Money saving tips while Shopping Online using BuyHatke
2 IIT Kharagpur students, Gaurav Dahake and Prashant Singh, in the last regard to their course in 2013 were taking a look at a couple of e-commerce websites to get an iPod for their pal's birthday. However it had not been a comfy experience. The more they surfed the more they were at a loss.
Various websites revealed various rates, price cuts and shipment time. There was no chance of quickly deciding. Lastly, they bought one, just to find out later on that the item would take five days to show up, well after the birthday. They likewise understood that when they positioned the order, they were not knowledgeable about another website which provided the item Rs 300 less. The experience set the two thinking on the requirement turn digital shopping into a problem-free experience.
Explains Dahake, "It's challenging to discover the very best offer while going shopping online. We felt every purchaser ought to have the ability to understand all the e-commerce websites that provided the item and the costs they provided."
Shopping website Buyhatke has actually re-launched a cool chrome extension that assists you discover the least expensive rates for products that you are wanting to get. The extension offers you costs from over 45 Indian e-commerce websites.
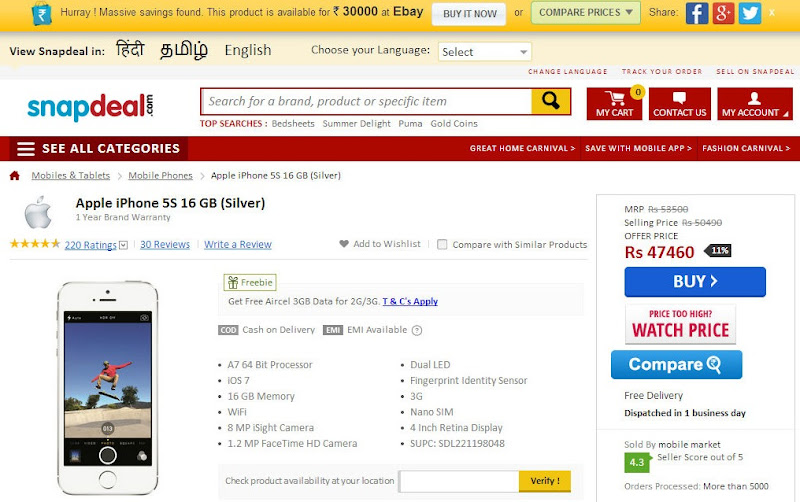
After you set up the extension to your Chrome browser, it stays up until you get to an item page on a shopping website. When you end up on an item page, it provides you a button to compare rates of the item throughout internet sites.If you do not wish to leave the page, you can click the extension on the leading right of the page and a list of costs appear. It likewise immediately compares costs and informs you if the item is being sold at a lower price somewhere else.
Chrome extensions for price contrast is a cool idea that has actually ended up being style just recently. This conserves users the problem of clicking through to a website to compare costs and boosts your possibilities of uncovering a much better price on a product.
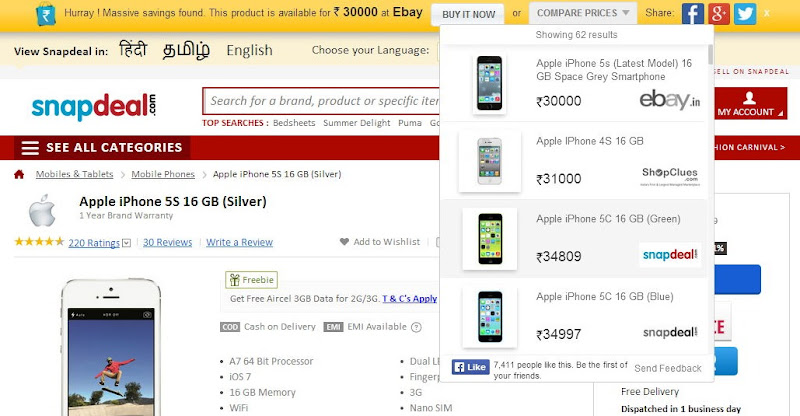
We discovered the extension rather helpful and stylish. Nevertheless, it often gets puzzled in between items. For instance, when we were on Flipkart trying to find a Seagate 1 TB disk drive, it recommended that the exact same item is readily available for less costly on the website. On closer appearance, it ended up that the less expensive price was for a 500 GB drive by the exact same producer.It might be a great idea to thoroughly filter information from websites like eBay that likewise offer pre-owned products.
There are lots of shopping services that have actually turned up in India as e-commerce gets. For e-commerce business, discount coupons and online shopping websites reduce expense of obtaining a client. Nevertheless, it likewise puts prices pressure on products. As seeing in comScore's most current report on India, online shopping is among the fastest growing internet classifications in the nation.
So overall I think it's a must have extension if you are really into the online shopping addiction, this would help you in saving tons of money even I faced a huge loss after purchasing SSD from Flipkart as its was available for approximately Rs.800 less on SnapDeal, so make sure you compare prices online before actually purchasing anything.
Various websites revealed various rates, price cuts and shipment time. There was no chance of quickly deciding. Lastly, they bought one, just to find out later on that the item would take five days to show up, well after the birthday. They likewise understood that when they positioned the order, they were not knowledgeable about another website which provided the item Rs 300 less. The experience set the two thinking on the requirement turn digital shopping into a problem-free experience.
Explains Dahake, "It's challenging to discover the very best offer while going shopping online. We felt every purchaser ought to have the ability to understand all the e-commerce websites that provided the item and the costs they provided."
Shopping website Buyhatke has actually re-launched a cool chrome extension that assists you discover the least expensive rates for products that you are wanting to get. The extension offers you costs from over 45 Indian e-commerce websites.

After you set up the extension to your Chrome browser, it stays up until you get to an item page on a shopping website. When you end up on an item page, it provides you a button to compare rates of the item throughout internet sites.If you do not wish to leave the page, you can click the extension on the leading right of the page and a list of costs appear. It likewise immediately compares costs and informs you if the item is being sold at a lower price somewhere else.
Chrome extensions for price contrast is a cool idea that has actually ended up being style just recently. This conserves users the problem of clicking through to a website to compare costs and boosts your possibilities of uncovering a much better price on a product.

We discovered the extension rather helpful and stylish. Nevertheless, it often gets puzzled in between items. For instance, when we were on Flipkart trying to find a Seagate 1 TB disk drive, it recommended that the exact same item is readily available for less costly on the website. On closer appearance, it ended up that the less expensive price was for a 500 GB drive by the exact same producer.It might be a great idea to thoroughly filter information from websites like eBay that likewise offer pre-owned products.
There are lots of shopping services that have actually turned up in India as e-commerce gets. For e-commerce business, discount coupons and online shopping websites reduce expense of obtaining a client. Nevertheless, it likewise puts prices pressure on products. As seeing in comScore's most current report on India, online shopping is among the fastest growing internet classifications in the nation.
So overall I think it's a must have extension if you are really into the online shopping addiction, this would help you in saving tons of money even I faced a huge loss after purchasing SSD from Flipkart as its was available for approximately Rs.800 less on SnapDeal, so make sure you compare prices online before actually purchasing anything.
