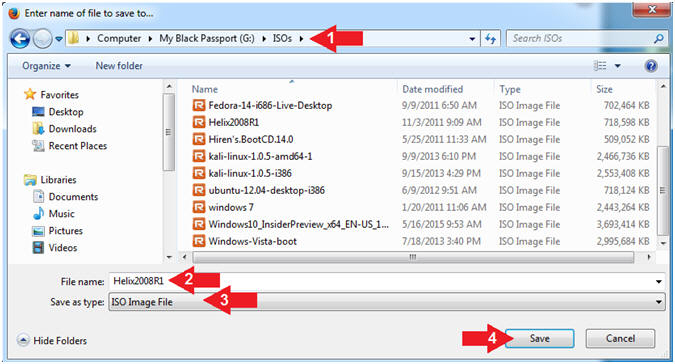
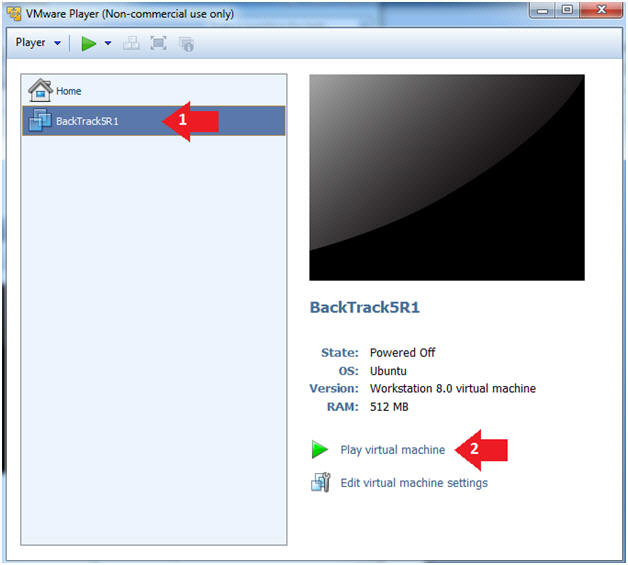
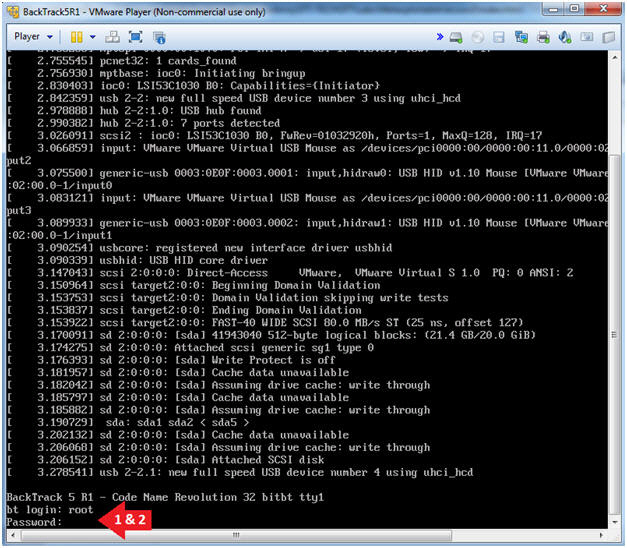
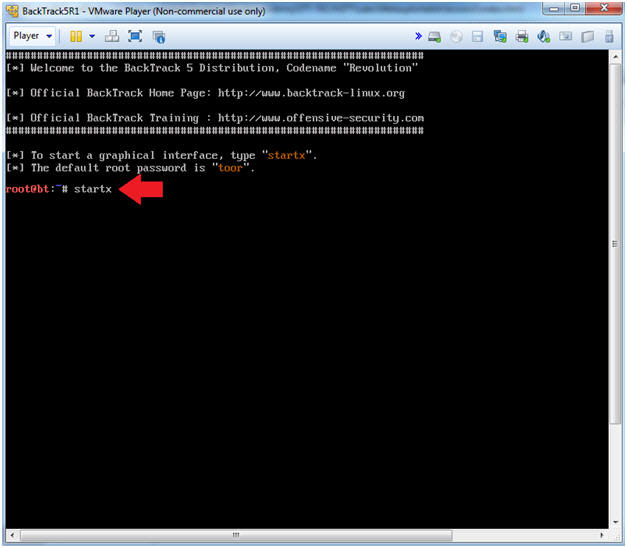
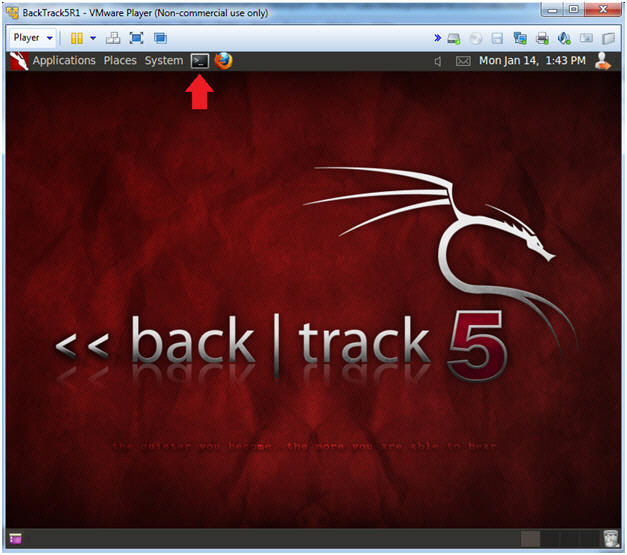
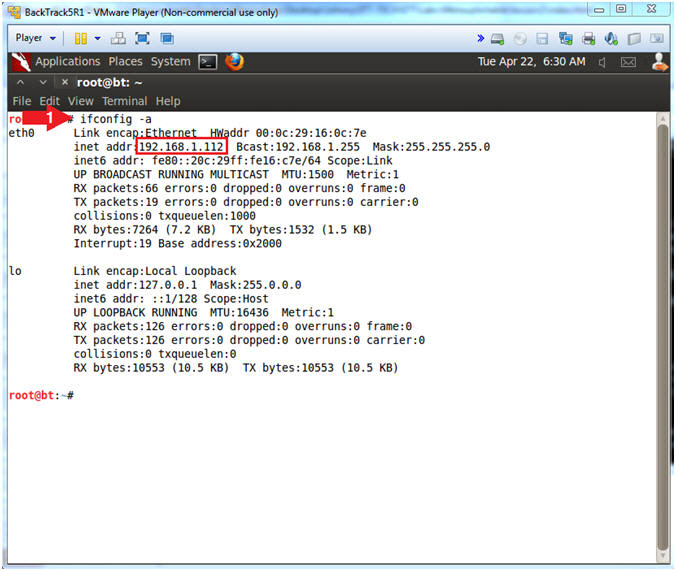
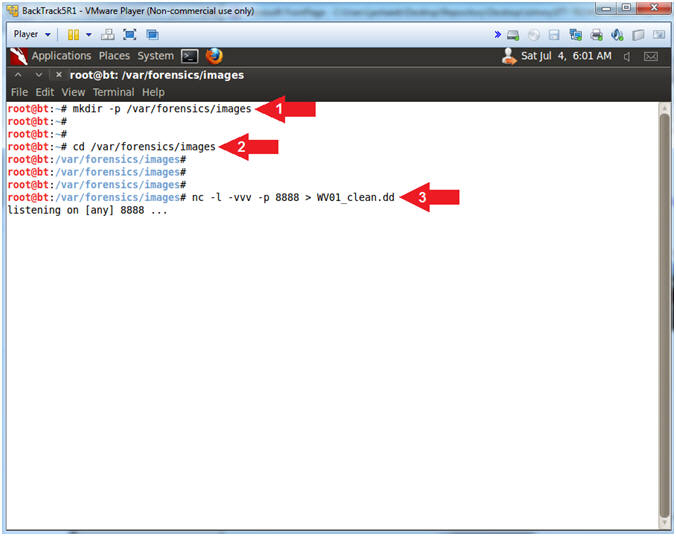
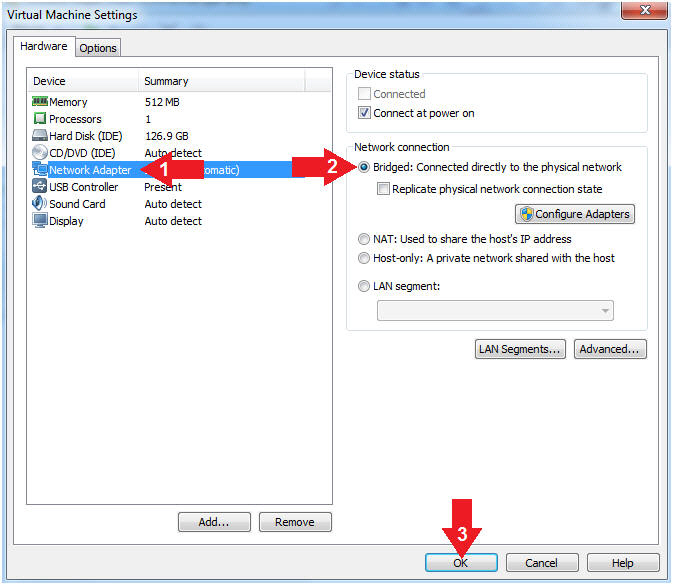
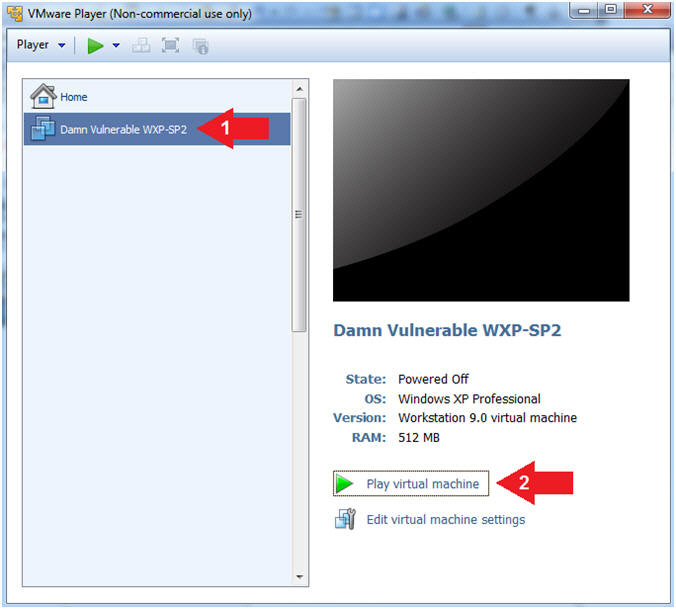
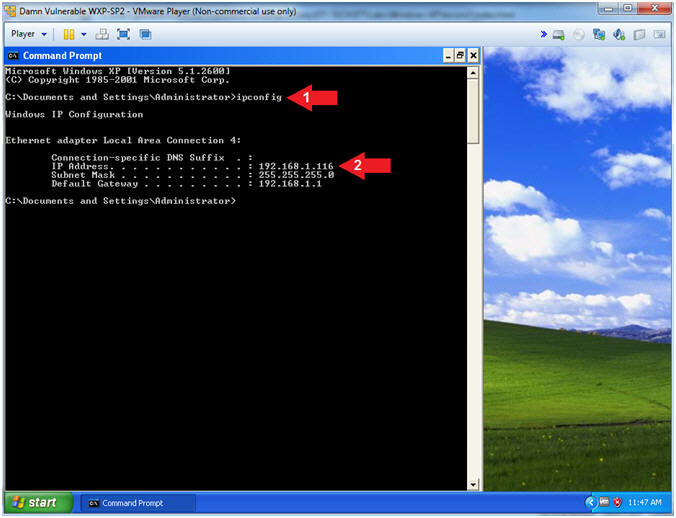
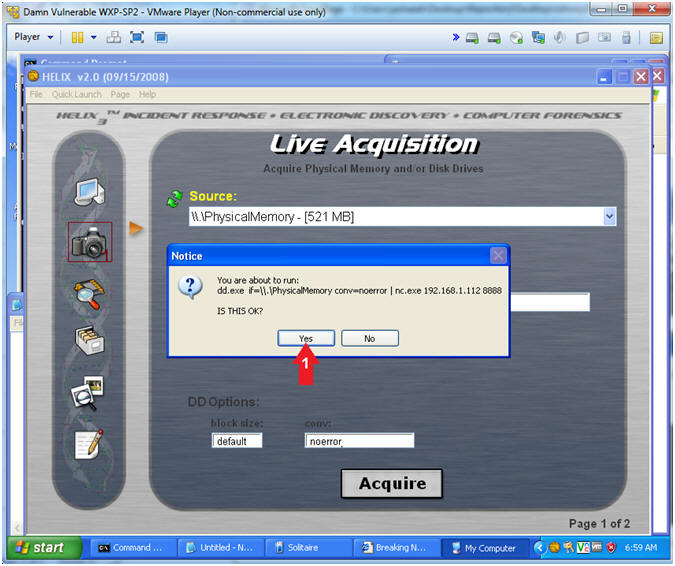
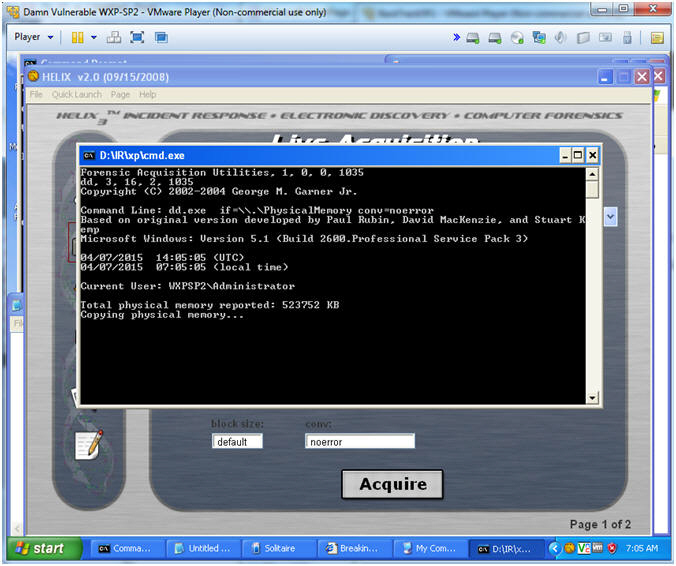
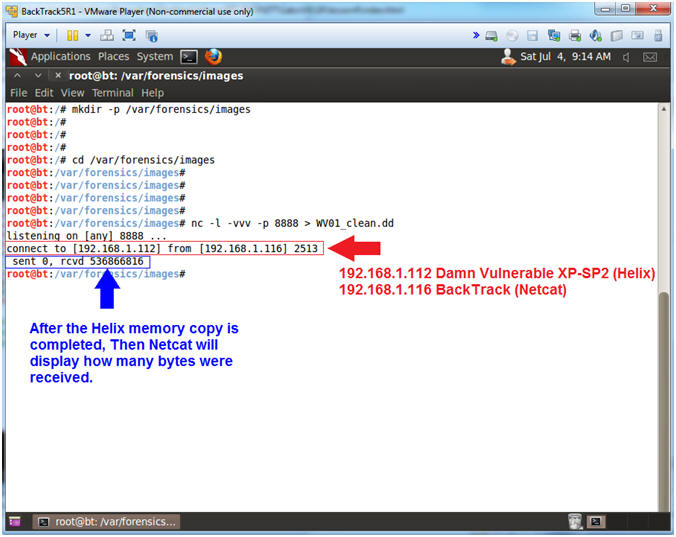
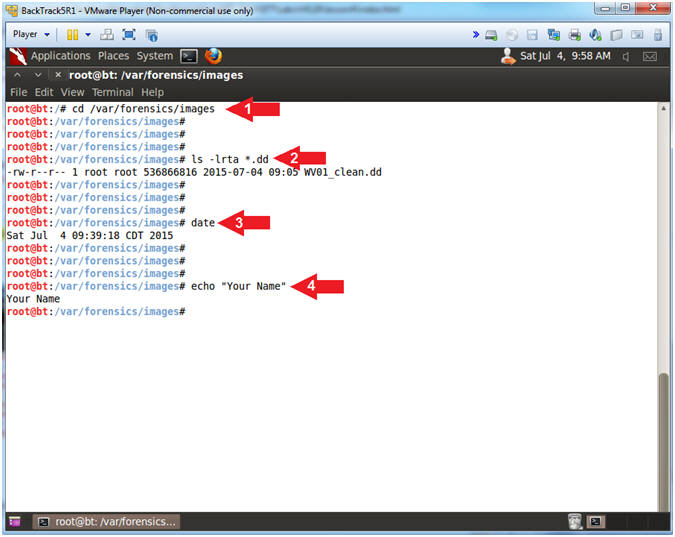
//PROGRAM FOR DISTANCE VECTOR ROUTING ALGORITHM
#include<stdio.h>
#include<conio.h>
struct node
{
unsigned dist[20];
unsigned from[20];
}rt[10];
int main()
{
int dmat[20][20];
int n,i,j,k,count=0;
printf("\nEnter number of nodes : ");
scanf("%d",&n);
printf("\nEnter the cost matrix :\n");
for(i=0;i<n;i++)
for(j=0;j<n;j++)
{
scanf("%d",&dmat[i][j]);
dmat[i][i]=0;
rt[i].dist[j]=dmat[i][j];
rt[i].from[j]=j;
}
do
{
count=0;
for(i=0;i<n;i++)
for(j=0;j<n;j++)
for(k=0;k<n;k++)
if(rt[i].dist[j]>dmat[i][k]+rt[k].dist[j])
{
rt[i].dist[j]=rt[i].dist[k]+rt[k].dist[j];
rt[i].from[j]=k;
count++;
}
}while(count!=0);
for(i=0;i<n;i++)
{
printf("\n\nNODE %d ROUTING TABLE",i+1);
printf("\nNode\tDistance\tViaNode\n");
for(j=0;j<n;j++)
{
printf("\t\n %d\t %d\t\t %d",j+1,rt[i].dist[j],rt[i].from[j]+1);
}
}
printf("\n\n");
return 0;
getch();
}
/*SAMPLE OUTPUT
**********INPUT*********
Enter number of nodes : 5
Enter the cost matrix :
0 4 2 6 99
4 0 99 99 99
2 99 0 3 99
6 99 3 0 2
99 99 99 2 0

::::::OUTPUT :::::
NODE 1 ROUTING TABLE
Node Distance ViaNode
1 0 1
2 4 2
3 2 3
4 5 3
5 7 4
NODE 2 ROUTING TABLE
Node Distance ViaNode
1 4 1
2 0 2
3 6 1
4 9 1
5 11 1
NODE 3 ROUTING TABLE
Node Distance ViaNode
1 2 1
2 6 1
3 0 3
4 3 4
5 5 4
NODE 4 ROUTING TABLE
Node Distance ViaNode
1 5 3
2 9 1
3 3 3
4 0 4
5 2 5
NODE 5 ROUTING TABLE
Node Distance ViaNode
1 7 4
2 11 4
3 5 4
4 2 4
5 0 5
//RSA ALGORITHM
#include <stdio.h>
int modulo(int e, int n, int pt)
{
int h;
if(e==0)
return 1;
else if(e==1)
return pt%n;
else
{
h = modulo(e/2, n, pt);
if(e%2==0)
return ((h*h)%n)%n;
else
return ((h*h)*(pt%n))%n;
}
}
int main()
{
int p, q, n, z, e, d, pt,ct;
printf("Enter p & q values <prime numbers>: ");
scanf("%d%d", &p, &q);
n = p*q;
z = (p-1)*(q-1);
printf("\nEnter a relative prime number to %d i.e., e value: ",z);
scanf("%d", &e);
d = 1;
while((d*e)%z!=1)
d++;
printf("d value is: %d\n", d);
printf("Keys are: <e, n>:(%d, %d)\t<d, n>:(%d, %d)",e,n,d,n);
printf("\n\nEnter message<pt> such that pt < %d : ",n);
scanf("%d", &pt);
ct = modulo(e,n,pt);
printf("\nCipher Text: %d\n",ct);
pt = modulo(d,n,ct);
printf("Decrypted Text: %d",pt);
return 0;
}
/* SAMPLE OUTPUT
Enter p & q values <prime numbers>: 11 7
Enter a relative prime number to 60 i.e., e value: 13
d value is: 37
Keys are: <e, n>:(13, 77) <d, n>:(37, 77)
Enter message<pt> such that pt < 77 : 5
Cipher Text: 26
Decrypted Text: 5
*/