nslookup google.com
Server: server ip
Address: gateway ip 3
Non-authoritative answer:
Name: google.com
Address: 209.85.171.100
Name: google.com
Address: 74.125.45.100
Name: google.com
Address: 74.125.67.100
6. dig (domain information groper) is a flexible tool for interrogating DNS name servers. It performs DNS lookups and displays the answers that are returned from the name server(s) that were queried. Most DNS administrators use dig to troubleshoot DNS problems because of its flexibility, ease of use and clarity of output. Other lookup tools tend to have less functionality than dig.
[fasil@smashtech ~]# dig google.com
; <<>> DiG 9.2.4 <<>> google.com
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4716
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 122 IN A 74.125.45.100
google.com. 122 IN A 74.125.67.100
google.com. 122 IN A 209.85.171.100
;; AUTHORITY SECTION:
google.com. 326567 IN NS ns3.google.com.
google.com. 326567 IN NS ns4.google.com.
google.com. 326567 IN NS ns1.google.com.
google.com. 326567 IN NS ns2.google.com.
;; ADDITIONAL SECTION:
ns1.google.com. 152216 IN A 216.239.32.10
ns2.google.com. 152216 IN A 216.239.34.10
ns3.google.com. 152216 IN A 216.239.36.10
ns4.google.com. 152216 IN A 216.239.38.10
;; Query time: 92 msec
;; SERVER: 172.29.36.1#53(172.29.36.1)
;; WHEN: Thu Mar 5 14:38:45 2009
;; MSG SIZE rcvd: 212
7.Route manipulates the IP routing tables. Its primary use is to set up static routes to specific hosts or networks via an interface after it has been configured with the ifconfig program.When the add or del options are used, route modifies the routing tables. Without these options, route displays the current contents of the routing tables.
[fasil@smashtech ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
54.192.56.321 * 255.255.255.0 U 0 0 0 eth0
* 255.255.0.0 U 0 0 0 eth0
default 0.0.0.0 UG 0 0 0 eth0
8.Traceroute : Internet is a large and complex aggregation of network hardware, connected together by gateways. Tracking the route one’s packets follow (or finding the miscreant gateway that’s discarding your packets) can be difficult.
Traceroute utilizes the IP protocol ‘time to live’ field and attempts to elicit an ICMP TIME_EXCEEDED response from each gateway along the path to some host. The only mandatory parameter is the destination host name or IP number. The default probe datagram length is 40 bytes, but this may be increased by specifying a packet length (in bytes) after the destination host name.
[fasil@smashtech ~]# traceroute google.com
traceroute: Warning: google.com has multiple addresses; using 209.85.171.100
traceroute to google.com (209.85.171.100), 30 hops max, 38 byte packets
1 * * *
9.W-displays information about the users currently on the machine, and their processes. The header shows, in this order, the current time, how long the system has been running, how many users are currently logged on, and the system load averages for the past 1, 5, and 15 minutes.
[fasil@smashtechl ~]# w
15:18:22 up 4:38, 3 users, load average: 0.89, 0.34, 0.19
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root :0 - 10:41 ?xdm? 24:53 1.35s /usr/bin/gnome-session
root pts/1 :0.0 10:58 1.00s 0.34s 0.00s w
root pts/2 :0.0 12:10 23:32 0.03s 0.03s bash
10. Nmap is designed to allow system administrators and curious individuals to scan large networks to determine which hosts are up and what services they are offering. nmap supports a large number of scanning techniques such as:UDP, TCP connect(), TCP SYN (half open), ftp proxy (bounce attack), ICMP (ping sweep), FIN, ACK sweep, Xmas Tree,SYN sweep, IP Protocol, and Null scan. See the Scan Types section for more details. nmap also offers a number of advanced features such as remote OS detection via TCP/IP fingerprinting, stealth scanning, dynamic delay and retransmission calculations, parallel scanning, detection of down hosts via parallel pings, decoy scanning, port filtering detection, direct (non-portmapper) RPC scanning, fragmentation scanning, and flexible target and port specification.
Significant effort has been put into decent nmap performance for non-root users. Unfortunately, many critical kernel interfaces (such as raw sockets) require root privileges. nmap should be run as root whenever possible (not setuid root, of course).
The result of running nmap is usually a list of interesting ports on the machine(s) being scanned (if any). Nmap always gives the port’s "well known" service name (if any), number, state, and protocol. The state is either"open", "filtered", or "unfiltered". Open means that the target machine will accept() connections on that port.Filtered means that a firewall, filter, or other network obstacle is covering the port and preventing nmap from determining whether the port is open. Unfiltered means that the port is known by nmap to be closed and no fire-wall/filter seems to be interfering with nmap’s attempts to determine this. Unfiltered ports are the common case and are only shown when most of the scanned ports are in the filtered state.
Depending on options used, nmap may also report the following characteristics of the remote host: OS in use, TCP sequentiality, usernames running the programs which have bound to each port, the DNS name, whether the host is a smurf address, and a few other--Network exploration tool and security scanners.
[fasil@smashtech ~]# nmap 52.194.69.152
Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2009-03-05 15:21 IST
Interesting ports on 52.194.69.152
(The 1658 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
22/tcp open ssh
111/tcp open rpcbind
Linux is most powerful operating system which often needs to use commands to explore it effectively.Some of the commands are restricted to normal user groups as they are powerful and has more functionality involved in it.Here we summarized most interesting and useful networking commands which every linux user are supposed to be familiar with it.
1.Arp manipulates the kernel’s ARP cache in various ways. The primary options are clearing an address mapping entry and manually setting up one. For debugging purposes, the arp program also allows a complete dump of the ARP cache.ARP displays the IP address assigned to particular ETH card and mac address
| [fasil@smashtech ]# arp Address HWtype HWaddress Flags Mask Iface 59.36.13.1 ether C eth0 |
2.Ifconfig is used to configure the network interfaces. Normally we use this command to check the IP address assigned to the system.It is used at boot time to set up interfaces as necessary. After that, it is usually only needed when debugging or when system tuning is needed.
[fasil@smashtech ~]# /sbin/ifconfig
eth0 UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:126341 errors:0 dropped:0 overruns:0 frame:0
TX packets:44441 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
3. Netstat prints information about the networking subsystem. The type of information which is usually printed by netstat are Print network connections, routing tables, interface statistics, masquerade connections, and multicast.
[fasil@smashtech ~]# netstat
Active Internet connections (w/o servers)
Proto Recv-Q Send-Q Local Address Foreign Address State
tcp 0 0 .230.87:https ESTABLISHED
Active UNIX domain sockets (w/o servers)
Proto RefCnt Flags Type State I-Node Path
unix 10 [ ] DGRAM 4970 /dev/log
unix 2 [ ] DGRAM 6625 @/var/run/hal/hotplug_socket
unix 2 [ ] DGRAM 2952 @udevd
unix 2 [ ] DGRAM 100564
unix 3 [ ] STREAM CONNECTED 62438 /tmp/.X11-unix/X0
unix 3 [ ] STREAM CONNECTED 62437
unix 3 [ ] STREAM CONNECTED 10271 @/tmp/fam-root-
unix 3 [ ] STREAM CONNECTED 10270
unix 3 [ ] STREAM CONNECTED 9276
unix 3 [ ] STREAM CONNECTED 9275
4.ping command is used to check the connectivity of a system to a network.Whenever there is problem in network connectivity we use ping to ensure the system is connected to network.
[root@smashtech ~]# ping google.com
PING google.com (74.125.45.100) 56(84) bytes of data.
64 bytes from yx-in-f100.google.com (74.125.45.100): icmp_seq=0 ttl=241 time=295 ms
64 bytes from yx-in-f100.google.com (74.125.45.100): icmp_seq=1 ttl=241 time=277 ms
64 bytes from yx-in-f100.google.com (74.125.45.100): icmp_seq=2 ttl=241 time=277 ms
--- google.com ping statistics ---
3 packets transmitted, 3 received, 0% packet loss, time 6332ms
rtt min/avg/max/mdev = 277.041/283.387/295.903/8.860 ms, pipe 2
5.Nslookup is a program to query Internet domain name servers. Nslookup has two modes: interactive and non-interactive. Interactive mode allows the user to query name servers for information about various hosts and domains or to print a list of hosts in a domain. Non-interactive mode is used to print just the name and requested information for a host or domain.
[fasil@smashtech ~]# nslookup google.com
Server: server ip
Address: gateway ip 3
Non-authoritative answer:
Name: google.com
Address: 209.85.171.100
Name: google.com
Address: 74.125.45.100
Name: google.com
Address: 74.125.67.100
6. dig (domain information groper) is a flexible tool for interrogating DNS name servers. It performs DNS lookups and displays the answers that are returned from the name server(s) that were queried. Most DNS administrators use dig to troubleshoot DNS problems because of its flexibility, ease of use and clarity of output. Other lookup tools tend to have less functionality than dig.
[fasil@smashtech ~]# dig google.com
; <<>> DiG 9.2.4 <<>> google.com
;; global options: printcmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 4716
;; flags: qr rd ra; QUERY: 1, ANSWER: 3, AUTHORITY: 4, ADDITIONAL: 4
;; QUESTION SECTION:
;google.com. IN A
;; ANSWER SECTION:
google.com. 122 IN A 74.125.45.100
google.com. 122 IN A 74.125.67.100
google.com. 122 IN A 209.85.171.100
;; AUTHORITY SECTION:
google.com. 326567 IN NS ns3.google.com.
google.com. 326567 IN NS ns4.google.com.
google.com. 326567 IN NS ns1.google.com.
google.com. 326567 IN NS ns2.google.com.
;; ADDITIONAL SECTION:
ns1.google.com. 152216 IN A 216.239.32.10
ns2.google.com. 152216 IN A 216.239.34.10
ns3.google.com. 152216 IN A 216.239.36.10
ns4.google.com. 152216 IN A 216.239.38.10
;; Query time: 92 msec
;; SERVER: 172.29.36.1#53(172.29.36.1)
;; WHEN: Thu Mar 5 14:38:45 2009
;; MSG SIZE rcvd: 212
7.Route manipulates the IP routing tables. Its primary use is to set up static routes to specific hosts or networks via an interface after it has been configured with the ifconfig program.When the add or del options are used, route modifies the routing tables. Without these options, route displays the current contents of the routing tables.
[fasil@smashtech ~]# route
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
54.192.56.321 * 255.255.255.0 U 0 0 0 eth0
* 255.255.0.0 U 0 0 0 eth0
default 0.0.0.0 UG 0 0 0 eth0
8.Traceroute : Internet is a large and complex aggregation of network hardware, connected together by gateways. Tracking the route one’s packets follow (or finding the miscreant gateway that’s discarding your packets) can be difficult.
Traceroute utilizes the IP protocol ‘time to live’ field and attempts to elicit an ICMP TIME_EXCEEDED response from each gateway along the path to some host. The only mandatory parameter is the destination host name or IP number. The default probe datagram length is 40 bytes, but this may be increased by specifying a packet length (in bytes) after the destination host name.
[fasil@smashtech ~]# traceroute google.com
traceroute: Warning: google.com has multiple addresses; using 209.85.171.100
traceroute to google.com (209.85.171.100), 30 hops max, 38 byte packets
1 * * *
9.W-displays information about the users currently on the machine, and their processes. The header shows, in this order, the current time, how long the system has been running, how many users are currently logged on, and the system load averages for the past 1, 5, and 15 minutes.
[fasil@smashtechl ~]# w
15:18:22 up 4:38, 3 users, load average: 0.89, 0.34, 0.19
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
root :0 - 10:41 ?xdm? 24:53 1.35s /usr/bin/gnome-session
root pts/1 :0.0 10:58 1.00s 0.34s 0.00s w
root pts/2 :0.0 12:10 23:32 0.03s 0.03s bash
10. Nmap is designed to allow system administrators and curious individuals to scan large networks to determine which hosts are up and what services they are offering. nmap supports a large number of scanning techniques such as:UDP, TCP connect(), TCP SYN (half open), ftp proxy (bounce attack), ICMP (ping sweep), FIN, ACK sweep, Xmas Tree,SYN sweep, IP Protocol, and Null scan. See the Scan Types section for more details. nmap also offers a number of advanced features such as remote OS detection via TCP/IP fingerprinting, stealth scanning, dynamic delay and retransmission calculations, parallel scanning, detection of down hosts via parallel pings, decoy scanning, port filtering detection, direct (non-portmapper) RPC scanning, fragmentation scanning, and flexible target and port specification.
Significant effort has been put into decent nmap performance for non-root users. Unfortunately, many critical kernel interfaces (such as raw sockets) require root privileges. nmap should be run as root whenever possible (not setuid root, of course).
The result of running nmap is usually a list of interesting ports on the machine(s) being scanned (if any). Nmap always gives the port’s "well known" service name (if any), number, state, and protocol. The state is either"open", "filtered", or "unfiltered". Open means that the target machine will accept() connections on that port.Filtered means that a firewall, filter, or other network obstacle is covering the port and preventing nmap from determining whether the port is open. Unfiltered means that the port is known by nmap to be closed and no fire-wall/filter seems to be interfering with nmap’s attempts to determine this. Unfiltered ports are the common case and are only shown when most of the scanned ports are in the filtered state.
Depending on options used, nmap may also report the following characteristics of the remote host: OS in use, TCP sequentiality, usernames running the programs which have bound to each port, the DNS name, whether the host is a smurf address, and a few other--Network exploration tool and security scanners.
[fasil@smashtech ~]# nmap 52.194.69.152
Starting nmap 3.70 ( http://www.insecure.org/nmap/ ) at 2009-03-05 15:21 IST
Interesting ports on 52.194.69.152
(The 1658 ports scanned but not shown below are in state: closed)
PORT STATE SERVICE
22/tcp open ssh
111/tcp open rpcbind
LINUX
File Handling Linux Commands
Linux has become most prominent operating system and for effective use of Linux system we should know certain basic file handling commands to perform our day-to-day operations in most efficient way. Here we have listed some of the most important and interesting File Handling commands which are ordered in categories wise to improve your Linux skills.
Easy File Viewing and Editing
We use gedit tool in Linux which is similar to notepad or WordPad in windows and it also got tabbed viewing of text files. But at the same time we should get familiar with using commands and this most will make that easier. Basic Text editors in Linux are Vim and Emacs which supports syntax highlighting and helps you a lot in programming skills. Some of the commands features are discussed here
Vim is easy to use and powerful text edit intended for beginner and advanced users. It has lot of in featured commands for text editing for simple task like copy, paste and some advanced commands like searching text, find and replace option.
| [fasil@smashtech ~]# vim smashtech.txt |
The above command will open the text file in the Vim editor and you can easily edit the text file and save it by entering the Escape key -> :w and to quit the editor Escape key -> :q .To know more about Vim commands download this cheat sheets.
Emacs is most powerful editor intended for advanced users. Prominent use of emacs is multiple window use. We can easily open almost four to five windows with horizontal or vertical view and helps you alot in manipulating multiple files.
| [fasil@smashtech ~]# emacs smashtech.txt |
The above command will open the text file in the Emacs editor and once editing is completed. Press ctrl+x+s to save file and to quit editor ctrl+x+c.To know more about emacs commands download this cheat sheet.
cat command will list the content of the file in the terminal .This option is limited to view files having only few lines since you have to scroll back to view the text if it is a large file.
| [fasil@smashtech ~]# cat smashtech.txt This text is displayed using cat command |
Simple command to view text files and to list the files in compressed archive like tar or zip.
| [fasil@smashtech ~]#less smashtech.tar.gz -rw-rw-r-- root/root 326 2009-03-04 13:48:50 /Documentation/RelNotes-1.5.3.1.txt -rw-rw-r-- root/root 1931 2009-03-04 13:48:50 Documentation/RelNotes-1.5.3.2.txt -rw-rw-r-- root/root 896 2009-03-04 13:48:50 /Documentation/RelNotes-1.5.3.3.txt -rw-rw-r-- root/root 1208 2009-03-04 13:48:50 /Documentation/RelNotes-1.5.3.4.txt -rw-rw-r-- root/root 3376 2009-03-04 13:48:50 |
Checking file size and disk usage
Simple commands like 'list' can be used to check the file size or folder size but the Linux has some more powerful commands to do so.
df - report filesystem disk space usage is simple command to check the disk space in all partitions of harddisk.
| [Fasil@smashtech ~]# df -h Filesystem Size Used Avail Use% Mounted on /dev/sda6 19.7G 18.1G 1.1G 89% / |
du - estimate file space usage of all files and folders
| [Fasil@smashtech ~]# du -sh . 602M . |
Simply Copy/rename and move files
Copying, moving and deleting files like never before, Simply saying you can delete files and folders very fast in command prompt then using mouse in GUI.But here is a caution although Linux is more powerful it does not have an undo command and if you delete a file/folder my mistake its loss. There are some methods to recover it but redundancy will be lost. cp - Copy files from source location to destination
| [Fasil@smashtech ~]# cp file1.txt file2.txt The above command will copy file1 as file2 text file [Fasil@smashtech ~]# cp -a smashtech fasil the above command will copy the folder smashtechtech as fasil |
mv-Move a file from original location to final location
| [Fasil@smashtech ~]# mv file1.txt file2.txt The above command will move/rename file1 as file2 text file [Fasil@smashtech ~]#mv -a smashtech fasil the above command will move contents of the folder smashtech to fasil |
rm-Remove a file or folder
| [Fasil@smashtech ~]# rm file1.txt The above command will delete file1 [Fasil@smashtech ~]#rm -rf smashtech the above command will delete the folder smashtech |
Compressing and Decompressing Files and Folders
The most interesting usage in Linux commands are compressing the text files in more efficient and effective way and some of the compressing and decompressing commands are shown here.
tar- This command is used for both compressing and extracting
| [Fasil@smashtech ~]# tar -cvf filename.tar folder/ The above command will create a tar archive with name.tar and folder is archived Fasil@smashtech ~]# tar -cvzf filename.tar.gz folder/ The above command will create a gzip archive with name.tar and folder is archived Fasil@smashtech ~]# tar -cvjf filename.tar.bz2 folder/ The above command will create a bzip2 archive with name.tar and folder is archived |
| [Fasil@smashtech ~]# tar -xvf filename.tar The above command will extract the content of the tar archive with name.tar Fasil@smashtech ~]# tar -cvzf filename.tar.gz folder/ The above command will extract the content of a gzip archive Fasil@smashtech ~]# tar -cvjf filename.tar.bz2 folder/ The above command will extract the content of the bzip2 archive |
Sharing CKTS
CircuitBee: Sharing Circuit Diagrams made easy
Are you an electronic hobbyist or having passion in using electronic
circuits for your projects and wanted to share your circuit diagram for
any help from open community. Then CircuitBee is the place you have to
land into. Many online utilities are there to share documents, images
and presentation, But sharing a circuit diagram with peers or online
community is not that easy and getting corrections for the circuits as
well. CircuitBee solves this problem. CircuitBee allows you to browse all public circuits and enables you to embed on any webpages. Highly useful for sharing in DIY sites and electronics hobby sites.
So What is Circuit Bee?
sample circuit embedded below
So What is Circuit Bee?
CircuitBee takes your schematic project files, converts them into its
own internal format and then provides you with an embeddable version of
the circuit, similar to Google Maps but for electronics schematics.
You can pan, zoom, go fullscreen, mouse over components to see what they are and schematic viewer that can be embedded on any web page as well as being visible on the CircuitBee website itself.
How can I upload my Circuit ?
Follow the instructions provided in CircuitBee page (http://www.circuitbee.com/
What file types can I upload?
Currently CircuitBee supports most schematic files saved from KiCad (no hierarchical schematics). You can also upload schmatics created in Eagle using ULP script available on Eagle import guide page.
You can pan, zoom, go fullscreen, mouse over components to see what they are and schematic viewer that can be embedded on any web page as well as being visible on the CircuitBee website itself.
How can I upload my Circuit ?
Follow the instructions provided in CircuitBee page (http://www.circuitbee.com/
What file types can I upload?
Currently CircuitBee supports most schematic files saved from KiCad (no hierarchical schematics). You can also upload schmatics created in Eagle using ULP script available on Eagle import guide page.
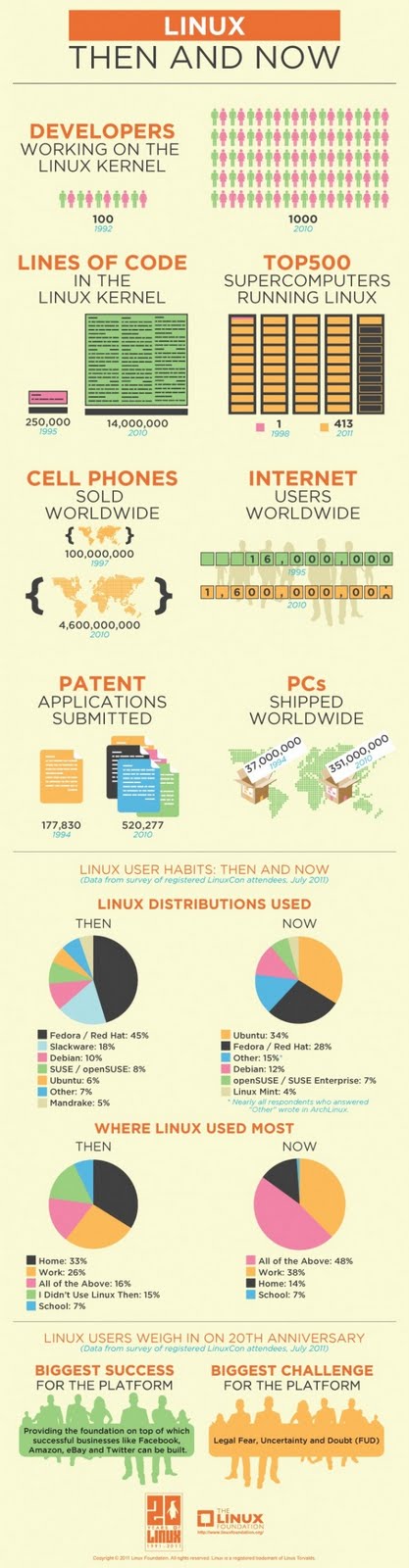
Celebrating Linux 20 years
20-years of Linux
Literacy Week
Financial Literacy for the Week

EPF
1. How to do EPF transfer online [ Link ]
Insurance
1. How to open E-Insurance Demat Account [ Link ]
2. How to claim Life Insurance [ Link ]
Banking
1. 6 dumb mistakes which you make while writing Cheque’s – Dont do it ! [ Link ]
Mutual Funds
1. Mutual Fund SIP Analyzer - Excel Sheet [ Link ]
Androis settings while travelling
Android Settings for Travellers
 This
is one of the important settings in Android to know your current
location using Cell Tower info there by avoiding the use of GPS and
A-GPS which kills the battery. This setting is much more useful for
persons travel ling in Train overnight and with the help of this setting
you can get the cell tower location information there by identifying the
current location.
This
is one of the important settings in Android to know your current
location using Cell Tower info there by avoiding the use of GPS and
A-GPS which kills the battery. This setting is much more useful for
persons travel ling in Train overnight and with the help of this setting
you can get the cell tower location information there by identifying the
current location.I have enjoyed this setting decade back in Nokia 1100 where it scrolls in the main screen and goes after some time where as in Android you will get this information as message.
Note: The result of this settings depends on your cellular operator. I have tested in Airtel network and its work fine most of the time which is very helpful during train travel.
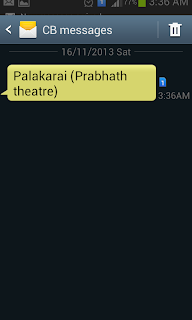
Settings to get Cell Tower information in Android.
1. Go to "Messages"
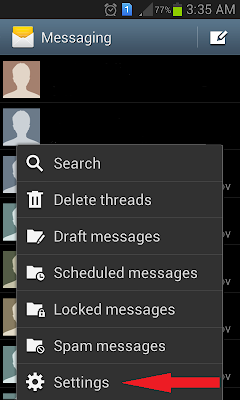
Step 2. Navigate and select " Cell Broadcast (CB) Settings"
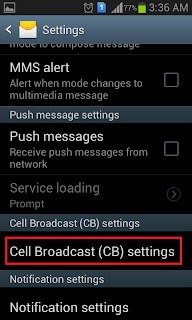
Step 3. Check on "CB Activation"
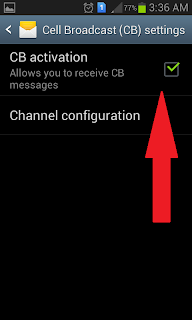
Step 4. You will get instant messages as you move from one Cell tower to another
Friends Tips to Improve your Typing Speed with Simple Techniques
To improve your typing speed to about 50wpm. Then follow
this simple techniques given below to improve your typing speed . Speed
Typing is necessary for a common human beings to interact with computers.
As every computer users now use mail service and other online services
.Speed typing improves your productivity and saves time.
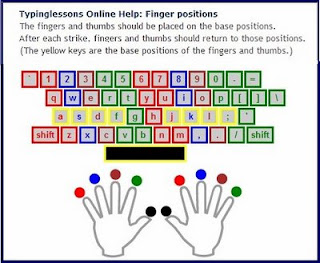
Learn from the Home Keys A,S,D,F for left hand and J,K,L, ; for right hand and use your right hand Thumb for Space Key as illustrated in the below diagram and note the corresponding fingers for the letter. This basic lesson of typing .
Familiarize with Home Keys by using any of the basic Typing Tutor software's which are available in plenty. A Google Search for a Typing Tutor software will do.No matter which software you use , but try to be proefficient with your Home Keys.Remember you can locate any key on the keyboard from the Home Key.
After Familiarizing with ASDF and JKL; proceed to use ER on the left hand and UI on the right hand as illustrated in the below figure. Note the color associated with the correspoding fingers
As mentioned below put some time exclusively to improve your typing speed.Say a solid 15 minutes per day on the morning and evening guarantees you to improve your typing speed significantly.
As your familiriaze with the keys ,have an eye on the accuracy and try to improve this on the side. Remember accuracy in typing is the integral part of Speed typing.
I hope this simple techiques can improve your typing speed significantly as it did for me.
Lesson One :
Learn from the Home Keys A,S,D,F for left hand and J,K,L, ; for right hand and use your right hand Thumb for Space Key as illustrated in the below diagram and note the corresponding fingers for the letter. This basic lesson of typing .
Lesson Two:
Familiarize with Home Keys by using any of the basic Typing Tutor software's which are available in plenty. A Google Search for a Typing Tutor software will do.No matter which software you use , but try to be proefficient with your Home Keys.Remember you can locate any key on the keyboard from the Home Key.
Lesson Three:
After Familiarizing with ASDF and JKL; proceed to use ER on the left hand and UI on the right hand as illustrated in the below figure. Note the color associated with the correspoding fingers

Lesson Four:
As mentioned below put some time exclusively to improve your typing speed.Say a solid 15 minutes per day on the morning and evening guarantees you to improve your typing speed significantly.
Lesson Five :
As your familiriaze with the keys ,have an eye on the accuracy and try to improve this on the side. Remember accuracy in typing is the integral part of Speed typing.
I hope this simple techiques can improve your typing speed significantly as it did for me.
Tools to manage multiple Twitter account
1. CoTweet
Cotweet is designed to manage your business activity via twitter. It helps companies to reach customers easily and promotes productivity. It supports to add multiple twitter accounts and helps in assigning tasks between accounts. It also has scheduling tweets, easy interface and tracking the bit.ly clicks using the API feature. Much clearly and neatly designed UI helps everyone to understand its functionality in one shot. Just sign up once free and you will feel the difference how twittering fun and productive too.
2.HootSuite
HootSuite is another excellent productivity to manage the business activity in Twitter. It has its own URL shortening system namely ow.ly and you can get a clear statics about the click made to your URL. The complete analysis of the clicks are given in excellent graphical form. Apart from that managing muliple Twitter accounts HootSuite helps to embedd columns, manage groups, schedule tweets and manage RSS feeds of your blog or site.
JAVA
VIVA Questions - For more mail to gistservicesz@gmail.com
Struts
1. What is Struts?
1.Struts is a web page development framework and an open source software that helps developers build web applications quickly and easily. Struts combines
Java Servlets, Java Server Pages, custom tags, and message resources into a unified framework. It is a cooperative, synergistic platform, suitable for
development teams, independent developers, and everyone between.
2.The core of the Struts framework is a flexible control layer based on standard technologies like Java Servlets, JavaBeans, ResourceBundles, and XML, as
well as various Jakarta Commons packages. Struts encourages application architectures based on the Model 2 approach, a variation of the classic
Model-View-Controller (MVC) design paradigm. Struts provides its own Controller component and integrates with other technologies to provide the Model and
the View. For the Model, Struts can interact with standard data access technologies, like JDBC and EJB, as well as most any third-party packages, like
Hibernate, iBATIS, or Object Relational Bridge. For the View, Struts works well with JavaServer Pages, including JSTL and JSF, as well as Velocity
Templates, XSLT, and other presentation systems. The Struts framework provides the invisible underpinnings every professional web application needs to
survive. Struts helps you create an extensible development environment for your application, based on published standards and proven design patterns.
3. Struts Frame work is the implementation of Model-View-Controller (MVC) design pattern for the JSP. Struts is maintained as a part of Apache Jakarta
project and is open source. Struts Framework is suited for the application of any size. Latest version of struts can be downloaded from
http://jakarta.apache.org/. We are using jakarta-struts-1.1 and jakarta-tomcat-5.0.4 for this tutorial.
2. How is the MVC design pattern used in Struts framework?
In the MVC design pattern, application flow is mediated by a central Controller. The Controller delegates requests to an appropriate handler. The
handlers are tied to a Model, and each handler acts as an adapter between the request and the Model. The Model represents, or encapsulates, an
application's business logic or state. Control is usually then forwarded back through the Controller to the appropriate View. The forwarding can be
determined by consulting a set of mappings, usually loaded from a database or configuration file. This provides a loose coupling between the View and
Model, which can make an application significantly easier to create and maintain.
Controller--Servlet controller which supplied by Struts itself; View --- what you can see on the screen, a JSP page and presentation components; Model
--- System state and a business logic JavaBeans.
3. Who makes the Struts?
Struts is hosted by the Apache Software Foundation(ASF) as part of its Jakarta project, like Tomcat, Ant and Velocity.
4. Why it called Struts?
Because the designers want to remind us of the invisible underpinnings that hold up our houses, buildings, bridges, and ourselves when we are on stilts.
This excellent description of Struts reflect the role the Struts plays in developing web applications.
5. Do we need to pay the Struts if being used in commercial purpose?
No. Struts is available for commercial use at no charge under the Apache Software License. You can also integrate the Struts components into your own
framework just as if they were written in house without any red tape, fees, or other hassles.
6. What are the core classes of Struts?
Action, ActionForm, ActionServlet, ActionMapping, ActionForward are basic classes of Struts.
7. What is the design role played by Struts?
The role played by Struts is controller in Model/View/Controller(MVC) style. The View is played by JSP and Model is played by JDBC or generic data source
classes. The Struts controller is a set of programmable components that allow developers to define exactly how the application interacts with the user.
8. What configuration files are used in Struts?
ApplicationResources.properties
struts-config.xml
These two files are used to bridge the gap between the Controller and the Model.
9. What helpers in the form of JSP pages are provided in Struts framework?
--struts-html.tld
--struts-bean.tld
--struts-logic.tld
10. Is Struts efficient?
11. How you will enable front-end validation based on the xml in validation.xml?
The < html:javascript > tag to allow front-end validation based on the xml in validation.xml. For example the code: < html:javascript formName=logonForm
dynamicJavascript=true staticJavascript=true / > generates the client side java script for the form logonForm as defined in the validation.xml file. The
< html:javascript > when added in the jsp file generates the client site validation script.
12. What is ActionServlet?
The class org.apache.struts.action.ActionServlet is the called the ActionServlet. In the the Jakarta Struts Framework this class plays the role of
controller. All the requests to the server goes through the controller. Controller is responsible for handling all the requests.
13. How you will make available any Message Resources Definitions file to the Struts Framework Environment?
Message Resources Definitions file are simple .properties files and these files contains the messages that can be used in the struts project. Message
Resources Definitions files can be added to the struts-config.xml file through < message-resources / > tag. Example: < message-resources parameter=
MessageResources / >
14. What is Action Class?
The Action Class is part of the Model and is a wrapper around the business logic. The purpose of Action Class is to translate the HttpServletRequest to
the business logic. To use the Action, we need to Subclass and overwrite the execute() method. In the Action Class all the database/business processing
are done. It is advisable to perform all the database related stuffs in the Action Class. The ActionServlet (commad) passes the parameterized class to
Action Form using the execute() method. The return type of the execute method is ActionForward which is used by the Struts Framework to forward the
request to the file as per the value of the returned ActionForward object.
15. How Struts control data flow?
Struts implements the MVC/Layers pattern through the use of ActionForwards and ActionMappings to keep control-flow decisions out of presentation layer.
16. Write code of any Action Class?
Here is the code of Action Class that returns the ActionForward object.
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.apache.struts.action.Action;
import org.apache.struts.action.ActionForm;
import org.apache.struts.action.ActionForward;
import org.apache.struts.action.ActionMapping;
public class TestAction extends Action
{
public ActionForward execute(
ActionMapping mapping,
ActionForm form,
HttpServletRequest request,
HttpServletResponse response) throws Exception
{
return mapping.findForward(\"testAction\");
}
}
17. What is ActionForm?
An ActionForm is a JavaBean that extends org.apache.struts.action.ActionForm. ActionForm maintains the session state for web application and the
ActionForm object is automatically populated on the server side with data entered from a form on the client side.
18. What is Struts Validator Framework?
Struts Framework provides the functionality to validate the form data. It can be use to validate the data on the users browser as well as on the server
side. Struts Framework emits the java scripts and it can be used validate the form data on the client browser. Server side validation of form can be
accomplished by sub classing your From Bean with DynaValidatorForm class. The Validator framework was developed by David Winterfeldt as third-party
add-on to Struts. Now the Validator framework is a part of Jakarta Commons project and it can be used with or without Struts. The Validator framework
comes integrated with the Struts Framework and can be used without doing any extra settings.
19. Give the Details of XML files used in Validator Framework?
The Validator Framework uses two XML configuration files validator-rules.xml and validation.xml. The validator-rules.xml defines the standard validation
routines, these are reusable and used in validation.xml. to define the form specific validations. The validation.xml defines the validations applied to a
form bean.
20. How you will display validation fail errors on jsp page?
The following tag displays all the errors:
< html:errors/ >
21. Can I use other beans or hashmaps with ActionForms?
Yes. There are several ways that you can use other beans or hashmaps with ActionForms.
you. There is nothing preventing you from using other beans, or including them in your form beans. Here are some examples:
Collections as properties Suppose that you need to display a pulldown list of available colors on an input form in your application. You can include a
string-valued colorSelected property in your ActionForm to represent the user's selection and a colorOptions property implemented as a Collection (of
strings) to store the available color choices. Assuming that you have defined the getters and setters for the colorSelected and colorOptions properties
in your orderEntryForm form bean, you can render the pulldown list using:
<html:select property="colorSelected">
<html:options property="colorOptions" name="orderEntryForm"/>
</html:select>
The list will be populated using the strings in the colorOptions collection of the orderEntryForm and the value that the user selects will go into the
colorSelected property that gets posted to the subsequent Action. Note that we are assuming here that the colorOptions property of the orderEntryForm has
already been set.
See How can I prepopulate a form? for instructions on how to set form bean properties before rendering edit forms that expect properties to be pre-set.
Independent DTO An Action that retrieves a list of open orders (as an ArrayList of Order objects) can use a DTO independently of any form bean to
transfer search results to the view. First, the Action's execute method performs the search and puts the DTO into the request:
ArrayList results = businessObject.executeSearch(searchParameters);
request.setAttribute("searchResults",results);
Then the view can iterate through the results using the "searchResults" request key to reference the DTO:
<logic:iterate id="order" name="searchResults" type="com.foo.bar.Order">
<tr><td><bean:write name="order" property="orderNumber"/><td>
<td>..other properties...</td></tr>
</logic:iterate>
22. Why do the Struts tags provide for so little formatting?
The Struts tags seem to provide only the most rudimentary functionality. Why is there not better support for date formatting and advanced string
handling?
Three reasons:
First, work started on the JSTL and we didn't want to duplicate the effort.
Second, work started on Java Server Faces, and we didn't want to duplicate that effort either.
Third, in a Model 2 application, most of the formatting can be handled in the ActionForms (or in the business tier), so all the tag has to do is spit out
a string. This leads to better reuse since the same "how to format" code does not need to be repeated in every instance. You can "say it once" in a
JavaBean and be done with it. Why don't the Struts taglibs offer more layout options?
Since the Struts tags are open source, you can extend them to provide whatever additional formatting you may need. If you are interested in a pre-written
taglib that offers more layout options, see the struts-layout taglib.
In the same arena, there is a well regarded contributor taglib that can help you create Menus for your Struts applications.
23. Why does the <html:link> tag URL-encode javascript and mailto links?
The <html:link> tag is not intended for use with client-side references like those used to launch Javascripts or email clients. The purpose of link tag
is to interject the context (or module) path into the URI so that your server-side links are not dependent on your context (or module) name. It also
encodes the link, as needed, to maintain the client's session on the server. Neither feature applies to client-side links, so there is no reason to use
the <html:link> tag. Simply markup the client-side links using the standard tag.
24. Why does the <html:link> tag URL-encode javascript and mailto links?
The <html:link> tag is not intended for use with client-side references like those used to launch Javascripts or email clients. The purpose of link tag
is to interject the context (or module) path into the URI so that your server-side links are not dependent on your context (or module) name. It also
encodes the link, as needed, to maintain the client's session on the server. Neither feature applies to client-side links, so there is no reason to use
the <html:link> tag. Simply markup the client-side links using the standard tag.
25. How can I scroll through list of pages like the search results in google?
Many Struts developers use the Pager from the JSPTags site.
26. How would you display “validation fail” errors on a JSP page?
Following tag displays all the errors: <html:errors/>
27. How can one enable front-end validation based on the xml in validation.xml?
The <html:javascript> tag allows front-end validation based on the xml in validation.xml.
For example the code:
generates the client side JavaScript for the form "logonForm" as defined in the validation.xml file.
The <html:javascript> when added in the JSP file generates the client side validation script.
Python
1. What is Python?
Python is an interpreted, interactive, object-oriented programming language. It incorporates
modules, exceptions, dynamic typing, very high level dynamic data types, and classes. Python
combines remarkable power with very clear syntax. It has interfaces to many system calls and
libraries, as well as to various window systems, and is extensible in C or C++. It is also
usable as an extension language for applications that need a programmable interface. Finally,
Python is portable: it runs on many Unix variants, on the Mac, and on PCs under MS-DOS, Windows,
Windows NT, and OS/2.
2. Is there a tool to help find bugs or perform static analysis?
Yes.
PyChecker is a static analysis tool that finds bugs in Python source code and warns about code
complexity and style. Pylint is another tool that checks if a module satisfies a coding standard,
and also makes it possible to write plug-ins to add a custom feature.
3. What is a negative index?
Python sequences are indexed with positive numbers and negative numbers. For positive numbers 0 is
the first index 1 is the second index and so forth. For negative indices -1 is the last index and -2
is the penultimate (next to last) index and so forth. Think of seq[-n] as the same as seq[len(seq)-n].
Using negative indices can be very convenient. For example S[:-1] is all of the string except for its
last character, which is useful for removing the trailing newline from a string.
4. What are the rules for local and global variables in Python?
In Python, variables that are only referenced inside a function are implicitly global. If a variable
is assigned a new value anywhere within the function's body, it's assumed to be a local. If a variable
is ever assigned a new value inside the function, the variable is implicitly local, and you need to
explicitly declare it as 'global'.
Though a bit surprising at first, a moment's consideration explains this. On one hand, requiring global
for assigned variables provides a bar against unintended side-effects. On the other hand, if global was
required for all global references, you'd be using global all the time. You'd have to declare as global
every reference to a builtin function or to a component of an imported module. This clutter would defeat
the usefulness of the global declaration for identifying side-effects.
5. How do I copy an object in Python?
In general, try copy.copy() or copy.deepcopy() for the general case. Not all objects can be copied, but most can.
Some objects can be copied more easily. Dictionaries have a copy() method:
newdict = olddict.copy()
Sequences can be copied by slicing:
new_l = l[:]
6. How can I find the methods or attributes of an object?
For an instance x of a user-defined class, dir(x) returns an alphabetized list of the names containing
the instance attributes and methods and attributes defined by its class.
7. How do I convert a string to a number?
For integers, use the built-in int() type constructor, e.g. int('144') == 144. Similarly, float() converts
to floating-point, e.g. float('144') == 144.0.
By default, these interpret the number as decimal, so that int('0144') == 144 and int('0x144') raises
ValueError. int(string, base) takes the base to convert from as a second optional argument,
so int('0x144', 16) == 324. If the base is specified as 0, the number is interpreted using Python's
rules: a leading '0' indicates octal, and '0x' indicates a hex number.
Do not use the built-in function eval() if all you need is to convert strings to numbers. eval() will be
significantly slower and it presents a security risk: someone could pass you a Python expression that
might have unwanted side effects. For example, someone could pass __import__('os').system("rm -rf $HOME")
which would erase your home directory.
eval() also has the effect of interpreting numbers as Python expressions, so that e.g. eval('09') gives
a syntax error because Python regards numbers starting with '0' as octal (base 8).
8. How do I convert a number to a string?
To convert, e.g., the number 144 to the string '144', use the built-in function str(). If you want a
hexadecimal or octal representation, use the built-in functions hex() or oct(). For fancy formatting,
use the % operator on strings, e.g. "%04d" % 144 yields '0144' and "%.3f" % (1/3.0) yields '0.333'.
See the library reference manual for details.
9. How do you remove duplicates from a list?
If you don't mind reordering the list, sort it and then scan from the end of the list, deleting duplicates as you go:
if List:
List.sort()
last = List[-1]
for i in range(len(List)-2, -1, -1):
if last==List[i]: del List[i]
else: last=List[i]
If all elements of the list may be used as dictionary keys (i.e. they are all hashable) this is often faster
d = {}
for x in List: d[x]=x
List = d.values()
10. How do you make an array in Python?
Use a list:
["this", 1, "is", "an", "array"]
Lists are equivalent to C or Pascal arrays in their time complexity; the primary difference is
that a Python list can contain objects of many different types.
The array module also provides methods for creating arrays of fixed types with compact representations,
but they are slower to index than lists. Also note that the Numeric extensions and others define
array-like structures with various characteristics as well.
To get Lisp-style linked lists, you can emulate cons cells using tuples:
lisp_list = ("like", ("this", ("example", None) ) )
If mutability is desired, you could use lists instead of tuples. Here the analogue of lisp car is
lisp_list[0] and the analogue of cdr is lisp_list[1]. Only do this if you're sure you really need to,
because it's usually a lot slower than using Python lists.
JSP
1. What is a JSP and what is it used for?
Java Server Pages (JSP) is a platform independent presentation layer technology that comes with SUN s J2EE platform.
JSPs are normal HTML pages with Java code pieces embedded in them. JSP pages are saved to *.jsp files. A JSP compiler
is used in the background to generate a Servlet from the JSP page.
2. What is difference between custom JSP tags and beans?
Custom JSP tag is a tag you defined. You define how a tag, its attributes and its body are interpreted, and then group your
tags into collections called tag libraries that can be used in any number of JSP files. To use custom JSP tags, you need to
define three separate components:
1. the tag handler class that defines the tag\'s behavior
2. the tag library descriptor file that maps the XML element names to the tag implementations
3. the JSP file that uses the tag library
When the first two components are done, you can use the tag by using taglib directive:
<%@ taglib uri="xxx.tld" prefix="..." %>
Then you are ready to use the tags you defined. Let's say the tag prefix is test:
MyJSPTag or
JavaBeans are Java utility classes you defined. Beans have a standard format for Java classes. You use tags
to declare a bean and use
to set value of the bean class and use
to get value of the bean class.
<%=identifier.getclassField() %>
Custom tags and beans accomplish the same goals -- encapsulating complex behavior into simple and accessible forms.
There are several differences:
Custom tags can manipulate JSP content; beans cannot.
Complex operations can be reduced to a significantly simpler form with custom tags than with beans. Custom tags require
quite a bit more work to set up than do beans.
Custom tags usually define relatively self-contained behavior, whereas beans are often defined in one servlet and used in
a different servlet or JSP page.
Custom tags are available only in JSP 1.1 and later, but beans can be used in all JSP 1.x versions.
3. What are the two kinds of comments in JSP and what's the difference between them.
<%-- JSP Comment --%>
4. What is JSP technology?
Java Server Page is a standard Java extension that is defined on top of the servlet Extensions. The goal of JSP is the simplified
creation and management of dynamic Web pages. JSPs are secure, platform-independent, and best of all, make use of Java as a
server-side scripting language.
5. What is JSP page?
A JSP page is a text-based document that contains two types of text: static template data, which can be expressed in any text-based
format such as HTML, SVG, WML, and XML, and JSP elements, which construct dynamic content.
6. What are the implicit objects?
Implicit objects are objects that are created by the web container and contain information related to a particular request, page,
or application. They are:
--request
--response
--pageContext
--session
--application
--out
--config
--page
--exceptio
7. How many JSP scripting elements and what are they?
There are three scripting language elements:
--declarations
--scriptlets
--expressions
8. Why are JSP pages the preferred API for creating a web-based client program?
Because no plug-ins or security policy files are needed on the client systems(applet does). Also, JSP pages enable cleaner
and more module application design because they provide a way to separate applications programming from web page design.
This means personnel involved in web page design do not need to understand Java programming language syntax to do their jobs.
9. Is JSP technology extensible?
YES. JSP technology is extensible through the development of custom actions, or tags, which are encapsulated in tag libraries.
10. Can we use the constructor, instead of init(), to initialize servlet?
Yes , of course you can use the constructor instead of init(). There’s nothing to stop you. But you shouldn’t. The original
reason for init() was that ancient versions of Java couldn’t dynamically invoke constructors with arguments, so there was no
way to give the constructur a ServletConfig. That no longer applies, but servlet containers still will only call your no-arg
constructor. So you won’t have access to a ServletConfig or ServletContext.
11. How can a servlet refresh automatically if some new data has entered the database?
You can use a client-side Refresh or Server Push.
12. The code in a finally clause will never fail to execute, right?
Using System.exit(1); in try block will not allow finally code to execute.
13. How many messaging models do JMS provide for and what are they?
JMS provide for two messaging models, publish-and-subscribe and point-to-point queuing.
14. What information is needed to create a TCP Socket?
The Local Systems IP Address and Port Number. And the Remote System’s IPAddress and Port Number.
15. What Class.forName will do while loading drivers?
It is used to create an instance of a driver and register it with the DriverManager. When you have loaded a driver,
it is available for making a connection with a DBMS.
XML
1. What is XML?
XML is the Extensible Markup Language. It improves the functionality of the Web by letting you identify your information
in a more accurate, flexible, and adaptable way.
It is extensible because it is not a fixed format like HTML (which is a single, predefined markup language). Instead, XML
is actually a metalanguage—a language for describing other languages—which lets you design your own markup languages for
limitless different types of documents. XML can do this because it's written in SGML, the international standard metalanguage
for text document markup (ISO 8879).
2. What is a markup language?
A markup language is a set of words and symbols for describing the identity of pieces of a document (for example ‘this is a
paragraph’, ‘this is a heading’, ‘this is a list’, ‘this is the caption of this figure’, etc). Programs can use this with a
stylesheet to create output for screen, print, audio, video, Braille, etc.
Some markup languages (eg those used in wordprocessors) only describe appearances (‘this is italics’, ‘this is bold’), but
this method can only be used for display, and is not normally re-usable for anything else.
3. Where should I use XML?
Its goal is to enable generic SGML to be served, received, and processed on the Web in the way that is now possible with HTML.
XML has been designed for ease of implementation and for interoperability with both SGML and HTML.
Despite early attempts, browsers never allowed other SGML, only HTML (although there were plugins), and they allowed it (even
encouraged it) to be corrupted or broken, which held development back for over a decade by making it impossible to program for
it reliably. XML fixes that by making it compulsory to stick to the rules, and by making the rules much simpler than SGML.
But XML is not just for Web pages: in fact it's very rarely used for Web pages on its own because browsers still don't provide
reliable support for formatting and transforming it. Common uses for XML include:
Information identification
because you can define your own markup, you can define meaningful names for all your information items. Information storage
because XML is portable and non-proprietary, it can be used to store textual information across any platform. Because it is backed
by an international standard, it will remain accessible and processable as a data format. Information structure
XML can therefore be used to store and identify any kind of (hierarchical) information structure, especially for long, deep, or
complex document sets or data sources, making it ideal for an information-management back-end to serving the Web. This is its most
common Web application, with a transformation system to serve it as HTML until such time as browsers are able to handle XML consistently.
Publishing
The original goal of XML as defined in the quotation at the start of this section. Combining the three previous topics (identity,
storage, structure) means it is possible to get all the benefits of robust document management and control (with XML) and publish
to the Web (as HTML) as well as to paper (as PDF) and to other formats (eg Braille, Audio, etc) from a single source document by
using the appropriate stylesheets. Messaging and data transfer
XML is also very heavily used for enclosing or encapsulating information in order to pass it between different computing systems
which would otherwise be unable to communicate. By providing a lingua franca for data identity and structure, it provides a common
envelope for inter-process communication (messaging). Web services
Building on all of these, as well as its use in browsers, machine-processable data can be exchanged between consenting systems,
where before it was only comprehensible by humans (HTML). Weather services, e-commerce sites, blog newsfeeds, AJaX sites, and
thousands of other data-exchange services use XML for data management and transmission, and the web browser for display and
interaction.
4. Why is XML such an important development?
It removes two constraints which were holding back Web developments:
1. dependence on a single, inflexible document type (HTML) which was being much abused for tasks it was never designed for;
2. the complexity of full SGML, whose syntax allows many powerful but hard-to-program options.
XML allows the flexible development of user-defined document types. It provides a robust, non-proprietary, persistent, and verifiable
file format for the storage and transmission of text and data both on and off the Web; and it removes the more complex options of SGML,
making it easier to program for.
5. Describe the role that XSL can play when dynamically generating HTML pages from a relational database.
Even if candidates have never participated in a project involving this type of architecture, they should recognize it as one of the
common uses of XML. Querying a database and then formatting the result set so that it can be validated as an XML document allows
developers to translate the data into an HTML table using XSLT rules. Consequently, the format of the resulting HTML table can be
modified without changing the database query or application code since the document rendering logic is isolated to the XSLT rules.
6. Aren't XML, SGML, and HTML all the same thing?
Not quite; SGML is the mother tongue, and has been used for describing thousands of different document types in many fields of
human activity, from transcriptions of ancient Irish manuscripts to the technical documentation for stealth bombers, and from
patients' clinical records to musical notation. SGML is very large and complex, however, and probably overkill for most common
office desktop applications.
XML is an abbreviated version of SGML, to make it easier to use over the Web, easier for you to define your own document types,
and easier for programmers to write programs to handle them. It omits all the complex and less-used options of SGML in return for
the benefits of being easier to write applications for, easier to understand, and more suited to delivery and interoperability over
the Web. But it is still SGML, and XML files may still be processed in the same way as any other SGML file (see the question on XML
software).
7. Who is responsible for XML?
XML is a project of the World Wide Web Consortium (W3C), and the development of the specification is supervised by an XML Working Group.
A Special Interest Group of co-opted contributors and experts from various fields contributed comments and reviews by email.
XML is a public format: it is not a proprietary development of any company, although the membership of the WG and the SIG represented
companies as well as research and academic institutions. The v1.0 specification was accepted by the W3C as a Recommendation on Feb 10,
1998.
HTML is just one of many SGML or XML applications—the one most frequently used on the Web.
Technical readers may find it more useful to think of XML as being SGML-- rather than HTML++.
8. Why is XML such an important development?
It removes two constraints which were holding back Web developments:
1. dependence on a single, inflexible document type (HTML) which was being much abused for tasks it was never designed for;
2. the complexity of full question A.4, SGML, whose syntax allows many powerful but hard-to-program options.
XML allows the flexible development of user-defined document types. It provides a robust, non-proprietary, persistent, and verifiable
file format for the storage and transmission of text and data both on and off the Web; and it removes the more complex options of SGML,
making it easier to program for.
9. Give a few examples of types of applications that can benefit from using XML.
There are literally thousands of applications that can benefit from XML technologies. The point of this question is not to have the
candidate rattle off a laundry list of projects that they have worked on, but, rather, to allow the candidate to explain the rationale
for choosing XML by citing a few real world examples. For instance, one appropriate answer is that XML allows content management systems
to store documents independently of their format, which thereby reduces data redundancy. Another answer relates to B2B exchanges or supply
chain management systems. In these instances, XML provides a mechanism for multiple companies to exchange data according to an agreed upon
set of rules. A third common response involves wireless applications that require WML to render data on hand held devices.
10. Give a few examples of types of applications that can benefit from using XML.
There are literally thousands of applications that can benefit from XML technologies. The point of this question is not to have the
candidate rattle off a laundry list of projects that they have worked on, but, rather, to allow the candidate to explain the rationale
for choosing XML by citing a few real world examples. For instance, one appropriate answer is that XML allows content management systems
to store documents independently of their format, which thereby reduces data redundancy. Another answer relates to B2B exchanges or supply
chain management systems. In these instances, XML provides a mechanism for multiple companies to exchange data according to an agreed upon
set of rules. A third common response involves wireless applications that require WML to render data on hand held devices.
11. What is DOM and how does it relate to XML?
The Document Object Model (DOM) is an interface specification maintained by the W3C DOM Workgroup that defines an application independent
mechanism to access, parse, or update XML data. In simple terms it is a hierarchical model that allows developers to manipulate XML documents
easily Any developer that has worked extensively with XML should be able to discuss the concept and use of DOM objects freely. Additionally,
it is not unreasonable to expect advanced candidates to thoroughly understand its internal workings and be able to explain how DOM differs
from an event-based interface like SAX.
12. What is SOAP and how does it relate to XML?
The Simple Object Access Protocol (SOAP) uses XML to define a protocol for the exchange of information in distributed computing environments.
SOAP consists of three components: an envelope, a set of encoding rules, and a convention for representing remote procedure calls. Unless
experience with SOAP is a direct requirement for the open position, knowing the specifics of the protocol, or how it can be used in conjunction
with HTTP, is not as important as identifying it as a natural application of XML.
13. Why not just carry on extending HTML?
HTML was already overburdened with dozens of interesting but incompatible inventions from different manufacturers, because it provides only
one way of describing your information.
XML allows groups of people or organizations to question C.13, create their own customized markup applications for exchanging information
in their domain (music, chemistry, electronics, hill-walking, finance, surfing, petroleum geology, linguistics, cooking, knitting, stellar
cartography, history, engineering, rabbit-keeping, question C.19, mathematics, genealogy, etc).
HTML is now well beyond the limit of its usefulness as a way of describing information, and while it will continue to play an important role
for the content it currently represents, many new applications require a more robust and flexible infrastructure.
14. Why should I use XML?
Here are a few reasons for using XML (in no particular order). Not all of these will apply to your own requirements, and you may have
additional reasons not mentioned here (if so, please let the editor of the FAQ know!).
absolutely nothing whatever to do with formatting, appearance, or the actual text content of your documents, only the structure of them.
everyone uses the same syntax it makes writing these systems much faster and more reliable.
with it, for lots of good reasons, but you don't pay for XML itself).
time to apply the required formatting to the text or data identified by its structure (location, position, rank, order, or whatever).
15. Can you walk us through the steps necessary to parse XML documents?
Superficially, this is a fairly basic question. However, the point is not to determine whether candidates understand the concept of a parser
but rather have them walk through the process of parsing XML documents step-by-step. Determining whether a non-validating or validating parser
is needed, choosing the appropriate parser, and handling errors are all important aspects to this process that should be included in the
candidate's response.
J2EE
What is J2EE?
J2EE is an environment for developing and deploying enterprise applications. The J2EE platform consists of a set of services, application programming
interfaces (APIs), and protocols that provide the functionality for developing multitiered, web-based applications.
What is the J2EE module?
A J2EE module consists of one or more J2EE components for the same container type and one component deployment descriptor of that type.
What are the components of J2EE application?
A J2EE component is a self-contained functional software unit that is assembled into a J2EE application with its related classes and files and
communicates with other components. The J2EE specification defines the following J2EE components:
What are the four types of J2EE modules?
1. Application client module
2. Web module
3. Enterprise JavaBeans module
4. Resource adapter module
What does application client module contain?
The application client module contains:
--class files,
--an application client deployment descriptor.
Application client modules are packaged as JAR files with a .jar extension.
What are the differences between Ear, Jar and War files? Under what circumstances should we use each one?
There are no structural differences between the files; they are all archived using zip-jar compression. However, they are intended for different
purposes.
--Jar files (files with a .jar extension) are intended to hold generic libraries of Java classes, resources, auxiliary files, etc.
--War files (files with a .war extension) are intended to contain complete Web applications. In this context, a Web application is defined as a single
group of files, classes, resources, .jar files that can be packaged and accessed as one servlet context.
--Ear files (files with a .ear extension) are intended to contain complete enterprise applications. In this context, an enterprise application is
defined as a collection of .jar files, resources, classes, and multiple Web applications.
Each type of file (.jar, .war, .ear) is processed uniquely by application servers, servlet containers, EJB containers, etc.
What is the difference between Session bean and Entity bean?one?
The Session bean and Entity bean are two main parts of EJB container.
Session Bean
--represents a workflow on behalf of a client
--one-to-one logical mapping to a client.
--created and destroyed by a client
--not permanent objects
--lives its EJB container(generally) does not survive system shut down
--two types: stateless and stateful beans
Entity Bean
--represents persistent data and behavior of this data
--can be shared among multiple clients
--persists across multiple invocations
--findable permanent objects
--outlives its EJB container, survives system shutdown
--two types: container managed persistence(CMP) and bean managed persistence(BMP)
What is "applet"
A J2EE component that typically executes in a Web browser but can execute in a variety of other applications or devices that support the applet
programming model.
What is "applet container"
A container that includes support for the applet programming model.
What is "application assembler"
A person who combines J2EE components and modules into deployable application units.
What is "application client"
A first-tier J2EE client component that executes in its own Java virtual machine. Application clients have access to some J2EE platform APIs.
What is "application client container"
A container that supports application client components.
What is "application client module"
A software unit that consists of one or more classes and an application client deployment descriptor.
What is "application component provider"
A vendor that provides the Java classes that implement components' methods, JSP page definitions, and any required deployment descriptors.
What is "application configuration resource file"
An XML file used to configure resources for a JavaServer Faces application, to define navigation rules for the application, and to register converters,
validators, listeners, renderers, and components with the application.
What is "archiving"
The process of saving the state of an object and restoring it.
What is "asant"
A Java-based build tool that can be extended using Java classes. The configuration files are XML-based, calling out a target tree where various tasks
get executed.
What is "attribute"What is "asant"
A qualifier on an XML tag that provides additional information.
What is authentication ?
The process that verifies the identity of a user, device, or other entity in a computer system, usually as a prerequisite to allowing access to
resources in a system. The Java servlet specification requires three types of authentication-basic, form-based, and mutual-and supports digest
authentication.
What is authorization?
The process by which access to a method or resource is determined. Authorization depends on the determination of whether the principal associated with
a request through authentication is in a given security role. A security role is a logical grouping of users defined by the person who assembles the
application. A deployer maps security roles to security identities. Security identities may be principals or groups in the operational environment.
What is authorization constraint?
An authorization rule that determines who is permitted to access a Web resource collection.
What is B2B?
B2B stands for Business-to-business.
What is backing bean?
A JavaBeans component that corresponds to a JSP page that includes JavaServer Faces components. The backing bean defines properties for the components
on the page and methods that perform processing for the component. This processing includes event handling, validation, and processing associated with
navigation.
What is basic authentication?
An authentication mechanism in which a Web server authenticates an entity via a user name and password obtained using the Web application's built-in
authentication mechanism.
What is bean-managed persistence?
The mechanism whereby data transfer between an entity bean's variables and a resource manager is managed by the entity bean.
What is bean-managed transaction?
A transaction whose boundaries are defined by an enterprise bean.
What is binding (XML)?
Generating the code needed to process a well-defined portion of XML data.
What is binding (JavaServer Faces technology)?
Wiring UI components to back-end data sources such as backing bean properties.
What is build file?
The XML file that contains one or more asant targets. A target is a set of tasks you want to be executed. When starting asant, you can select which
targets you want to have executed. When no target is given, the project's default target is executed.
What is business logic?
The code that implements the functionality of an application. In the Enterprise JavaBeans architecture, this logic is implemented by the methods of an
enterprise bean.
What is business method?
A method of an enterprise bean that implements the business logic or rules of an application.
What is callback methods?
Component methods called by the container to notify the component of important events in its life cycle.
What is caller?
Same as caller principal.
What is caller principal?
The principal that identifies the invoker of the enterprise bean method.
What is cascade delete?
A deletion that triggers another deletion. A cascade delete can be specified for an entity bean that has container-managed persistence.
What is CDATA?
A predefined XML tag for character data that means "don't interpret these characters," as opposed to parsed character data (PCDATA), in which the
normal rules of XML syntax apply. CDATA sections are typically used to show examples of XML syntax.
What is certificate authority?
A trusted organization that issues public key certificates and provides identification to the bearer.
What is client-certificate authentication?
An authentication mechanism that uses HTTP over SSL, in which the server and, optionally, the client authenticate each other with a public key
certificate that conforms to a standard that is defined by X.509 Public Key Infrastructure.
What is comment?
In an XML document, text that is ignored unless the parser is specifically told to recognize it.
What is commit?
The point in a transaction when all updates to any resources involved in the transaction are made permanent.
What is component contract?
The contract between a J2EE component and its container. The contract includes life-cycle management of the component, a context interface that the
instance uses to obtain various information and services from its container, and a list of services that every container must provide for its
components.
What is component-managed sign-on?
A mechanism whereby security information needed for signing on to a resource is provided by an application component.
What is connector?
A standard extension mechanism for containers that provides connectivity to enterprise information systems. A connector is specific to an enterprise
information system and consists of a resource adapter and application development tools for enterprise information system connectivity. The resource
adapter is plugged in to a container through its support for system-level contracts defined in the Connector architecture.
What is Connector architecture?
An architecture for integration of J2EE products with enterprise information systems. There are two parts to this architecture: a resource adapter
provided by an enterprise information system vendor and the J2EE product that allows this resource adapter to plug in. This architecture defines a set
of contracts that a resource adapter must support to plug in to a J2EE product-for example, transactions, security, and resource management.
What is container?
An entity that provides life-cycle management, security, deployment, and runtime services to J2EE components. Each type of container (EJB, Web, JSP,
servlet, applet, and application client) also provides component-specific services.
What is container-managed persistence?
The mechanism whereby data transfer between an entity bean's variables and a resource manager is managed by the entity bean's container. .
What is container-managed sign-on?
The mechanism whereby security information needed for signing on to a resource is supplied by the container.
What is container-managed transaction?
A transaction whose boundaries are defined by an EJB container. An entity bean must use container-managed transactions.
What is content?
In an XML document, the part that occurs after the prolog, including the root element and everything it contains.
JAVA
Q Why a thread blocks or enters to waiting state on I/O?
A Threads enters to waiting state or block on I/O because other threads can execute while the I/O operations are performed.
Q What are transient variables in java?
A Transient variables are variable that cannot be serialized.
Q How Observer and Observable are used?
A Subclass of Observable class maintains a list of observers. Whenever an Observable object is updated, it invokes the update () method of each of its observers to notify the observers that it has a changed state. An observer is any object that implements the interface Observer.
Q What is synchronization? A Synchronization is the ability to control the access of multiple threads to shared resources. Synchronization stops multithreading. With synchronization, at a time only one thread will be able to access a shared resource.
Q what is List interface?
A List is an ordered collection of objects.
Q What is a Vector?
A Vector is a grow able array of objects.
Q What is the difference between yield () and sleep ()?
A When a object invokes yield () it returns to ready state. But when an object invokes sleep () method enters to not ready state.
Q What are Wrapper Classes?
A They are wrappers to primitive data types. They allow us to access primitives as objects.
Q Can we call finalize () method?
A Yes. Nobody will stop us to call any method, if it is accessible in our class. But a garbage collector cannot call an object's finalize method if that object is reachable.
Q What is the difference between time slicing and preemptive scheduling?
A In preemptive scheduling, highest priority task continues execution till it enters a not running state or a higher priority task comes into existence. In time slicing, the task continues its execution for a predefined period of time and reenters the pool of ready tasks.
Q What is the initial state of a thread when it is created and started?
A The thread is in ready state.
Q Can we declare an anonymous class as both extending a class and implementing an interface?
A No. An anonymous class can extend a class or implement an interface, but it cannot be declared to do both
Q What are the differences between Boolean & operator and & operator?
A When an expression containing the & operator is evaluated, both operands are evaluated. And the & operator is applied to the operand. When an expression containing && operator is evaluated, the first operand is evaluated. If the first operand returns a value of true then only the second operand is evaluated otherwise the second part will not get executed. && is also called short cut and.
Q What is the use of the finally block?
A Finally is the block of code that executes always. The code in finally block will execute even if an exception is occurred. Finally will not execute when the user calls System.exit().
Q What is an abstract method?
A An abstract method is a method that don't have a body. It is declared with modifier abstract.
JAVA and EJB
Oracle
What is use of a cursor variable? How it is defined.
A cursor variable is associated with different statements at run time, which can hold different values at run time. Static cursors can only be associated with one run time query. A cursor variable is reference type(like a pointer in C). Declaring a cursor variable: TYPE type_name IS REF CURSOR RETURN return_type type_name is the name of the reference type,return_type is a record type indicating the types of the select list that will eventually be returned by the cursor variable.
What should be the return type for a cursor variable.Can we use a scalar data type as return type?
The return type for a cursor must be a record type.It can be declared explicitly as a user-defined or %ROWTYPE can be used. eg TYPE t_studentsref IS REF CURSOR RETURN students%ROWTYPE
How you open and close a cursor variable.Why it is required?
OPEN cursor variable FOR SELECT…Statement CLOSE cursor variable In order to associate a cursor variable with a particular SELECT statement OPEN syntax is used.In order to free the resources used for the query CLOSE statement is used.
How you were passing cursor variables in PL/SQL 2.2?
In PL/SQL 2.2 cursor variables cannot be declared in a package.This is because the storage for a cursor variable has to be allocated using Pro*C or OCI with version 2.2,the only means of passing a cursor variable to a PL/SQL block is via bind variable or a procedure parameter. Can cursor variables be stored in PL/SQL tables.If yes how.If not why. No, a cursor variable points a row which cannot be stored in a two-dimensional PL/SQL table.
Difference between procedure and function.
Functions are named PL/SQL blocks that return a value and can be called with arguments procedure a named block that can be called with parameter. A procedure all is a PL/SQL statement by itself, while a Function call is called as part of an expression.
What are different modes of parameters used in functions and procedures.
IN OUT INOUT
What is difference between a formal and an actual parameter?
The variables declared in the procedure and which are passed, as arguments are called actual, the parameters in the procedure declaration. Actual parameters contain the values that are passed to a procedure and receive results. Formal parameters are the placeholders for the values of actual parameters
Can the default values be assigned to actual parameters?
Yes
Can a function take OUT parameters.If not why.
No.A function has to return a value,an OUT parameter cannot return a value.
What is syntax for dropping a procedure and a function .Are these operations possible?
Drop Procedure procedure_name Drop Function function_name
What are ORACLE PRECOMPILERS?
Using ORACLE PRECOMPILERS ,SQL statements and PL/SQL blocks can be contained inside 3GL programs written in C,C++,COBOL,PASCAL, FORTRAN,PL/1 AND ADA. The Precompilers are known as Pro*C,Pro*Cobol,… This form of PL/SQL is known as embedded pl/sql,the language in which pl/sql is embedded is known as the host language. The prcompiler translates the embedded SQL and pl/sql ststements into calls to the precompiler runtime library.The output must be compiled and linked with this library to creater an executable.
What is OCI. What are its uses?
Oracle Call Interface is a method of accesing database from a 3GL program. Uses–No precompiler is required,PL/SQL blocks are executed like other DML statements. The OCI library provides -functions to parse SQL statements -bind input variables -bind output variables -execute statements -fetch the results
Difference between database triggers and form triggers?
a) Data base trigger(DBT) fires when a DML operation is performed on a data base table.Form trigger(FT) Fires when user presses a key or navigates between fields on the screen b) Can be row level or statement level No distinction between row level and statement level. c) Can manipulate data stored in Oracle tables via SQL Can manipulate data in Oracle tables as well as variables in forms. d) Can be fired from any session executing the triggering DML statements. Can be fired only from the form that define the trigger. e) Can cause other database triggers to fire.Can cause other database triggers to fire,but not other form triggers.
C++
C Questions Output Predicting
.NET
1. What is a static class?
2. What is static member?
3. What is static function?
4. What is static constructor?
5. How can we inherit a static variable?
6. How can we inherit a static member?
7. Can we use a static function with a non-static variable?
8. How can we access static variable?
9. Why main function is static?
10. How will you load dynamic assembly? How will create assemblies at run time?
11. What is Reflection?
12. If I have more than one version of one assembly, then how will I use old version
(how/where to specify version number?) in my application?
13. How do you create threading in.NET? What is the namespace for that?
14. What do you mean by Serialize and MarshalByRef?
15. What is the difference between Array and LinkedList?
16. What is Asynchronous call and how it can be implemented using delegates?
17. How to create events for a control? What are custom events? How to create it?
18. If you want to write your own dot net language, what steps you will you take care?
19. Describe the difference between inline and code behind - which is best in a loosely coupled solution?
20. How dot net compiled code will become platform independent?
21. Without modifying source code if we compile again, will it be generated MSIL again?
22. How does you handle this COM components developed in other programming languages in.NET?
23. How CCW (Com Callable Wrapper) and RCW (Runtime Callable Wrappers) works?
24. What are the new thee features of COM+ services, which are not there in COM (MTS)?
25. What are the differences between COM architecture and.NET architecture?
26. Can we copy a COM dll to GAC folder?
27. What is Shared and Repeatable Inheritance?
28. Can you explain what inheritance is and an example of when you might use it?
29. How can you write a class to restrict that only one object of this class can be created (Singleton class)?
30. What are virtual destructors?
31. What is close method? How its different from Finalize and Dispose?
32. What is Boxing and UnBoxing?
33. What is check/uncheck?
34. What is the use of base keyword? Tell me a practical example for base keyword’s usage?
35. What are the different.NET tools which you used in projects?
36. What will do to avoid prior case?
37. What happens when you try to update data in a dataset in.NET while the record is already
deleted in SQL Server as backend?
38. What is concurrency? How will you avoid concurrency when dealing with dataset?
39. One user deleted one row after that another user through his dataset was trying to update same row.
What will happen? How will you avoid this problem?
40. How do you merge two datasets into the third dataset in a simple manner?
41. If you are executing these statements in commandObject. “Select * from Table1; Select * from Table2″
How you will deal result set?
42. How do you sort a dataset.
43. If a dataset contains 100 rows, how to fetch rows between 5 and 15 only?
44. What is the use of Parameter object?
45. How to generateXML from a dataset and vice versa?
46. How do you implement locking concept for dataset?
47. How will you do Redo and Undo in TextBox control?
48. How to implement DataGrid in.NET? How would you make a combo-box appear in one column of a DataGrid?
What are the ways to show data grid inside a data grid for a master details type of tables? If we write any
code for DataGrid methods. what is the access specifier used for that methods in the code behind file and why?
49. How can we create Tree control in asp.NET?
50. Write a program in C# to find the angle between the hours and minutes in a clock?
51. Write a program to create a user control with name and surname as data members and login as method
and also the code to call it.
52. How can you read 3rd line from a text file?
53. Explain the code behind wors and contrast that using the inline style.
54. Explain different types of HTML, Web and server controls.
55. What are the differences between user control and server control?
56. How server form post-back works?
57. Can the action attribute of a server-side tag be set to a value and if not how can you possibly
pass data from a form page to a subsequent page?
58. How would ASP and ASP.NET apps run at the same time on the same server?
59. What are good ADO.NET object to replace to ADO Recordset object.
60. Explain the differences between Server-side code and Client-side code.
61. What type of code(server or client) is found in a Code-Behind class?
62. Should validation (did the user enter a real date) occur server-side or client-side? Why?
63. What does the “EnableViewState” property do? Why would I want it on or off?
64. What is the difference between Server.Transfer and response.Redirect? Why?
65. Can you give an example of when it would be appropriate to use a web service as opposed to
a non-serviced.NET component?
66. Let’s say I have an existing application written using VB6 and this application utilizes Windows 2000
COM+ transaction services. How would you approach migrating this application to.NET?
67. If I am developing an application that must accomodate multiple security levels though secure
login and my ASP.NET web application is spanned across three web-servers (using round-robin load balancing).
What would be the best approach to maintain login-in state for the users?
68. What are ASP.NET web forms? How is this technology different than what is available though ASP(1.0-3.0)?
69. How does VB.NET achieve polymorphism?
70. How does C# achieve polymorphism?
71. Can you explain what is Inheritance and an example in VB.NET and C# of when you might use it?
72. Describe difference between inline and code-behind?
73. What is loosely coupled solution in.NET?
74. What is diffgram?
75. Where would you use an iHTTPModule and what are the limitations of any approach you might take in implementing one?
76. What are the Advantages and DisAdvantages of viewstate?
77. Describe session handling in a webform, how does it work and what are the limitations?
78. How would you get ASP.NET running in Apache web servers? Explain it’s limitations.
79. What is MSIL and why should my developers need an appreciation of it if at all?
80. Which methos do you invoke on the DataAdapter control to load your generated dataset with data?
81. Can you edit data in Repeater control? How?
82. Which template must you provide, in order to display data in a Repeater control?
83. How can you provide an alternating color scheme in a Repeater control?
84. What property must you set, and what method must you call in your code, in order to bind the data
from some data source to the repeater control?
85. What base class do all web forms inherit from?
86. What method do you use to explicitly kill a user’s session? How?
87. How do you turn off cookies for one page in your site? Give an example.
88. Which two properties are on every validation control?
89. What tags do you need to add within the asp:datagrid tags to bind columns manually? Give an example.
90. How do you create a permanent cookie?
91. What tag do you use to add a hyperlink column to the dataGrid?
92. What is the standard you use to wrap up a call to a Web Service?
93. Which method do you use to redirect the user to another page without performing a round trip to the client? How?
94. What is the transport protocol you use to call a Seb Service SOAP?
95. What does WSDL stand for?
96. What property do you have to set to tell the grid which page to go to when using the Pager object?
97. Where on the Internet would you look for Web Services?
98. What tags do you need to add within the asp:datagrid tags to bind columns manually? How?
99. Which property on a Combo Box do you set with a column name, prior to setting the DataSource, to display data in the combo box?
100. How is a property designated as read-only?
101. Which control would you use if you needed to make sure the values in two different controls matched?
ASP.NET
1. Describe the difference between a Thread and a Process?
2. What is a Windows Service and how does its lifecycle differ from a .standard. EXE?
3. What is the maximum amount of memory any single process on Windows can address?
Is this different than the maximum virtual memory for the system? How would this affect a system design?
4. What is the difference between an EXE and a DLL?
5. What is strong-typing versus weak-typing? Which is preferred? Why?
6. What.s wrong with a line like this? DateTime.Parse(myString
7. What are PDBs? Where must they be located for debugging to work?
8. What is cyclomatic complexity and why is it important?
9. Write a standard lock() plus double check to create a critical section around a variable access.
10. What is FullTrust? Do GAC’ed assemblies have FullTrust?
11. What benefit does your code receive if you decorate it with attributes demanding specific Security permissions?
12. What does this do? gacutil /l | find /i about
13. What does this do? sn -t foo.dll
14. What ports must be open for DCOM over a firewall? What is the purpose of Port 135?
15. Contrast OOP and SOA. What are tenets of each
16. How does the XmlSerializer work? What ACL permissions does a process using it require?
17. Why is catch(Exception) almost always a bad idea?
18. What is the difference between Debug.Write and Trace.Write? When should each be used?
19. What is the difference between a Debug and Release build? Is there a significant speed difference? Why or why not?
20. Does JITting occur per-assembly or per-method? How does this affect the working set?
21. Contrast the use of an abstract base class against an interface?
22. What is the difference between a.Equals(b) and a == b?
23. In the context of a comparison, what is object identity versus object equivalence?
24. How would one do a deep copy in .NET?
25. Explain current thinking around IClonable.
26. What is boxing?
27. Is string a value type or a reference type?
28. What is the maximum length of a varchar field in SQL Server?
29. How do you define an integer in SQL Server?
30. How do you separate business logic while creating an ASP.NET application?
31. If there is a calendar control to be included in each page of your application, and
we do not intend to use the Microsoft-provided calendar control, how do you develop it?
Do you copy and paste the code into each and very page of your application?
32. How do you debug an ASP.NET application?
33. How do you deploy an ASP.NET application?
34. Name a few differences between .NET application and a Java application?
35. Specify the best ways to store variables so that we can access them in various pages of ASP.NET application?
36. What are the XML files that are important in developing an ASP.NET application?
37. What is XSLT and what is its use?
38. Can you give an example of what might be best suited to place in the application_Start and Session_Start subroutines?
39. Can you explain the difference between an ADO.NET Dataset and an ADO Recordset?
40. Can you give an example of when it would be appropriate to use a web service as opposed to a non-serviced .NET component
41. What are good ADO.NET object(s) to replace the ADO Recordset object.?
42. How would ASP and ASP.NET apps run at the same time on the same server?
43. Can the action attribute of a server-side tag be set to a value and if not how can you
possibly pass data from a form page to a subsequent page. Briefly describe the role of global.asax.
44. Briefly explain how server form post-back works (perhaps ask about view state as well).?
45. Briefly explain what user controls are and what server controls are and the differences between the two.
46. Briefly explain how the server control validation controls work.?
47. What are HTML controls, Web controls, and server controls?
48. Briefly explain how code behind works and contrast that using the inline style.?
49. How many classes can a single .NET DLL contain?
50. True or False: To test a Web service you must create a windows application or Web application to consume this service?
51. Which control would you use if you needed to make sure the values in two different controls matched?
52. How is a property designated as read-only?
53. Which property on a Combo Box do you set with a column name, prior to setting the DataSource, to display data in the combo box?
54. What tags do you need to add within the asp:datagrid tags to bind columns manually.?
55. Where on the Internet would you look for Web services?
56. the Pager object?
57. What property do you have to set to tell the grid which page to go to when using ?
58. What does WSDL stand for?
59. True or False: A Web service can only be written in .NET?
60. What is the transport protocol you use to call a Web service SOAP?
61. Which method do you use to redirect the user to another page without performing a round trip to the client?
62. What is the standard you use to wrap up a call to a Web service?
63. What tag do you use to add a hyperlink column to the DataGrid?
64. How do you create a permanent cookie?
65. What tags do you need to add within the asp:datagrid tags to bind columns manually?
66. Which two properties are on every validation control?
67. How do you turn off cookies for one page in your site?
68. Can you explain what inheritance is and an example of when you might use it?
69. What method do you use to explicitly kill a user s session?
70. What base class do all Web Forms inherit from? 71. What property must you set, and what method must you call in your code, in order to bind
the data from some data source to the Repeater control?
72. How can you provide an alternating color scheme in a Repeater control?
73. Which template must you provide, in order to display data in a Repeater control?
74. Can you edit data in the Repeater control?
75. Which method do you invoke on the DataAdapter control to load your generated dataset with data?
76. In what order do the events of an ASPX page execute. As a developer is it important to understand these events?
77. Whats MSIL, and why should my developers need an appreciation of it if at all?
78. How would you get ASP.NET running in Apache web servers - why would you even do this?
79. Describe session handling in a webfarm, how does it work and what are the limits?
80. What are the disadvantages of viewstate/what are the benefits?
81. Can you explain what inheritance is and an example of when you might use it?
82. Where would you use an iHTTPModule, and what are the limitations of any approach you might take in implementing one?
83. How would you implement inheritance using VB.NET/C#?
84. Describe the difference between inline and code behind - which is best in a loosely coupled solution.
85. Whats an assembly ..?
86. How would you implement inheritance using VB.NET/C#?
87. How does VB.NET/C# achieve polymorphism?
88. Can you give an example of what might be best suited to place in the Application Start and Session Start subroutines?
89. Can you explain the difference between an ADO.NET Dataset and an ADO Recordset?
90. Can you give an example of when it would be appropriate to use a web service as opposed to a non-serviced .NET component
91. What is the difference between Servers? Transfer and Response. Redirect? Why would I choose one over the other?
92. What does the "EnableViewState" property do? Why would I want it on or off?
93. Should validation (did the user enter a real date) occur server-side or client-side? Why?
94. What type of code (server or client) is found in a Code-Behind class?
95. Explain the differences between Server-side and Client-side code?
Struts
1. What is Struts?
1.Struts is a web page development framework and an open source software that helps developers build web applications quickly and easily. Struts combines
Java Servlets, Java Server Pages, custom tags, and message resources into a unified framework. It is a cooperative, synergistic platform, suitable for
development teams, independent developers, and everyone between.
2.The core of the Struts framework is a flexible control layer based on standard technologies like Java Servlets, JavaBeans, ResourceBundles, and XML, as
well as various Jakarta Commons packages. Struts encourages application architectures based on the Model 2 approach, a variation of the classic
Model-View-Controller (MVC) design paradigm. Struts provides its own Controller component and integrates with other technologies to provide the Model and
the View. For the Model, Struts can interact with standard data access technologies, like JDBC and EJB, as well as most any third-party packages, like
Hibernate, iBATIS, or Object Relational Bridge. For the View, Struts works well with JavaServer Pages, including JSTL and JSF, as well as Velocity
Templates, XSLT, and other presentation systems. The Struts framework provides the invisible underpinnings every professional web application needs to
survive. Struts helps you create an extensible development environment for your application, based on published standards and proven design patterns.
3. Struts Frame work is the implementation of Model-View-Controller (MVC) design pattern for the JSP. Struts is maintained as a part of Apache Jakarta
project and is open source. Struts Framework is suited for the application of any size. Latest version of struts can be downloaded from
http://jakarta.apache.org/. We are using jakarta-struts-1.1 and jakarta-tomcat-5.0.4 for this tutorial.
2. How is the MVC design pattern used in Struts framework?
In the MVC design pattern, application flow is mediated by a central Controller. The Controller delegates requests to an appropriate handler. The
handlers are tied to a Model, and each handler acts as an adapter between the request and the Model. The Model represents, or encapsulates, an
application's business logic or state. Control is usually then forwarded back through the Controller to the appropriate View. The forwarding can be
determined by consulting a set of mappings, usually loaded from a database or configuration file. This provides a loose coupling between the View and
Model, which can make an application significantly easier to create and maintain.
Controller--Servlet controller which supplied by Struts itself; View --- what you can see on the screen, a JSP page and presentation components; Model
--- System state and a business logic JavaBeans.
3. Who makes the Struts?
Struts is hosted by the Apache Software Foundation(ASF) as part of its Jakarta project, like Tomcat, Ant and Velocity.
4. Why it called Struts?
Because the designers want to remind us of the invisible underpinnings that hold up our houses, buildings, bridges, and ourselves when we are on stilts.
This excellent description of Struts reflect the role the Struts plays in developing web applications.
5. Do we need to pay the Struts if being used in commercial purpose?
No. Struts is available for commercial use at no charge under the Apache Software License. You can also integrate the Struts components into your own
framework just as if they were written in house without any red tape, fees, or other hassles.
6. What are the core classes of Struts?
Action, ActionForm, ActionServlet, ActionMapping, ActionForward are basic classes of Struts.
7. What is the design role played by Struts?
The role played by Struts is controller in Model/View/Controller(MVC) style. The View is played by JSP and Model is played by JDBC or generic data source
classes. The Struts controller is a set of programmable components that allow developers to define exactly how the application interacts with the user.
8. What configuration files are used in Struts?
ApplicationResources.properties
struts-config.xml
These two files are used to bridge the gap between the Controller and the Model.
9. What helpers in the form of JSP pages are provided in Struts framework?
--struts-html.tld
--struts-bean.tld
--struts-logic.tld
10. Is Struts efficient?
- The Struts is not only thread-safe but thread-dependent(instantiates each Action once and allows other requests to be threaded through the original object.
- ActionForm beans minimize subclass code and shorten subclass hierarchies
- The Struts tag libraries provide general-purpose functionality
- The Struts components are reusable by the application
- The Struts localization strategies reduce the need for redundant JSPs
- The Struts is designed with an open architecture--subclass available
- The Struts is lightweight (5 core packages, 5 tag libraries)
- The Struts is open source and well documented (code to be examined easily)
- The Struts is model neutral
11. How you will enable front-end validation based on the xml in validation.xml?
The < html:javascript > tag to allow front-end validation based on the xml in validation.xml. For example the code: < html:javascript formName=logonForm
dynamicJavascript=true staticJavascript=true / > generates the client side java script for the form logonForm as defined in the validation.xml file. The
< html:javascript > when added in the jsp file generates the client site validation script.
12. What is ActionServlet?
The class org.apache.struts.action.ActionServlet is the called the ActionServlet. In the the Jakarta Struts Framework this class plays the role of
controller. All the requests to the server goes through the controller. Controller is responsible for handling all the requests.
13. How you will make available any Message Resources Definitions file to the Struts Framework Environment?
Message Resources Definitions file are simple .properties files and these files contains the messages that can be used in the struts project. Message
Resources Definitions files can be added to the struts-config.xml file through < message-resources / > tag. Example: < message-resources parameter=
MessageResources / >
14. What is Action Class?
The Action Class is part of the Model and is a wrapper around the business logic. The purpose of Action Class is to translate the HttpServletRequest to
the business logic. To use the Action, we need to Subclass and overwrite the execute() method. In the Action Class all the database/business processing
are done. It is advisable to perform all the database related stuffs in the Action Class. The ActionServlet (commad) passes the parameterized class to
Action Form using the execute() method. The return type of the execute method is ActionForward which is used by the Struts Framework to forward the
request to the file as per the value of the returned ActionForward object.
15. How Struts control data flow?
Struts implements the MVC/Layers pattern through the use of ActionForwards and ActionMappings to keep control-flow decisions out of presentation layer.
16. Write code of any Action Class?
Here is the code of Action Class that returns the ActionForward object.
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
import org.apache.struts.action.Action;
import org.apache.struts.action.ActionForm;
import org.apache.struts.action.ActionForward;
import org.apache.struts.action.ActionMapping;
public class TestAction extends Action
{
public ActionForward execute(
ActionMapping mapping,
ActionForm form,
HttpServletRequest request,
HttpServletResponse response) throws Exception
{
return mapping.findForward(\"testAction\");
}
}
17. What is ActionForm?
An ActionForm is a JavaBean that extends org.apache.struts.action.ActionForm. ActionForm maintains the session state for web application and the
ActionForm object is automatically populated on the server side with data entered from a form on the client side.
18. What is Struts Validator Framework?
Struts Framework provides the functionality to validate the form data. It can be use to validate the data on the users browser as well as on the server
side. Struts Framework emits the java scripts and it can be used validate the form data on the client browser. Server side validation of form can be
accomplished by sub classing your From Bean with DynaValidatorForm class. The Validator framework was developed by David Winterfeldt as third-party
add-on to Struts. Now the Validator framework is a part of Jakarta Commons project and it can be used with or without Struts. The Validator framework
comes integrated with the Struts Framework and can be used without doing any extra settings.
19. Give the Details of XML files used in Validator Framework?
The Validator Framework uses two XML configuration files validator-rules.xml and validation.xml. The validator-rules.xml defines the standard validation
routines, these are reusable and used in validation.xml. to define the form specific validations. The validation.xml defines the validations applied to a
form bean.
20. How you will display validation fail errors on jsp page?
The following tag displays all the errors:
< html:errors/ >
21. Can I use other beans or hashmaps with ActionForms?
Yes. There are several ways that you can use other beans or hashmaps with ActionForms.
- ActionForms can have other beansor hashmaps as properties
- "Value Beans" or "Data Transfer Objects" (DTOs) can be used independently of ActionForms to transfer data to the view
- ActionForms can use Maps to support "dynamic" properties (since Struts 1.1)
you. There is nothing preventing you from using other beans, or including them in your form beans. Here are some examples:
Collections as properties Suppose that you need to display a pulldown list of available colors on an input form in your application. You can include a
string-valued colorSelected property in your ActionForm to represent the user's selection and a colorOptions property implemented as a Collection (of
strings) to store the available color choices. Assuming that you have defined the getters and setters for the colorSelected and colorOptions properties
in your orderEntryForm form bean, you can render the pulldown list using:
<html:select property="colorSelected">
<html:options property="colorOptions" name="orderEntryForm"/>
</html:select>
The list will be populated using the strings in the colorOptions collection of the orderEntryForm and the value that the user selects will go into the
colorSelected property that gets posted to the subsequent Action. Note that we are assuming here that the colorOptions property of the orderEntryForm has
already been set.
See How can I prepopulate a form? for instructions on how to set form bean properties before rendering edit forms that expect properties to be pre-set.
Independent DTO An Action that retrieves a list of open orders (as an ArrayList of Order objects) can use a DTO independently of any form bean to
transfer search results to the view. First, the Action's execute method performs the search and puts the DTO into the request:
ArrayList results = businessObject.executeSearch(searchParameters);
request.setAttribute("searchResults",results);
Then the view can iterate through the results using the "searchResults" request key to reference the DTO:
<logic:iterate id="order" name="searchResults" type="com.foo.bar.Order">
<tr><td><bean:write name="order" property="orderNumber"/><td>
<td>..other properties...</td></tr>
</logic:iterate>
22. Why do the Struts tags provide for so little formatting?
The Struts tags seem to provide only the most rudimentary functionality. Why is there not better support for date formatting and advanced string
handling?
Three reasons:
First, work started on the JSTL and we didn't want to duplicate the effort.
Second, work started on Java Server Faces, and we didn't want to duplicate that effort either.
Third, in a Model 2 application, most of the formatting can be handled in the ActionForms (or in the business tier), so all the tag has to do is spit out
a string. This leads to better reuse since the same "how to format" code does not need to be repeated in every instance. You can "say it once" in a
JavaBean and be done with it. Why don't the Struts taglibs offer more layout options?
Since the Struts tags are open source, you can extend them to provide whatever additional formatting you may need. If you are interested in a pre-written
taglib that offers more layout options, see the struts-layout taglib.
In the same arena, there is a well regarded contributor taglib that can help you create Menus for your Struts applications.
23. Why does the <html:link> tag URL-encode javascript and mailto links?
The <html:link> tag is not intended for use with client-side references like those used to launch Javascripts or email clients. The purpose of link tag
is to interject the context (or module) path into the URI so that your server-side links are not dependent on your context (or module) name. It also
encodes the link, as needed, to maintain the client's session on the server. Neither feature applies to client-side links, so there is no reason to use
the <html:link> tag. Simply markup the client-side links using the standard tag.
24. Why does the <html:link> tag URL-encode javascript and mailto links?
The <html:link> tag is not intended for use with client-side references like those used to launch Javascripts or email clients. The purpose of link tag
is to interject the context (or module) path into the URI so that your server-side links are not dependent on your context (or module) name. It also
encodes the link, as needed, to maintain the client's session on the server. Neither feature applies to client-side links, so there is no reason to use
the <html:link> tag. Simply markup the client-side links using the standard tag.
25. How can I scroll through list of pages like the search results in google?
Many Struts developers use the Pager from the JSPTags site.
26. How would you display “validation fail” errors on a JSP page?
Following tag displays all the errors: <html:errors/>
27. How can one enable front-end validation based on the xml in validation.xml?
The <html:javascript> tag allows front-end validation based on the xml in validation.xml.
For example the code:
generates the client side JavaScript for the form "logonForm" as defined in the validation.xml file.
The <html:javascript> when added in the JSP file generates the client side validation script.
Python
1. What is Python?
Python is an interpreted, interactive, object-oriented programming language. It incorporates
modules, exceptions, dynamic typing, very high level dynamic data types, and classes. Python
combines remarkable power with very clear syntax. It has interfaces to many system calls and
libraries, as well as to various window systems, and is extensible in C or C++. It is also
usable as an extension language for applications that need a programmable interface. Finally,
Python is portable: it runs on many Unix variants, on the Mac, and on PCs under MS-DOS, Windows,
Windows NT, and OS/2.
2. Is there a tool to help find bugs or perform static analysis?
Yes.
PyChecker is a static analysis tool that finds bugs in Python source code and warns about code
complexity and style. Pylint is another tool that checks if a module satisfies a coding standard,
and also makes it possible to write plug-ins to add a custom feature.
3. What is a negative index?
Python sequences are indexed with positive numbers and negative numbers. For positive numbers 0 is
the first index 1 is the second index and so forth. For negative indices -1 is the last index and -2
is the penultimate (next to last) index and so forth. Think of seq[-n] as the same as seq[len(seq)-n].
Using negative indices can be very convenient. For example S[:-1] is all of the string except for its
last character, which is useful for removing the trailing newline from a string.
4. What are the rules for local and global variables in Python?
In Python, variables that are only referenced inside a function are implicitly global. If a variable
is assigned a new value anywhere within the function's body, it's assumed to be a local. If a variable
is ever assigned a new value inside the function, the variable is implicitly local, and you need to
explicitly declare it as 'global'.
Though a bit surprising at first, a moment's consideration explains this. On one hand, requiring global
for assigned variables provides a bar against unintended side-effects. On the other hand, if global was
required for all global references, you'd be using global all the time. You'd have to declare as global
every reference to a builtin function or to a component of an imported module. This clutter would defeat
the usefulness of the global declaration for identifying side-effects.
5. How do I copy an object in Python?
In general, try copy.copy() or copy.deepcopy() for the general case. Not all objects can be copied, but most can.
Some objects can be copied more easily. Dictionaries have a copy() method:
newdict = olddict.copy()
Sequences can be copied by slicing:
new_l = l[:]
6. How can I find the methods or attributes of an object?
For an instance x of a user-defined class, dir(x) returns an alphabetized list of the names containing
the instance attributes and methods and attributes defined by its class.
7. How do I convert a string to a number?
For integers, use the built-in int() type constructor, e.g. int('144') == 144. Similarly, float() converts
to floating-point, e.g. float('144') == 144.0.
By default, these interpret the number as decimal, so that int('0144') == 144 and int('0x144') raises
ValueError. int(string, base) takes the base to convert from as a second optional argument,
so int('0x144', 16) == 324. If the base is specified as 0, the number is interpreted using Python's
rules: a leading '0' indicates octal, and '0x' indicates a hex number.
Do not use the built-in function eval() if all you need is to convert strings to numbers. eval() will be
significantly slower and it presents a security risk: someone could pass you a Python expression that
might have unwanted side effects. For example, someone could pass __import__('os').system("rm -rf $HOME")
which would erase your home directory.
eval() also has the effect of interpreting numbers as Python expressions, so that e.g. eval('09') gives
a syntax error because Python regards numbers starting with '0' as octal (base 8).
8. How do I convert a number to a string?
To convert, e.g., the number 144 to the string '144', use the built-in function str(). If you want a
hexadecimal or octal representation, use the built-in functions hex() or oct(). For fancy formatting,
use the % operator on strings, e.g. "%04d" % 144 yields '0144' and "%.3f" % (1/3.0) yields '0.333'.
See the library reference manual for details.
9. How do you remove duplicates from a list?
If you don't mind reordering the list, sort it and then scan from the end of the list, deleting duplicates as you go:
if List:
List.sort()
last = List[-1]
for i in range(len(List)-2, -1, -1):
if last==List[i]: del List[i]
else: last=List[i]
If all elements of the list may be used as dictionary keys (i.e. they are all hashable) this is often faster
d = {}
for x in List: d[x]=x
List = d.values()
10. How do you make an array in Python?
Use a list:
["this", 1, "is", "an", "array"]
Lists are equivalent to C or Pascal arrays in their time complexity; the primary difference is
that a Python list can contain objects of many different types.
The array module also provides methods for creating arrays of fixed types with compact representations,
but they are slower to index than lists. Also note that the Numeric extensions and others define
array-like structures with various characteristics as well.
To get Lisp-style linked lists, you can emulate cons cells using tuples:
lisp_list = ("like", ("this", ("example", None) ) )
If mutability is desired, you could use lists instead of tuples. Here the analogue of lisp car is
lisp_list[0] and the analogue of cdr is lisp_list[1]. Only do this if you're sure you really need to,
because it's usually a lot slower than using Python lists.
JSP
1. What is a JSP and what is it used for?
Java Server Pages (JSP) is a platform independent presentation layer technology that comes with SUN s J2EE platform.
JSPs are normal HTML pages with Java code pieces embedded in them. JSP pages are saved to *.jsp files. A JSP compiler
is used in the background to generate a Servlet from the JSP page.
2. What is difference between custom JSP tags and beans?
Custom JSP tag is a tag you defined. You define how a tag, its attributes and its body are interpreted, and then group your
tags into collections called tag libraries that can be used in any number of JSP files. To use custom JSP tags, you need to
define three separate components:
1. the tag handler class that defines the tag\'s behavior
2. the tag library descriptor file that maps the XML element names to the tag implementations
3. the JSP file that uses the tag library
When the first two components are done, you can use the tag by using taglib directive:
<%@ taglib uri="xxx.tld" prefix="..." %>
Then you are ready to use the tags you defined. Let's say the tag prefix is test:
MyJSPTag or
JavaBeans are Java utility classes you defined. Beans have a standard format for Java classes. You use tags
to declare a bean and use
to set value of the bean class and use
to get value of the bean class.
<%=identifier.getclassField() %>
Custom tags and beans accomplish the same goals -- encapsulating complex behavior into simple and accessible forms.
There are several differences:
Custom tags can manipulate JSP content; beans cannot.
Complex operations can be reduced to a significantly simpler form with custom tags than with beans. Custom tags require
quite a bit more work to set up than do beans.
Custom tags usually define relatively self-contained behavior, whereas beans are often defined in one servlet and used in
a different servlet or JSP page.
Custom tags are available only in JSP 1.1 and later, but beans can be used in all JSP 1.x versions.
3. What are the two kinds of comments in JSP and what's the difference between them.
<%-- JSP Comment --%>
4. What is JSP technology?
Java Server Page is a standard Java extension that is defined on top of the servlet Extensions. The goal of JSP is the simplified
creation and management of dynamic Web pages. JSPs are secure, platform-independent, and best of all, make use of Java as a
server-side scripting language.
5. What is JSP page?
A JSP page is a text-based document that contains two types of text: static template data, which can be expressed in any text-based
format such as HTML, SVG, WML, and XML, and JSP elements, which construct dynamic content.
6. What are the implicit objects?
Implicit objects are objects that are created by the web container and contain information related to a particular request, page,
or application. They are:
--request
--response
--pageContext
--session
--application
--out
--config
--page
--exceptio
7. How many JSP scripting elements and what are they?
There are three scripting language elements:
--declarations
--scriptlets
--expressions
8. Why are JSP pages the preferred API for creating a web-based client program?
Because no plug-ins or security policy files are needed on the client systems(applet does). Also, JSP pages enable cleaner
and more module application design because they provide a way to separate applications programming from web page design.
This means personnel involved in web page design do not need to understand Java programming language syntax to do their jobs.
9. Is JSP technology extensible?
YES. JSP technology is extensible through the development of custom actions, or tags, which are encapsulated in tag libraries.
10. Can we use the constructor, instead of init(), to initialize servlet?
Yes , of course you can use the constructor instead of init(). There’s nothing to stop you. But you shouldn’t. The original
reason for init() was that ancient versions of Java couldn’t dynamically invoke constructors with arguments, so there was no
way to give the constructur a ServletConfig. That no longer applies, but servlet containers still will only call your no-arg
constructor. So you won’t have access to a ServletConfig or ServletContext.
11. How can a servlet refresh automatically if some new data has entered the database?
You can use a client-side Refresh or Server Push.
12. The code in a finally clause will never fail to execute, right?
Using System.exit(1); in try block will not allow finally code to execute.
13. How many messaging models do JMS provide for and what are they?
JMS provide for two messaging models, publish-and-subscribe and point-to-point queuing.
14. What information is needed to create a TCP Socket?
The Local Systems IP Address and Port Number. And the Remote System’s IPAddress and Port Number.
15. What Class.forName will do while loading drivers?
It is used to create an instance of a driver and register it with the DriverManager. When you have loaded a driver,
it is available for making a connection with a DBMS.
XML
1. What is XML?
XML is the Extensible Markup Language. It improves the functionality of the Web by letting you identify your information
in a more accurate, flexible, and adaptable way.
It is extensible because it is not a fixed format like HTML (which is a single, predefined markup language). Instead, XML
is actually a metalanguage—a language for describing other languages—which lets you design your own markup languages for
limitless different types of documents. XML can do this because it's written in SGML, the international standard metalanguage
for text document markup (ISO 8879).
2. What is a markup language?
A markup language is a set of words and symbols for describing the identity of pieces of a document (for example ‘this is a
paragraph’, ‘this is a heading’, ‘this is a list’, ‘this is the caption of this figure’, etc). Programs can use this with a
stylesheet to create output for screen, print, audio, video, Braille, etc.
Some markup languages (eg those used in wordprocessors) only describe appearances (‘this is italics’, ‘this is bold’), but
this method can only be used for display, and is not normally re-usable for anything else.
3. Where should I use XML?
Its goal is to enable generic SGML to be served, received, and processed on the Web in the way that is now possible with HTML.
XML has been designed for ease of implementation and for interoperability with both SGML and HTML.
Despite early attempts, browsers never allowed other SGML, only HTML (although there were plugins), and they allowed it (even
encouraged it) to be corrupted or broken, which held development back for over a decade by making it impossible to program for
it reliably. XML fixes that by making it compulsory to stick to the rules, and by making the rules much simpler than SGML.
But XML is not just for Web pages: in fact it's very rarely used for Web pages on its own because browsers still don't provide
reliable support for formatting and transforming it. Common uses for XML include:
Information identification
because you can define your own markup, you can define meaningful names for all your information items. Information storage
because XML is portable and non-proprietary, it can be used to store textual information across any platform. Because it is backed
by an international standard, it will remain accessible and processable as a data format. Information structure
XML can therefore be used to store and identify any kind of (hierarchical) information structure, especially for long, deep, or
complex document sets or data sources, making it ideal for an information-management back-end to serving the Web. This is its most
common Web application, with a transformation system to serve it as HTML until such time as browsers are able to handle XML consistently.
Publishing
The original goal of XML as defined in the quotation at the start of this section. Combining the three previous topics (identity,
storage, structure) means it is possible to get all the benefits of robust document management and control (with XML) and publish
to the Web (as HTML) as well as to paper (as PDF) and to other formats (eg Braille, Audio, etc) from a single source document by
using the appropriate stylesheets. Messaging and data transfer
XML is also very heavily used for enclosing or encapsulating information in order to pass it between different computing systems
which would otherwise be unable to communicate. By providing a lingua franca for data identity and structure, it provides a common
envelope for inter-process communication (messaging). Web services
Building on all of these, as well as its use in browsers, machine-processable data can be exchanged between consenting systems,
where before it was only comprehensible by humans (HTML). Weather services, e-commerce sites, blog newsfeeds, AJaX sites, and
thousands of other data-exchange services use XML for data management and transmission, and the web browser for display and
interaction.
4. Why is XML such an important development?
It removes two constraints which were holding back Web developments:
1. dependence on a single, inflexible document type (HTML) which was being much abused for tasks it was never designed for;
2. the complexity of full SGML, whose syntax allows many powerful but hard-to-program options.
XML allows the flexible development of user-defined document types. It provides a robust, non-proprietary, persistent, and verifiable
file format for the storage and transmission of text and data both on and off the Web; and it removes the more complex options of SGML,
making it easier to program for.
5. Describe the role that XSL can play when dynamically generating HTML pages from a relational database.
Even if candidates have never participated in a project involving this type of architecture, they should recognize it as one of the
common uses of XML. Querying a database and then formatting the result set so that it can be validated as an XML document allows
developers to translate the data into an HTML table using XSLT rules. Consequently, the format of the resulting HTML table can be
modified without changing the database query or application code since the document rendering logic is isolated to the XSLT rules.
6. Aren't XML, SGML, and HTML all the same thing?
Not quite; SGML is the mother tongue, and has been used for describing thousands of different document types in many fields of
human activity, from transcriptions of ancient Irish manuscripts to the technical documentation for stealth bombers, and from
patients' clinical records to musical notation. SGML is very large and complex, however, and probably overkill for most common
office desktop applications.
XML is an abbreviated version of SGML, to make it easier to use over the Web, easier for you to define your own document types,
and easier for programmers to write programs to handle them. It omits all the complex and less-used options of SGML in return for
the benefits of being easier to write applications for, easier to understand, and more suited to delivery and interoperability over
the Web. But it is still SGML, and XML files may still be processed in the same way as any other SGML file (see the question on XML
software).
7. Who is responsible for XML?
XML is a project of the World Wide Web Consortium (W3C), and the development of the specification is supervised by an XML Working Group.
A Special Interest Group of co-opted contributors and experts from various fields contributed comments and reviews by email.
XML is a public format: it is not a proprietary development of any company, although the membership of the WG and the SIG represented
companies as well as research and academic institutions. The v1.0 specification was accepted by the W3C as a Recommendation on Feb 10,
1998.
HTML is just one of many SGML or XML applications—the one most frequently used on the Web.
Technical readers may find it more useful to think of XML as being SGML-- rather than HTML++.
8. Why is XML such an important development?
It removes two constraints which were holding back Web developments:
1. dependence on a single, inflexible document type (HTML) which was being much abused for tasks it was never designed for;
2. the complexity of full question A.4, SGML, whose syntax allows many powerful but hard-to-program options.
XML allows the flexible development of user-defined document types. It provides a robust, non-proprietary, persistent, and verifiable
file format for the storage and transmission of text and data both on and off the Web; and it removes the more complex options of SGML,
making it easier to program for.
9. Give a few examples of types of applications that can benefit from using XML.
There are literally thousands of applications that can benefit from XML technologies. The point of this question is not to have the
candidate rattle off a laundry list of projects that they have worked on, but, rather, to allow the candidate to explain the rationale
for choosing XML by citing a few real world examples. For instance, one appropriate answer is that XML allows content management systems
to store documents independently of their format, which thereby reduces data redundancy. Another answer relates to B2B exchanges or supply
chain management systems. In these instances, XML provides a mechanism for multiple companies to exchange data according to an agreed upon
set of rules. A third common response involves wireless applications that require WML to render data on hand held devices.
10. Give a few examples of types of applications that can benefit from using XML.
There are literally thousands of applications that can benefit from XML technologies. The point of this question is not to have the
candidate rattle off a laundry list of projects that they have worked on, but, rather, to allow the candidate to explain the rationale
for choosing XML by citing a few real world examples. For instance, one appropriate answer is that XML allows content management systems
to store documents independently of their format, which thereby reduces data redundancy. Another answer relates to B2B exchanges or supply
chain management systems. In these instances, XML provides a mechanism for multiple companies to exchange data according to an agreed upon
set of rules. A third common response involves wireless applications that require WML to render data on hand held devices.
11. What is DOM and how does it relate to XML?
The Document Object Model (DOM) is an interface specification maintained by the W3C DOM Workgroup that defines an application independent
mechanism to access, parse, or update XML data. In simple terms it is a hierarchical model that allows developers to manipulate XML documents
easily Any developer that has worked extensively with XML should be able to discuss the concept and use of DOM objects freely. Additionally,
it is not unreasonable to expect advanced candidates to thoroughly understand its internal workings and be able to explain how DOM differs
from an event-based interface like SAX.
12. What is SOAP and how does it relate to XML?
The Simple Object Access Protocol (SOAP) uses XML to define a protocol for the exchange of information in distributed computing environments.
SOAP consists of three components: an envelope, a set of encoding rules, and a convention for representing remote procedure calls. Unless
experience with SOAP is a direct requirement for the open position, knowing the specifics of the protocol, or how it can be used in conjunction
with HTTP, is not as important as identifying it as a natural application of XML.
13. Why not just carry on extending HTML?
HTML was already overburdened with dozens of interesting but incompatible inventions from different manufacturers, because it provides only
one way of describing your information.
XML allows groups of people or organizations to question C.13, create their own customized markup applications for exchanging information
in their domain (music, chemistry, electronics, hill-walking, finance, surfing, petroleum geology, linguistics, cooking, knitting, stellar
cartography, history, engineering, rabbit-keeping, question C.19, mathematics, genealogy, etc).
HTML is now well beyond the limit of its usefulness as a way of describing information, and while it will continue to play an important role
for the content it currently represents, many new applications require a more robust and flexible infrastructure.
14. Why should I use XML?
Here are a few reasons for using XML (in no particular order). Not all of these will apply to your own requirements, and you may have
additional reasons not mentioned here (if so, please let the editor of the FAQ know!).
- XML can be used to describe and identify information accurately and unambiguously, in a way that computers can be programmed to
- XML allows documents which are all the same type to be created consistently and without structural errors, because it provides a
absolutely nothing whatever to do with formatting, appearance, or the actual text content of your documents, only the structure of them.
- XML provides a robust and durable format for information storage and transmission. Robust because it is based on a proven standard,
- XML provides a common syntax for messaging systems for the exchange of information between applications. Previously, each messaging
everyone uses the same syntax it makes writing these systems much faster and more reliable.
- XML is free. Not just free of charge (free as in beer) but free of legal encumbrances (free as in speech). It doesn't belong to anyone,
with it, for lots of good reasons, but you don't pay for XML itself).
- XML information can be manipulated programmatically (under machine control), so XML documents can be pieced together from disparate
- XML lets you separate form from content. Your XML file contains your document information (text, data) and identifies its structure:
time to apply the required formatting to the text or data identified by its structure (location, position, rank, order, or whatever).
15. Can you walk us through the steps necessary to parse XML documents?
Superficially, this is a fairly basic question. However, the point is not to determine whether candidates understand the concept of a parser
but rather have them walk through the process of parsing XML documents step-by-step. Determining whether a non-validating or validating parser
is needed, choosing the appropriate parser, and handling errors are all important aspects to this process that should be included in the
candidate's response.
J2EE
What is J2EE?
J2EE is an environment for developing and deploying enterprise applications. The J2EE platform consists of a set of services, application programming
interfaces (APIs), and protocols that provide the functionality for developing multitiered, web-based applications.
What is the J2EE module?
A J2EE module consists of one or more J2EE components for the same container type and one component deployment descriptor of that type.
What are the components of J2EE application?
A J2EE component is a self-contained functional software unit that is assembled into a J2EE application with its related classes and files and
communicates with other components. The J2EE specification defines the following J2EE components:
- Application clients and applets are client components.
- Java Servlet and JavaServer PagesTM (JSPTM) technology components are web components.
- Enterprise JavaBeansTM (EJBTM) components (enterprise beans) are business components.
- Resource adapter components provided by EIS and tool vendors.
What are the four types of J2EE modules?
1. Application client module
2. Web module
3. Enterprise JavaBeans module
4. Resource adapter module
What does application client module contain?
The application client module contains:
--class files,
--an application client deployment descriptor.
Application client modules are packaged as JAR files with a .jar extension.
What are the differences between Ear, Jar and War files? Under what circumstances should we use each one?
There are no structural differences between the files; they are all archived using zip-jar compression. However, they are intended for different
purposes.
--Jar files (files with a .jar extension) are intended to hold generic libraries of Java classes, resources, auxiliary files, etc.
--War files (files with a .war extension) are intended to contain complete Web applications. In this context, a Web application is defined as a single
group of files, classes, resources, .jar files that can be packaged and accessed as one servlet context.
--Ear files (files with a .ear extension) are intended to contain complete enterprise applications. In this context, an enterprise application is
defined as a collection of .jar files, resources, classes, and multiple Web applications.
Each type of file (.jar, .war, .ear) is processed uniquely by application servers, servlet containers, EJB containers, etc.
What is the difference between Session bean and Entity bean?one?
The Session bean and Entity bean are two main parts of EJB container.
Session Bean
--represents a workflow on behalf of a client
--one-to-one logical mapping to a client.
--created and destroyed by a client
--not permanent objects
--lives its EJB container(generally) does not survive system shut down
--two types: stateless and stateful beans
Entity Bean
--represents persistent data and behavior of this data
--can be shared among multiple clients
--persists across multiple invocations
--findable permanent objects
--outlives its EJB container, survives system shutdown
--two types: container managed persistence(CMP) and bean managed persistence(BMP)
What is "applet"
A J2EE component that typically executes in a Web browser but can execute in a variety of other applications or devices that support the applet
programming model.
What is "applet container"
A container that includes support for the applet programming model.
What is "application assembler"
A person who combines J2EE components and modules into deployable application units.
What is "application client"
A first-tier J2EE client component that executes in its own Java virtual machine. Application clients have access to some J2EE platform APIs.
What is "application client container"
A container that supports application client components.
What is "application client module"
A software unit that consists of one or more classes and an application client deployment descriptor.
What is "application component provider"
A vendor that provides the Java classes that implement components' methods, JSP page definitions, and any required deployment descriptors.
What is "application configuration resource file"
An XML file used to configure resources for a JavaServer Faces application, to define navigation rules for the application, and to register converters,
validators, listeners, renderers, and components with the application.
What is "archiving"
The process of saving the state of an object and restoring it.
What is "asant"
A Java-based build tool that can be extended using Java classes. The configuration files are XML-based, calling out a target tree where various tasks
get executed.
What is "attribute"What is "asant"
A qualifier on an XML tag that provides additional information.
What is authentication ?
The process that verifies the identity of a user, device, or other entity in a computer system, usually as a prerequisite to allowing access to
resources in a system. The Java servlet specification requires three types of authentication-basic, form-based, and mutual-and supports digest
authentication.
What is authorization?
The process by which access to a method or resource is determined. Authorization depends on the determination of whether the principal associated with
a request through authentication is in a given security role. A security role is a logical grouping of users defined by the person who assembles the
application. A deployer maps security roles to security identities. Security identities may be principals or groups in the operational environment.
What is authorization constraint?
An authorization rule that determines who is permitted to access a Web resource collection.
What is B2B?
B2B stands for Business-to-business.
What is backing bean?
A JavaBeans component that corresponds to a JSP page that includes JavaServer Faces components. The backing bean defines properties for the components
on the page and methods that perform processing for the component. This processing includes event handling, validation, and processing associated with
navigation.
What is basic authentication?
An authentication mechanism in which a Web server authenticates an entity via a user name and password obtained using the Web application's built-in
authentication mechanism.
What is bean-managed persistence?
The mechanism whereby data transfer between an entity bean's variables and a resource manager is managed by the entity bean.
What is bean-managed transaction?
A transaction whose boundaries are defined by an enterprise bean.
What is binding (XML)?
Generating the code needed to process a well-defined portion of XML data.
What is binding (JavaServer Faces technology)?
Wiring UI components to back-end data sources such as backing bean properties.
What is build file?
The XML file that contains one or more asant targets. A target is a set of tasks you want to be executed. When starting asant, you can select which
targets you want to have executed. When no target is given, the project's default target is executed.
What is business logic?
The code that implements the functionality of an application. In the Enterprise JavaBeans architecture, this logic is implemented by the methods of an
enterprise bean.
What is business method?
A method of an enterprise bean that implements the business logic or rules of an application.
What is callback methods?
Component methods called by the container to notify the component of important events in its life cycle.
What is caller?
Same as caller principal.
What is caller principal?
The principal that identifies the invoker of the enterprise bean method.
What is cascade delete?
A deletion that triggers another deletion. A cascade delete can be specified for an entity bean that has container-managed persistence.
What is CDATA?
A predefined XML tag for character data that means "don't interpret these characters," as opposed to parsed character data (PCDATA), in which the
normal rules of XML syntax apply. CDATA sections are typically used to show examples of XML syntax.
What is certificate authority?
A trusted organization that issues public key certificates and provides identification to the bearer.
What is client-certificate authentication?
An authentication mechanism that uses HTTP over SSL, in which the server and, optionally, the client authenticate each other with a public key
certificate that conforms to a standard that is defined by X.509 Public Key Infrastructure.
What is comment?
In an XML document, text that is ignored unless the parser is specifically told to recognize it.
What is commit?
The point in a transaction when all updates to any resources involved in the transaction are made permanent.
What is component contract?
The contract between a J2EE component and its container. The contract includes life-cycle management of the component, a context interface that the
instance uses to obtain various information and services from its container, and a list of services that every container must provide for its
components.
What is component-managed sign-on?
A mechanism whereby security information needed for signing on to a resource is provided by an application component.
What is connector?
A standard extension mechanism for containers that provides connectivity to enterprise information systems. A connector is specific to an enterprise
information system and consists of a resource adapter and application development tools for enterprise information system connectivity. The resource
adapter is plugged in to a container through its support for system-level contracts defined in the Connector architecture.
What is Connector architecture?
An architecture for integration of J2EE products with enterprise information systems. There are two parts to this architecture: a resource adapter
provided by an enterprise information system vendor and the J2EE product that allows this resource adapter to plug in. This architecture defines a set
of contracts that a resource adapter must support to plug in to a J2EE product-for example, transactions, security, and resource management.
What is container?
An entity that provides life-cycle management, security, deployment, and runtime services to J2EE components. Each type of container (EJB, Web, JSP,
servlet, applet, and application client) also provides component-specific services.
What is container-managed persistence?
The mechanism whereby data transfer between an entity bean's variables and a resource manager is managed by the entity bean's container. .
What is container-managed sign-on?
The mechanism whereby security information needed for signing on to a resource is supplied by the container.
What is container-managed transaction?
A transaction whose boundaries are defined by an EJB container. An entity bean must use container-managed transactions.
What is content?
In an XML document, the part that occurs after the prolog, including the root element and everything it contains.
JAVA
Q Why a thread blocks or enters to waiting state on I/O?
A Threads enters to waiting state or block on I/O because other threads can execute while the I/O operations are performed.
Q What are transient variables in java?
A Transient variables are variable that cannot be serialized.
Q How Observer and Observable are used?
A Subclass of Observable class maintains a list of observers. Whenever an Observable object is updated, it invokes the update () method of each of its observers to notify the observers that it has a changed state. An observer is any object that implements the interface Observer.
Q What is synchronization? A Synchronization is the ability to control the access of multiple threads to shared resources. Synchronization stops multithreading. With synchronization, at a time only one thread will be able to access a shared resource.
Q what is List interface?
A List is an ordered collection of objects.
Q What is a Vector?
A Vector is a grow able array of objects.
Q What is the difference between yield () and sleep ()?
A When a object invokes yield () it returns to ready state. But when an object invokes sleep () method enters to not ready state.
Q What are Wrapper Classes?
A They are wrappers to primitive data types. They allow us to access primitives as objects.
Q Can we call finalize () method?
A Yes. Nobody will stop us to call any method, if it is accessible in our class. But a garbage collector cannot call an object's finalize method if that object is reachable.
Q What is the difference between time slicing and preemptive scheduling?
A In preemptive scheduling, highest priority task continues execution till it enters a not running state or a higher priority task comes into existence. In time slicing, the task continues its execution for a predefined period of time and reenters the pool of ready tasks.
Q What is the initial state of a thread when it is created and started?
A The thread is in ready state.
Q Can we declare an anonymous class as both extending a class and implementing an interface?
A No. An anonymous class can extend a class or implement an interface, but it cannot be declared to do both
Q What are the differences between Boolean & operator and & operator?
A When an expression containing the & operator is evaluated, both operands are evaluated. And the & operator is applied to the operand. When an expression containing && operator is evaluated, the first operand is evaluated. If the first operand returns a value of true then only the second operand is evaluated otherwise the second part will not get executed. && is also called short cut and.
Q What is the use of the finally block?
A Finally is the block of code that executes always. The code in finally block will execute even if an exception is occurred. Finally will not execute when the user calls System.exit().
Q What is an abstract method?
A An abstract method is a method that don't have a body. It is declared with modifier abstract.
JAVA and EJB
1. What is Entity Bean and Session Bean ?
2. What are the methods of Entity Bean?
3. How does Stateful Session bean store its state ?
4. Why does Stateless Session bean not store its state even though it has ejbActivate and ejbPassivate ?
5. What are the services provided by the container ?
6. Types of transaction ?
7. What is bean managed transaction ?
8. Why does EJB needs two interface( Home and Remote Interface) ?
9. What are transaction attributes ?
10. What is the difference between Container managed persistent bean and Bean managed persistent entity bean ?
11. What is J2EE ?
12. What is JTS ?
13. How many entity beans used and how many tables can u use in EJB project ?
14. What is scalable,portability in J2EE?
15. What is Connection pooling?Is it advantageous?
16. Method and class used for Connection pooling ?
17. How to deploy in J2EE(i.e Jar,War file) ?
18. How is entity bean created using Container managed entity bean ?
19. Sotware architechture of EJB ?
20. In Entity bean will the create method in EJB home and ejbCreate in Entity bean have the same parameters ?
21. What methods do u use in Servlet – Applet communication ?
22. What are the types of Servlet ?
23. Difference between HttpServlet and Generic Servlets ?
24. Difference between doGet and doPost ?
25. What are the methods in HttpServlet?
26. What are the types of SessionTracking?
27. What is Cookie ? Why is Cookie used ?
28. If my browser does not support Cookie,and my server sends a cookie instance What will happen ?
29. Why do u use Session Tracking in HttpServlet ?
30. Can u use javaScript in Servlets ?
31. What is the capacity the doGet can send to the server ?
32. What are the type of protocols used in HttpServlet ?
33. Difference between TCP/IP and IP protocol ?
34. Why do you use UniCastRemoteObject in RMI ?
35. How many interfaces are used in RMI?
36. Can Rmi registry be written in the code, without having to write it in the command prompt and if yes where?
37. Why is Socket used ?
38. What are the types of JDBC drivers ?
39. Explain the third driver(Native protocol driver) ?
40. Which among the four driver is pure Java driver ?
41. What are the Isolation level in JDBC transaction ?
42. How do you connect with the database ?
43. How do you connect without the Class.forName (" ") ?
44. What does Class.forName return ?
45. What are the types of statement ?
46. Why is preparedStatement,CallableStatement used for?
47. In real time project which driver did u use ?
48. Difference between AWT and Swing compenents ?
49. Is there any heavy weight component in Swings ?
50. Can the Swing application if you upload in net, be compatible with your browser?
51. What should you do get your browser compatible with swing components?
52. What are the methods in Applet ?
53. When is init(),start() called ?
54. When you navigate from one applet to another what are the methods called ?
55. What is the difference between Trusted and Untrusted Applet ?
56. What is Exception ?
57. What are the ways you can handle exception ?
58. When is try,catch block used ?
59. What is finally method in Exceptions ?
60. What are the types of access modifiers ?
61. What is protected and friendly ?
62. What are the other modifiers ?
63. Is synchronised modifier ?
64. What is meant by polymorphism ?
65. What is inheritance ?
66. What is method Overloading ? What is this in OOPS ?
67. What is method Overriding ? What is it in OOPS ?
68. Does java support multi dimensional arrays ?
69. Is multiple inheritance used in Java ?
70. How do you send a message to the browser in JavaScript ?
71. Does javascript support multidimensional arrays ?
72. Why is XML used mainly?
73. Do use coding for database connectivity in XML?
74. What is DTD ?
75. Is there any tool in java that can create reports ?
Oracle
What is use of a cursor variable? How it is defined.
A cursor variable is associated with different statements at run time, which can hold different values at run time. Static cursors can only be associated with one run time query. A cursor variable is reference type(like a pointer in C). Declaring a cursor variable: TYPE type_name IS REF CURSOR RETURN return_type type_name is the name of the reference type,return_type is a record type indicating the types of the select list that will eventually be returned by the cursor variable.
What should be the return type for a cursor variable.Can we use a scalar data type as return type?
The return type for a cursor must be a record type.It can be declared explicitly as a user-defined or %ROWTYPE can be used. eg TYPE t_studentsref IS REF CURSOR RETURN students%ROWTYPE
How you open and close a cursor variable.Why it is required?
OPEN cursor variable FOR SELECT…Statement CLOSE cursor variable In order to associate a cursor variable with a particular SELECT statement OPEN syntax is used.In order to free the resources used for the query CLOSE statement is used.
How you were passing cursor variables in PL/SQL 2.2?
In PL/SQL 2.2 cursor variables cannot be declared in a package.This is because the storage for a cursor variable has to be allocated using Pro*C or OCI with version 2.2,the only means of passing a cursor variable to a PL/SQL block is via bind variable or a procedure parameter. Can cursor variables be stored in PL/SQL tables.If yes how.If not why. No, a cursor variable points a row which cannot be stored in a two-dimensional PL/SQL table.
Difference between procedure and function.
Functions are named PL/SQL blocks that return a value and can be called with arguments procedure a named block that can be called with parameter. A procedure all is a PL/SQL statement by itself, while a Function call is called as part of an expression.
What are different modes of parameters used in functions and procedures.
IN OUT INOUT
What is difference between a formal and an actual parameter?
The variables declared in the procedure and which are passed, as arguments are called actual, the parameters in the procedure declaration. Actual parameters contain the values that are passed to a procedure and receive results. Formal parameters are the placeholders for the values of actual parameters
Can the default values be assigned to actual parameters?
Yes
Can a function take OUT parameters.If not why.
No.A function has to return a value,an OUT parameter cannot return a value.
What is syntax for dropping a procedure and a function .Are these operations possible?
Drop Procedure procedure_name Drop Function function_name
What are ORACLE PRECOMPILERS?
Using ORACLE PRECOMPILERS ,SQL statements and PL/SQL blocks can be contained inside 3GL programs written in C,C++,COBOL,PASCAL, FORTRAN,PL/1 AND ADA. The Precompilers are known as Pro*C,Pro*Cobol,… This form of PL/SQL is known as embedded pl/sql,the language in which pl/sql is embedded is known as the host language. The prcompiler translates the embedded SQL and pl/sql ststements into calls to the precompiler runtime library.The output must be compiled and linked with this library to creater an executable.
What is OCI. What are its uses?
Oracle Call Interface is a method of accesing database from a 3GL program. Uses–No precompiler is required,PL/SQL blocks are executed like other DML statements. The OCI library provides -functions to parse SQL statements -bind input variables -bind output variables -execute statements -fetch the results
Difference between database triggers and form triggers?
a) Data base trigger(DBT) fires when a DML operation is performed on a data base table.Form trigger(FT) Fires when user presses a key or navigates between fields on the screen b) Can be row level or statement level No distinction between row level and statement level. c) Can manipulate data stored in Oracle tables via SQL Can manipulate data in Oracle tables as well as variables in forms. d) Can be fired from any session executing the triggering DML statements. Can be fired only from the form that define the trigger. e) Can cause other database triggers to fire.Can cause other database triggers to fire,but not other form triggers.
C++
The problems below are not intended to teach you how to program in C++. You should not attempt
them until you believe you have mastered all the topics on the "Checklist" in the document entitled "Computer
Science C++ Exam".
The solutions for the problems are given
1. What is the output of the program below?
#include <iostream.h>
main()
{
int n = 3;
while (n >= 0)
{
cout << n * n << endl;
--n;
}
cout << n << endl;
while (n < 4)
cout << ++n << endl;
cout << n << endl;
while (n >= 0)
cout << (n /= 2) << endl;
return 0;
}
Ans:
The output would be as shown below. The program contains an endless loop.
9
4
1
0
-1
0
1
2
3
4
4
2
1
0
0 [endlessly]
2.What is the output of the program below?
#include <iostream.h>
main()
{
int n;
cout << (n = 4) << endl;
cout << (n == 4) << endl;
cout << (n > 3) << endl;
cout << (n < 4) << endl;
cout << (n = 0) << endl;
cout << (n == 0) << endl;
cout << (n > 0) << endl;
cout << (n && 4) << endl;
cout << (n || 4) << endl;
cout << (!n) << endl;
return 0;
}
Ans:
The output would be as shown below.
4
1
1
0
0
1
0
0
1
1
3.What is the output of the following program?
#include <iostream.h>
main()
{
enum color_type {red, orange, yellow, green, blue, violet};
color_type shirt, pants;
shirt = red;
pants = blue;
cout << shirt << " " << pants << endl;
return 0;
}
Ans:The output would be as shown below.
0 4
4.What is the output when the following code fragment is executed?
int i = 5, j = 6, k = 7, n = 3;
cout << i + j * k - k % n << endl;
cout << i / n << endl;
Ans:The output would be as shown below.
46
1
5.What is the output when the following code fragment is executed?
int found = 0, count = 5;
if (!found || --count == 0)
cout << "danger" << endl;
cout << "count = " << count << endl;
Ans:The output would be as shown below, because when it is discovered that "!found" is true, the second
half of the OR expression is not evaluated, and thus count is not decremented.
danger
count = 5
6.What is the output when the following code fragment is executed?
char ch;
char title[] = "Titanic";
ch = title[1];
title[3] = ch;
cout << title << endl;
cout << ch << endl;
Ans:The output would be as shown below. The 'a' in "Titanic" has been changed to an 'i'.
Titinic
i
7.Suppose that the following code fragment is executed.
const int LENGTH = 21;
char message[LENGTH];
cout << "Enter a sentence on the line below." << endl;
cin >> message;
cout << message << endl;
Suppose that in response to the prompt, the interactive user types the following line and presses Enter:
Please go away.
What will the output of the code fragment look like?
Ans:The output would be as shown below. The line in italics would be typed by the interactive user.
Enter a sentence on the line below.
Please go away.
Please
The reason that only the word "Please" is picked up in the message array is that the extraction operator >>
ignores leading white space characters and then reads non-white space characters up to the next white space
character. That is, >> is "word oriented", not line oriented.
8.Suppose that the following code fragment is executed.
const int LENGTH = 21;
char message[LENGTH];
cout << "Enter a sentence on the line below." << endl;
cin.getline(message, LENGTH, '\n');
cout << message << endl;
a. Suppose that in response to the prompt, the interactive user types the following line and presses Enter:
Please go away.
What will the output of the code fragment look like?
b. Suppose that in response to the prompt, the interactive user types the following line and presses Enter:
Please stop bothering me.
What will the output of the code fragment look like?
Ans:
a. The output would be as shown below. The line in italics would be typed by the interactive user.
Enter a sentence on the line below.
Please go away.
Please go away.
b.The output would be as shown below. The line in italics would be typed by the interactive user.
Enter a sentence on the line below.
Please stop bothering me.
Please stop botherin
The reason that the entire line typed by the user is not picked up in the message array is that the
getline instruction will read at most 20 characters from the keyboard.
9.The nested conditional statement shown below has been written by an inexperienced C/C++ programmer.
The behavior of the statement is not correctly represented by the formatting.
if (n < 10)
if (n > 0)
cout << "The number is positive." << endl;
else
cout << "The number is ______________." << endl;
a. What is the output of the statement if the variable n has the value 7 ? If n has the value 15 ?
If n has the value -3 ?
b. Correct the syntax of the statement so that the logic of the corrected statement corresponds to the
formatting of the original statement. Also, replace the blank with an appropriate word or phrase.
c. Correct the formatting of the (original) statement so that the new format reflects the logical behavior of the
original statement. Also, replace the blank with an appropriate word or phrase.
Ans: a. The original statement is formatted in such a way that it appears that the "else" clause of the statement
is the alternative to the "if (n < 10)" case, but in fact, the C or C++ compiler will treat the "else"
clause as the alternative to the "if (n > 0)" clause. If n has the value 7 , the output will be "The
number is positive". If n has the value 15 , then there will be no output. If n has the value -3
then the output will be "The number is ____________".
b. If we want the statement to behave according the logic that's suggested by the formatting of the
original statement, we can write
if (n < 10)
{
if (n > 0)
cout << "The number is positive." << endl;
}
else
cout << "The number is greater than 10." << endl;
c. If we want the statement to be formatted so as to reflect the actual logic of the original statement, we
can write
if (n < 10)
if (n > 0)
cout << "The number is positive." << endl;
else
cout << "The number is negative." << endl;
10.The loop shown below has been written by an inexperienced C/C++ programmer. The behavior of the
loop is not correctly represented by the formatting.
int n = 10;
while (n > 0)
n /= 2;
cout << n * n << endl;
a. What is the output of the loop as it is written?
b. Correct the syntax of the loop so that the logic of the corrected loop corresponds to the formatting of the
original loop. What is the output of the corrected loop?
c. Correct the formatting of the (original) loop so that the new format reflects the logical behavior of the original
loop.
Ans:
a. Since there are no braces surrounding the last two lines of the code, the compiler treats only the
statement "n /= 2;" as the body of the loop. Thus n will successively assume the values 5, 2, 1, and 0 ,
at which point the loop will exit and the "cout" statement will print 0 . The values 5, 2, and 1 will not be
printed.
b. If we want the statement to behave according the logic that's suggested by the formatting of the
original statement, we can put braces around the last two lines of code to make a compound statement as the
body of the loop:
int n = 10;
while (n > 0)
{
n /= 2;
cout << n * n << endl;
}
In this case the output of the loop will be
25
4
1
0
c. If we want the statement to be formatted so as to reflect the actual logic of the original statement, we
can write
int n = 10;
while (n > 0)
n /= 2;
cout << n * n << endl;
C Questions Output Predicting
Predict the output or error(s) for the following:
1. void main()
{
int const * p=5;
printf("%d",++(*p));
}
Answer:
Compiler error: Cannot modify a constant value.
Explanation:
p is a pointer to a "constant integer". But we tried to change the value of the "constant integer".
2. main()
{
char s[ ]="man";
int i;
for(i=0;s[ i ];i++)
printf("\n%c%c%c%c",s[ i ],*(s+i),*(i+s),i[s]);
}
Answer:
mmmm
aaaa
nnnn
Explanation:
s[i], *(i+s), *(s+i), i[s] are all different ways of expressing the same idea. Generally array name is
the base address for that array. Here s is the base address. i is the index number/displacement from the
base address. So, indirecting it with * is same as s[i]. i[s] may be surprising. But in the case of C
it is same as s[i].
3. main()
{
float me = 1.1;
double you = 1.1;
if(me==you)
printf("I love U");
else
printf("I hate U");
}
Answer:
I hate U
Explanation:
For floating point numbers (float, double, long double) the values cannot be predicted exactly. Depending
on the number of bytes, the precession with of the value represented varies. Float takes 4 bytes and long
double takes 10 bytes. So float stores 0.9 with less precision than long double.
Rule of Thumb:
Never compare or at-least be cautious when using floating point numbers with relational operators (== , >, <, <=, >=,!= ) .
4. main()
{
static int var = 5;
printf("%d ",var--);
if(var)
main();
}
Answer:
5 4 3 2 1
Explanation:
When static storage class is given, it is initialized once. The change in the value of a static variable is
retained even between the function calls. Main is also treated like any other ordinary function, which can
be called recursively.
5. main()
{
int c[ ]={2.8,3.4,4,6.7,5};
int j,*p=c,*q=c;
for(j=0;j<5;j++) {
printf(" %d ",*c);
++q; }
for(j=0;j<5;j++){
printf(" %d ",*p);
++p; }
}
Answer:
2 2 2 2 2 2 3 4 6 5
Explanation:
Initially pointer c is assigned to both p and q. In the first loop, since only q is incremented and not c ,
the value 2 will be printed 5 times. In second loop p itself is incremented. So the values 2 3 4 6 5 will be printed.
6. main()
{
extern int i;
i=20;
printf("%d",i);
}
Answer:
Linker Error : Undefined symbol '_i'
Explanation:
extern storage class in the following declaration,
extern int i;
specifies to the compiler that the memory for i is allocated in some other program and that address will be
given to the current program at the time of linking. But linker finds that no other variable of name i is
available in any other program with memory space allocated for it. Hence a linker error has occurred .
7. main()
{
int i=-1,j=-1,k=0,l=2,m;
m=i++&&j++&&k++||l++;
printf("%d %d %d %d %d",i,j,k,l,m);
}
Answer:
0 0 1 3 1
Explanation :
Logical operations always give a result of 1 or 0 . And also the logical AND (&&) operator has higher priority
over the logical OR (||) operator. So the expression ‘i++ && j++ && k++’ is executed first. The result of this
expression is 0 (-1 && -1 && 0 = 0). Now the expression is 0 || 2 which evaluates to 1 (because OR operator
always gives 1 except for ‘0 || 0’ combination- for which it gives 0). So the value of m is 1. The values of
other variables are also incremented by 1.
8. main()
{
char *p;
printf("%d %d ",sizeof(*p),sizeof(p));
}
Answer:
1 2
Explanation:
The sizeof() operator gives the number of bytes taken by its operand. P is a character pointer, which needs one
byte for storing its value (a character). Hence sizeof(*p) gives a value of 1. Since it needs two bytes to store
the address of the character pointer sizeof(p) gives 2.
9. main()
{
int i=3;
switch(i)
{
default:printf("zero");
case 1: printf("one");
break;
case 2:printf("two");
break;
case 3: printf("three");
break;
}
}
Answer :
three
Explanation :
The default case can be placed anywhere inside the loop. It is executed only when all other cases doesn't match.
10. main()
{
printf("%x",-1<<4);
}
Answer:
fff0
Explanation :
-1 is internally represented as all 1's. When left shifted four times the least significant 4 bits are filled
with 0's.The %x format specifier specifies that the integer value be printed as a hexadecimal value.
11. main()
{
char string[]="Hello World";
display(string);
}
void display(char *string)
{
printf("%s",string);
}
Answer:
Compiler Error : Type mismatch in redeclaration of function display
Explanation :
In third line, when the function display is encountered, the compiler doesn't know anything about the function
display. It assumes the arguments and return types to be integers, (which is the default type). When it sees the
actual function display, the arguments and type contradicts with what it has assumed previously. Hence a compile
time error occurs.
12. main()
{
int c=- -2;
printf("c=%d",c);
}
Answer:
c=2;
Explanation:
Here unary minus (or negation) operator is used twice. Same maths rules applies, ie. minus * minus= plus.
Note:
However you cannot give like --2. Because -- operator can only be applied to variables as a decrement operator
(eg., i--). 2 is a constant and not a variable.
13. #define int char
main()
{
int i=65;
printf("sizeof(i)=%d",sizeof(i));
}
Answer:
sizeof(i)=1
Explanation:
Since the #define replaces the string int by the macro char
14. main()
{
int i=10;
i=!i>14;
Printf ("i=%d",i);
}
Answer:
i=0
Explanation:
In the expression !i>14 , NOT (!) operator has more precedence than ‘ >’ symbol. ! is a unary logical operator.
!i (!10) is 0 (not of true is false). 0>14 is false (zero).
#include
main()
{
char s[]={'a','b','c','\n','c','\0'};
char *p,*str,*str1;
p=&s[3];
str=p;
str1=s;
printf("%d",++*p + ++*str1-32);
}
Answer:
77
Explanation:
p is pointing to character '\n'. str1 is pointing to character 'a' ++*p. "p is pointing to '\n' and that is
incremented by one." the ASCII value of '\n' is 10, which is then incremented to 11. The value of ++*p is 11.
++*str1, str1 is pointing to 'a' that is incremented by 1 and it becomes 'b'. ASCII value of 'b' is 98.
Now performing (11 + 98 – 32), we get 77("M");
So we get the output 77 :: "M" (Ascii is 77).
16. #include
main()
{
int a[2][2][2] = { {10,2,3,4}, {5,6,7,8} };
int *p,*q;
p=&a[2][2][2];
*q=***a;
printf("%d----%d",*p,*q);
}
Answer:
SomeGarbageValue---1
Explanation:
p=&a[2][2][2] you declare only two 2D arrays, but you are trying to access the third 2D(which you are not
declared) it will print garbage values. *q=***a starting address of a is assigned integer pointer. Now q
is pointing to starting address of a. If you print *q, it will print first element of 3D array.
17. #include
main()
{
struct xx
{
int x=3;
char name[]="hello";
};
struct xx *s;
printf("%d",s->x);
printf("%s",s->name);
}
Answer:
Compiler Error
Explanation:
You should not initialize variables in declaration
18. #include
main()
{
struct xx
{
int x;
struct yy
{
char s;
struct xx *p;
};
struct yy *q;
};
}
Answer:
Compiler Error
Explanation:
The structure yy is nested within structure xx. Hence, the elements are of yy are to be accessed through
the instance of structure xx, which needs an instance of yy to be known. If the instance is created after
defining the structure the compiler will not know about the instance relative to xx. Hence for nested
structure yy you have to declare member.
19. main()
{
printf("\nab");
printf("\bsi");
printf("\rha");
}
Answer:
hai
Explanation:
\n - newline
\b - backspace
\r - linefeed
20. main()
{
int i=5;
printf("%d%d%d%d%d%d",i++,i--,++i,--i,i);
}
Answer:
45545
Explanation:
The arguments in a function call are pushed into the stack from left to right. The evaluation is by
popping out from the stack. and the evaluation is from right to left, hence the result.
21. #define square(x) x*x
main()
{
int i;
i = 64/square(4);
printf("%d",i);
}
Answer:
64
Explanation:
the macro call square(4) will substituted by 4*4 so the expression becomes i = 64/4*4 . Since / and *
has equal priority the expression will be evaluated as (64/4)*4 i.e. 16*4 = 64
22. main()
{
char *p="hai friends",*p1;
p1=p;
while(*p!='\0') ++*p++;
printf("%s %s",p,p1);
}
Answer:
ibj!gsjfoet
Explanation:
++*p++ will be parse in the given order
Ø *p that is value at the location currently pointed by p will be taken
Ø ++*p the retrieved value will be incremented
Ø when ; is encountered the location will be incremented that is p++ will be executed
Hence, in the while loop initial value pointed by p is ‘h’, which is changed to ‘i’ by executing ++*p
and pointer moves to point, ‘a’ which is similarly changed to ‘b’ and so on. Similarly blank space is
converted to ‘!’. Thus, we obtain value in p becomes “ibj!gsjfoet” and since p reaches ‘\0’ and p1 points
to p thus p1doesnot print anything.
23. #include
#define a 10
main()
{
#define a 50
printf("%d",a);
}
Answer:
50
Explanation:
The preprocessor directives can be redefined anywhere in the program. So the most recently assigned value will be taken.
24. #define clrscr() 100
main()
{
clrscr();
printf("%d\n",clrscr());
}
Answer:
100
Explanation:
Preprocessor executes as a seperate pass before the execution of the compiler. So textual replacement
of clrscr() to 100 occurs.The input program to compiler looks like this :
main()
{
100;
printf("%d\n",100);
}
Note:
100; is an executable statement but with no action. So it doesn't give any problem
25. main()
{
printf("%p",main);
}
Answer:
Some address will be printed.
Explanation:
Function names are just addresses (just like array names are addresses).
main() is also a function. So the address of function main will be printed. %p in printf specifies that
the argument is an address. They are printed as hexadecimal numbers.
.NET
1. What is a static class?
2. What is static member?
3. What is static function?
4. What is static constructor?
5. How can we inherit a static variable?
6. How can we inherit a static member?
7. Can we use a static function with a non-static variable?
8. How can we access static variable?
9. Why main function is static?
10. How will you load dynamic assembly? How will create assemblies at run time?
11. What is Reflection?
12. If I have more than one version of one assembly, then how will I use old version
(how/where to specify version number?) in my application?
13. How do you create threading in.NET? What is the namespace for that?
14. What do you mean by Serialize and MarshalByRef?
15. What is the difference between Array and LinkedList?
16. What is Asynchronous call and how it can be implemented using delegates?
17. How to create events for a control? What are custom events? How to create it?
18. If you want to write your own dot net language, what steps you will you take care?
19. Describe the difference between inline and code behind - which is best in a loosely coupled solution?
20. How dot net compiled code will become platform independent?
21. Without modifying source code if we compile again, will it be generated MSIL again?
22. How does you handle this COM components developed in other programming languages in.NET?
23. How CCW (Com Callable Wrapper) and RCW (Runtime Callable Wrappers) works?
24. What are the new thee features of COM+ services, which are not there in COM (MTS)?
25. What are the differences between COM architecture and.NET architecture?
26. Can we copy a COM dll to GAC folder?
27. What is Shared and Repeatable Inheritance?
28. Can you explain what inheritance is and an example of when you might use it?
29. How can you write a class to restrict that only one object of this class can be created (Singleton class)?
30. What are virtual destructors?
31. What is close method? How its different from Finalize and Dispose?
32. What is Boxing and UnBoxing?
33. What is check/uncheck?
34. What is the use of base keyword? Tell me a practical example for base keyword’s usage?
35. What are the different.NET tools which you used in projects?
36. What will do to avoid prior case?
37. What happens when you try to update data in a dataset in.NET while the record is already
deleted in SQL Server as backend?
38. What is concurrency? How will you avoid concurrency when dealing with dataset?
39. One user deleted one row after that another user through his dataset was trying to update same row.
What will happen? How will you avoid this problem?
40. How do you merge two datasets into the third dataset in a simple manner?
41. If you are executing these statements in commandObject. “Select * from Table1; Select * from Table2″
How you will deal result set?
42. How do you sort a dataset.
43. If a dataset contains 100 rows, how to fetch rows between 5 and 15 only?
44. What is the use of Parameter object?
45. How to generateXML from a dataset and vice versa?
46. How do you implement locking concept for dataset?
47. How will you do Redo and Undo in TextBox control?
48. How to implement DataGrid in.NET? How would you make a combo-box appear in one column of a DataGrid?
What are the ways to show data grid inside a data grid for a master details type of tables? If we write any
code for DataGrid methods. what is the access specifier used for that methods in the code behind file and why?
49. How can we create Tree control in asp.NET?
50. Write a program in C# to find the angle between the hours and minutes in a clock?
51. Write a program to create a user control with name and surname as data members and login as method
and also the code to call it.
52. How can you read 3rd line from a text file?
53. Explain the code behind wors and contrast that using the inline style.
54. Explain different types of HTML, Web and server controls.
55. What are the differences between user control and server control?
56. How server form post-back works?
57. Can the action attribute of a server-side tag be set to a value and if not how can you possibly
pass data from a form page to a subsequent page?
58. How would ASP and ASP.NET apps run at the same time on the same server?
59. What are good ADO.NET object to replace to ADO Recordset object.
60. Explain the differences between Server-side code and Client-side code.
61. What type of code(server or client) is found in a Code-Behind class?
62. Should validation (did the user enter a real date) occur server-side or client-side? Why?
63. What does the “EnableViewState” property do? Why would I want it on or off?
64. What is the difference between Server.Transfer and response.Redirect? Why?
65. Can you give an example of when it would be appropriate to use a web service as opposed to
a non-serviced.NET component?
66. Let’s say I have an existing application written using VB6 and this application utilizes Windows 2000
COM+ transaction services. How would you approach migrating this application to.NET?
67. If I am developing an application that must accomodate multiple security levels though secure
login and my ASP.NET web application is spanned across three web-servers (using round-robin load balancing).
What would be the best approach to maintain login-in state for the users?
68. What are ASP.NET web forms? How is this technology different than what is available though ASP(1.0-3.0)?
69. How does VB.NET achieve polymorphism?
70. How does C# achieve polymorphism?
71. Can you explain what is Inheritance and an example in VB.NET and C# of when you might use it?
72. Describe difference between inline and code-behind?
73. What is loosely coupled solution in.NET?
74. What is diffgram?
75. Where would you use an iHTTPModule and what are the limitations of any approach you might take in implementing one?
76. What are the Advantages and DisAdvantages of viewstate?
77. Describe session handling in a webform, how does it work and what are the limitations?
78. How would you get ASP.NET running in Apache web servers? Explain it’s limitations.
79. What is MSIL and why should my developers need an appreciation of it if at all?
80. Which methos do you invoke on the DataAdapter control to load your generated dataset with data?
81. Can you edit data in Repeater control? How?
82. Which template must you provide, in order to display data in a Repeater control?
83. How can you provide an alternating color scheme in a Repeater control?
84. What property must you set, and what method must you call in your code, in order to bind the data
from some data source to the repeater control?
85. What base class do all web forms inherit from?
86. What method do you use to explicitly kill a user’s session? How?
87. How do you turn off cookies for one page in your site? Give an example.
88. Which two properties are on every validation control?
89. What tags do you need to add within the asp:datagrid tags to bind columns manually? Give an example.
90. How do you create a permanent cookie?
91. What tag do you use to add a hyperlink column to the dataGrid?
92. What is the standard you use to wrap up a call to a Web Service?
93. Which method do you use to redirect the user to another page without performing a round trip to the client? How?
94. What is the transport protocol you use to call a Seb Service SOAP?
95. What does WSDL stand for?
96. What property do you have to set to tell the grid which page to go to when using the Pager object?
97. Where on the Internet would you look for Web Services?
98. What tags do you need to add within the asp:datagrid tags to bind columns manually? How?
99. Which property on a Combo Box do you set with a column name, prior to setting the DataSource, to display data in the combo box?
100. How is a property designated as read-only?
101. Which control would you use if you needed to make sure the values in two different controls matched?
ASP.NET
1. Describe the difference between a Thread and a Process?
2. What is a Windows Service and how does its lifecycle differ from a .standard. EXE?
3. What is the maximum amount of memory any single process on Windows can address?
Is this different than the maximum virtual memory for the system? How would this affect a system design?
4. What is the difference between an EXE and a DLL?
5. What is strong-typing versus weak-typing? Which is preferred? Why?
6. What.s wrong with a line like this? DateTime.Parse(myString
7. What are PDBs? Where must they be located for debugging to work?
8. What is cyclomatic complexity and why is it important?
9. Write a standard lock() plus double check to create a critical section around a variable access.
10. What is FullTrust? Do GAC’ed assemblies have FullTrust?
11. What benefit does your code receive if you decorate it with attributes demanding specific Security permissions?
12. What does this do? gacutil /l | find /i about
13. What does this do? sn -t foo.dll
14. What ports must be open for DCOM over a firewall? What is the purpose of Port 135?
15. Contrast OOP and SOA. What are tenets of each
16. How does the XmlSerializer work? What ACL permissions does a process using it require?
17. Why is catch(Exception) almost always a bad idea?
18. What is the difference between Debug.Write and Trace.Write? When should each be used?
19. What is the difference between a Debug and Release build? Is there a significant speed difference? Why or why not?
20. Does JITting occur per-assembly or per-method? How does this affect the working set?
21. Contrast the use of an abstract base class against an interface?
22. What is the difference between a.Equals(b) and a == b?
23. In the context of a comparison, what is object identity versus object equivalence?
24. How would one do a deep copy in .NET?
25. Explain current thinking around IClonable.
26. What is boxing?
27. Is string a value type or a reference type?
28. What is the maximum length of a varchar field in SQL Server?
29. How do you define an integer in SQL Server?
30. How do you separate business logic while creating an ASP.NET application?
31. If there is a calendar control to be included in each page of your application, and
we do not intend to use the Microsoft-provided calendar control, how do you develop it?
Do you copy and paste the code into each and very page of your application?
32. How do you debug an ASP.NET application?
33. How do you deploy an ASP.NET application?
34. Name a few differences between .NET application and a Java application?
35. Specify the best ways to store variables so that we can access them in various pages of ASP.NET application?
36. What are the XML files that are important in developing an ASP.NET application?
37. What is XSLT and what is its use?
38. Can you give an example of what might be best suited to place in the application_Start and Session_Start subroutines?
39. Can you explain the difference between an ADO.NET Dataset and an ADO Recordset?
40. Can you give an example of when it would be appropriate to use a web service as opposed to a non-serviced .NET component
41. What are good ADO.NET object(s) to replace the ADO Recordset object.?
42. How would ASP and ASP.NET apps run at the same time on the same server?
43. Can the action attribute of a server-side tag be set to a value and if not how can you
possibly pass data from a form page to a subsequent page. Briefly describe the role of global.asax.
44. Briefly explain how server form post-back works (perhaps ask about view state as well).?
45. Briefly explain what user controls are and what server controls are and the differences between the two.
46. Briefly explain how the server control validation controls work.?
47. What are HTML controls, Web controls, and server controls?
48. Briefly explain how code behind works and contrast that using the inline style.?
49. How many classes can a single .NET DLL contain?
50. True or False: To test a Web service you must create a windows application or Web application to consume this service?
51. Which control would you use if you needed to make sure the values in two different controls matched?
52. How is a property designated as read-only?
53. Which property on a Combo Box do you set with a column name, prior to setting the DataSource, to display data in the combo box?
54. What tags do you need to add within the asp:datagrid tags to bind columns manually.?
55. Where on the Internet would you look for Web services?
56. the Pager object?
57. What property do you have to set to tell the grid which page to go to when using ?
58. What does WSDL stand for?
59. True or False: A Web service can only be written in .NET?
60. What is the transport protocol you use to call a Web service SOAP?
61. Which method do you use to redirect the user to another page without performing a round trip to the client?
62. What is the standard you use to wrap up a call to a Web service?
63. What tag do you use to add a hyperlink column to the DataGrid?
64. How do you create a permanent cookie?
65. What tags do you need to add within the asp:datagrid tags to bind columns manually?
66. Which two properties are on every validation control?
67. How do you turn off cookies for one page in your site?
68. Can you explain what inheritance is and an example of when you might use it?
69. What method do you use to explicitly kill a user s session?
70. What base class do all Web Forms inherit from? 71. What property must you set, and what method must you call in your code, in order to bind
the data from some data source to the Repeater control?
72. How can you provide an alternating color scheme in a Repeater control?
73. Which template must you provide, in order to display data in a Repeater control?
74. Can you edit data in the Repeater control?
75. Which method do you invoke on the DataAdapter control to load your generated dataset with data?
76. In what order do the events of an ASPX page execute. As a developer is it important to understand these events?
77. Whats MSIL, and why should my developers need an appreciation of it if at all?
78. How would you get ASP.NET running in Apache web servers - why would you even do this?
79. Describe session handling in a webfarm, how does it work and what are the limits?
80. What are the disadvantages of viewstate/what are the benefits?
81. Can you explain what inheritance is and an example of when you might use it?
82. Where would you use an iHTTPModule, and what are the limitations of any approach you might take in implementing one?
83. How would you implement inheritance using VB.NET/C#?
84. Describe the difference between inline and code behind - which is best in a loosely coupled solution.
85. Whats an assembly ..?
86. How would you implement inheritance using VB.NET/C#?
87. How does VB.NET/C# achieve polymorphism?
88. Can you give an example of what might be best suited to place in the Application Start and Session Start subroutines?
89. Can you explain the difference between an ADO.NET Dataset and an ADO Recordset?
90. Can you give an example of when it would be appropriate to use a web service as opposed to a non-serviced .NET component
91. What is the difference between Servers? Transfer and Response. Redirect? Why would I choose one over the other?
92. What does the "EnableViewState" property do? Why would I want it on or off?
93. Should validation (did the user enter a real date) occur server-side or client-side? Why?
94. What type of code (server or client) is found in a Code-Behind class?
95. Explain the differences between Server-side and Client-side code?
Subscribe to:
Comments (Atom)







